- 1Java基础--Stream流
- 2Java~在maven项目中添加junit依赖实现单元测试(@After、@Before 、@Ignore、@Test)的使用_maven java @test 依赖
- 3Vue项目中关于全局css的处理_var(--el-color-primary)
- 4pytorch复现lenet5模型,并检测自己手写的数字图片_pytorch读取自己的手写数字数据集
- 5【大厂AI课学习笔记NO.54】2.3深度学习开发任务实例(7)数据标注和数据集拆分_深度学习数据集标注
- 6NeRF必读:Mip-NeRF总结与公式推导_mipnerf
- 7红米AX6000刷openwrt
- 8python 使用GDAL实现栅格tif转矢量shp_tif转shp的展示效果
- 9pandas按条件筛选数据_ilocation based boolean indexing cannot use an ind
- 10安装thinkphp6并使用多应用模式,解决提示路由不存在解决办法_thinkphp6 多模块路由 控制器不存在
【 Linux学习】SSH连接时出现Host key verification failed的原因及解决方法以及ssh-keygen命令的用法_host key verification failed.
赞
踩
一、问题描述
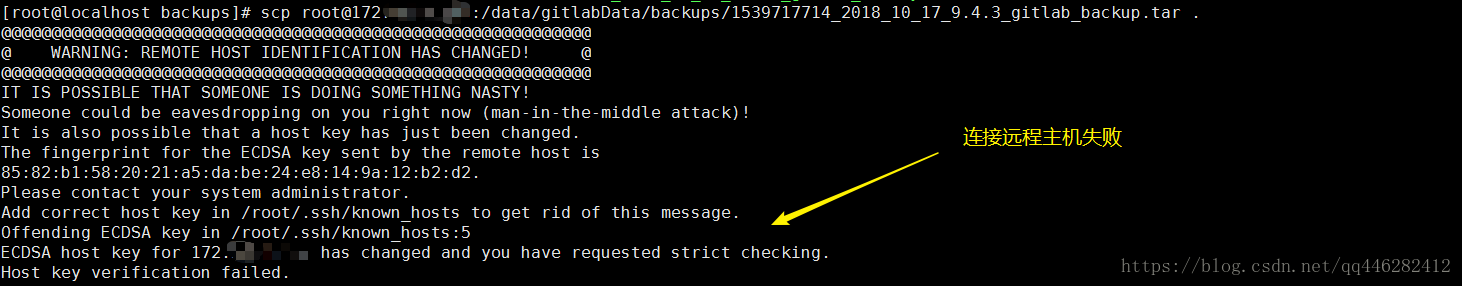
今天下午使用ssh连接其他服务器进行scp操作的时候,提示失败,如下所示:
[root@localhost backups]# scp root@172.xxx.xxx.xxx:/data/gitlabData/backups/1539717714_2018_10_17_9.4.3_gitlab_backup.tar .
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY!
Someone could be eavesdropping on you right now (man-in-the-middle attack)!
It is also possible that a host key has just been changed.
The fingerprint for the ECDSA key sent by the remote host is
85:82:b1:58:20:21:a5:da:be:24:e8:14:9a:12:b2:d2.
Please contact your system administrator.
Add correct host key in /root/.ssh/known_hosts to get rid of this message.
Offending ECDSA key in /root/.ssh/known_hosts:5
ECDSA host key for 172.xxx.xxx.xxx has changed and you have requested strict checking.
Host key verification failed.
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
二、分析原因
用OpenSSH的人都知ssh会把你每个你访问过计算机的公钥(public key)都记录在~/.ssh/known_hosts。当下次访问相同计算机时,OpenSSH会核对公钥。如果公钥不同,OpenSSH会发出警告,避免你受到DNS Hijack之类的攻击。
SSH对主机的public_key的检查等级是根据StrictHostKeyChecking变量来配置的。默认情况下,StrictHostKeyChecking=ask。
简单说下它的三种配置值:
- StrictHostKeyChecking=no
最不安全的级别,当然也没有那么多烦人的提示了,相对安全的内网时建议使用。如果连接server的key在本地不存在,那么就自动添加到文件中(默认是known_hosts),并且给出一个警告。
- StrictHostKeyChecking=ask
默认的级别,就是出现刚才的提示了。如果连接和key不匹配,给出提示,并拒绝登录。
- StrictHostKeyChecking=yes
最安全的级别,如果连接与key不匹配,就拒绝连接,不会提示详细信息。
三、解决问题
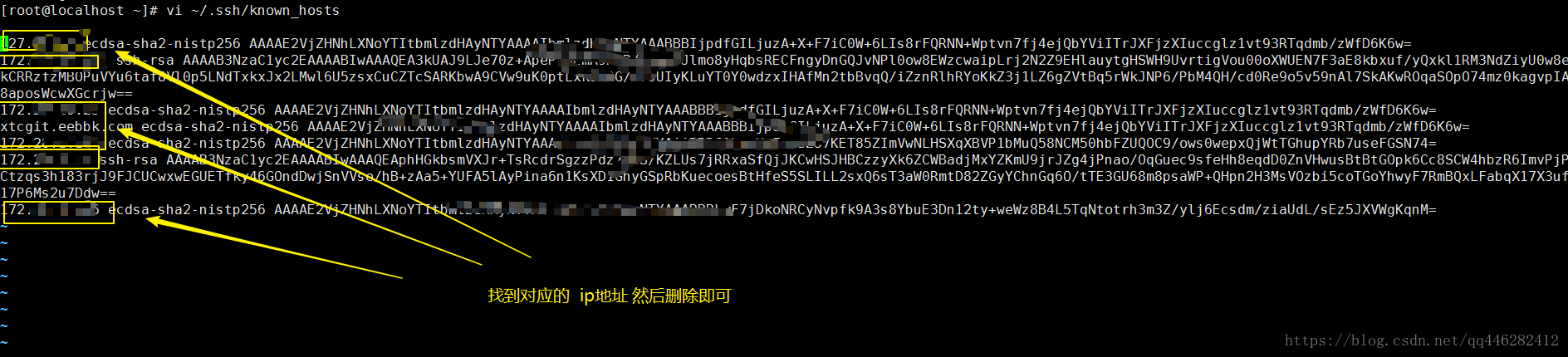
方法一、删除~/.ssh/known_hosts文件中对应ip的相关rsa信息
输入命令vi ~/.ssh/known_hosts ,编辑文件
删除对应ip的相关rsa信息,即可。
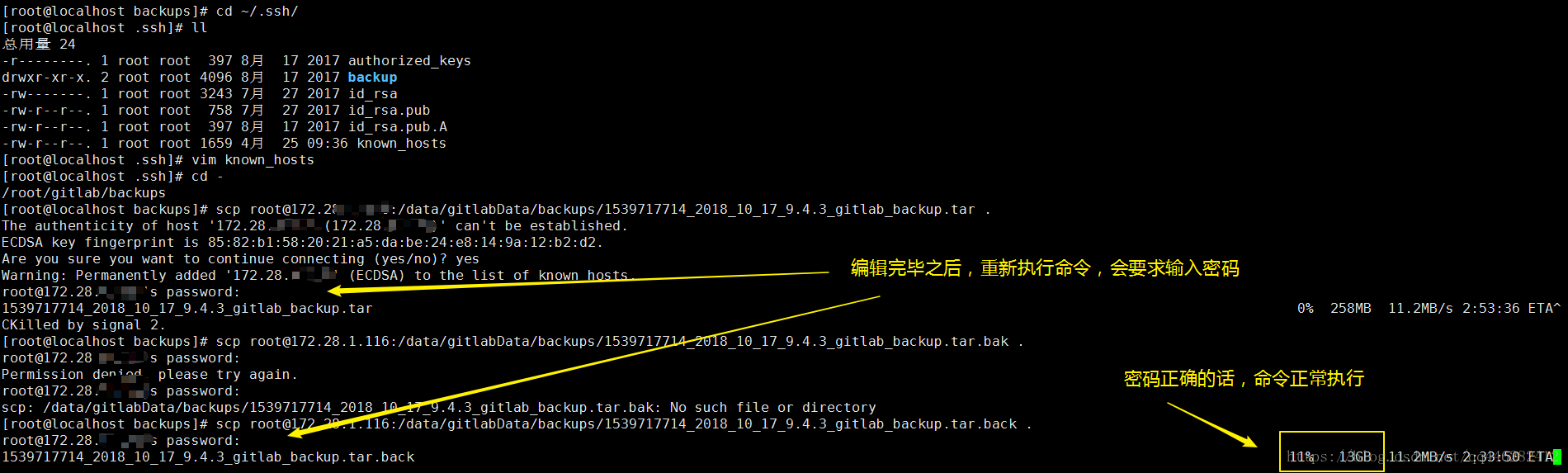
删除完毕之后,重新执行命令,会要求输入密码。
密码正确的话,命令正常执行。
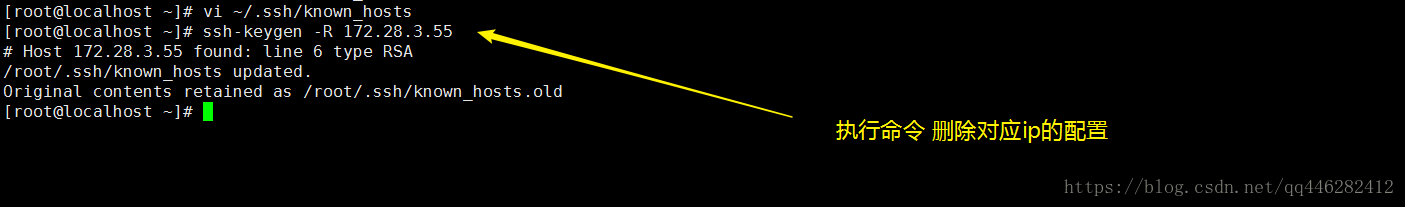
方法二、 使用 ssh-keygen -R hostname 命令
ssh-keygen -R xxx.xxx.xxx.xxx (服务器ip地址)
目的是清除你当前机器里关于你的远程服务器的缓存和公钥信息,注意是大写的字母“R”。
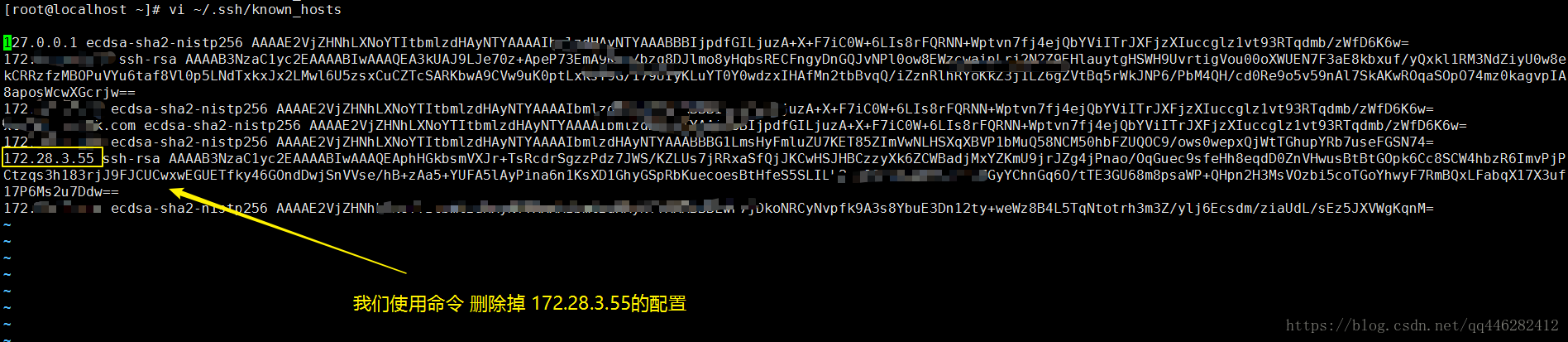
比如 ~/.ssh/known_hosts文件中有一条 172.28.3.55 的配置。
现在我们执行ssh-keygen -R hostname命令
[root@localhost ~]# vi ~/.ssh/known_hosts
[root@localhost ~]# ssh-keygen -R 172.28.3.55
# Host 172.28.3.55 found: line 6 type RSA
/root/.ssh/known_hosts updated.
Original contents retained as /root/.ssh/known_hosts.old
[root@localhost ~]#
- 1
- 2
- 3
- 4
- 5
- 6
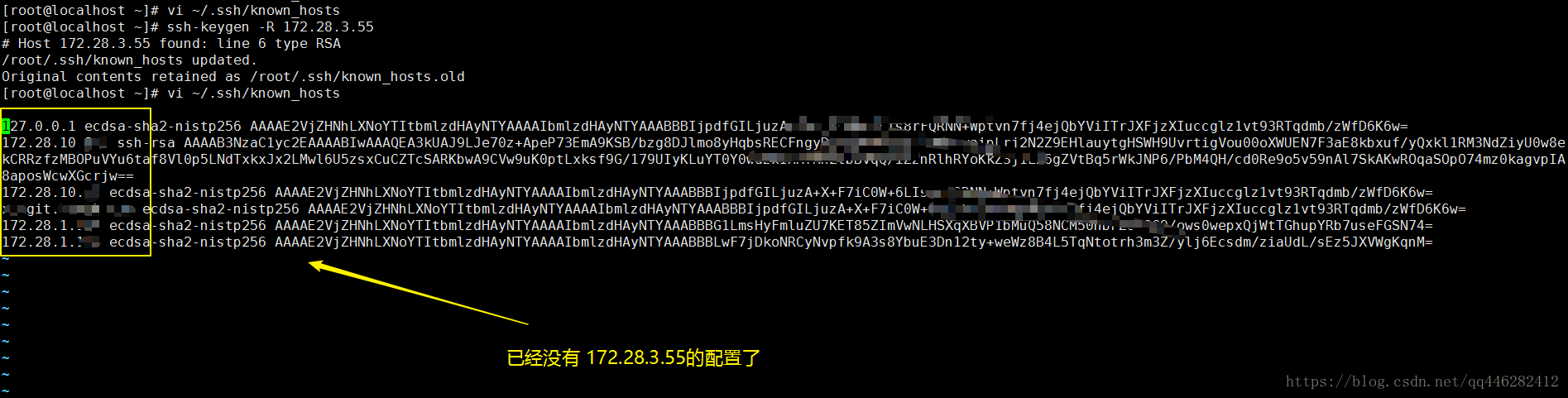
我们再查看下 ~/.ssh/known_hosts文件的内容,如下所示:
删除完配置之后,重新执行命令,输入命令然后输入密码即可。
如果想以后都不输入密码直接执行命令的话,则需要参考链接 https://blog.csdn.net/ouyang_peng/article/details/77334215 然后重新配置ssh秘钥,然后再执行命令。
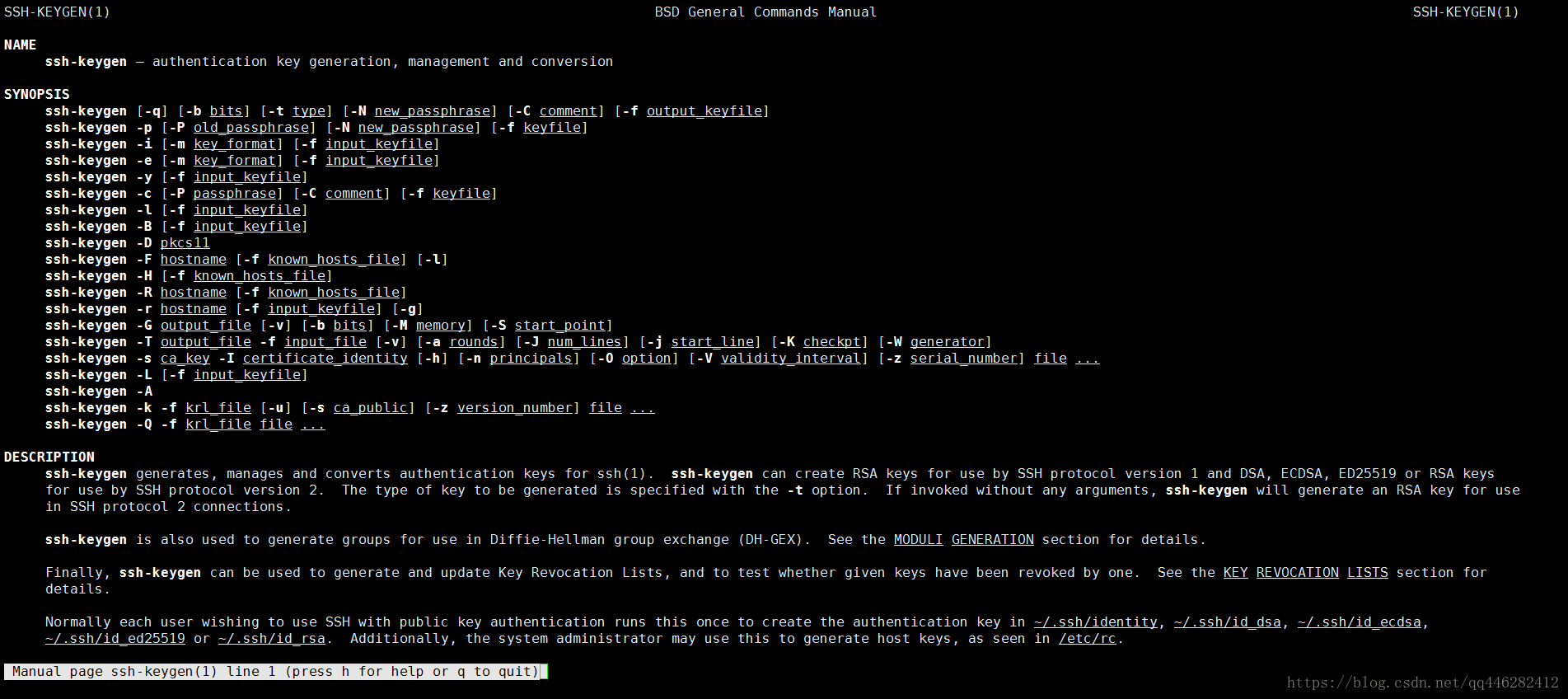
四、讲解下ssh-keygen命令
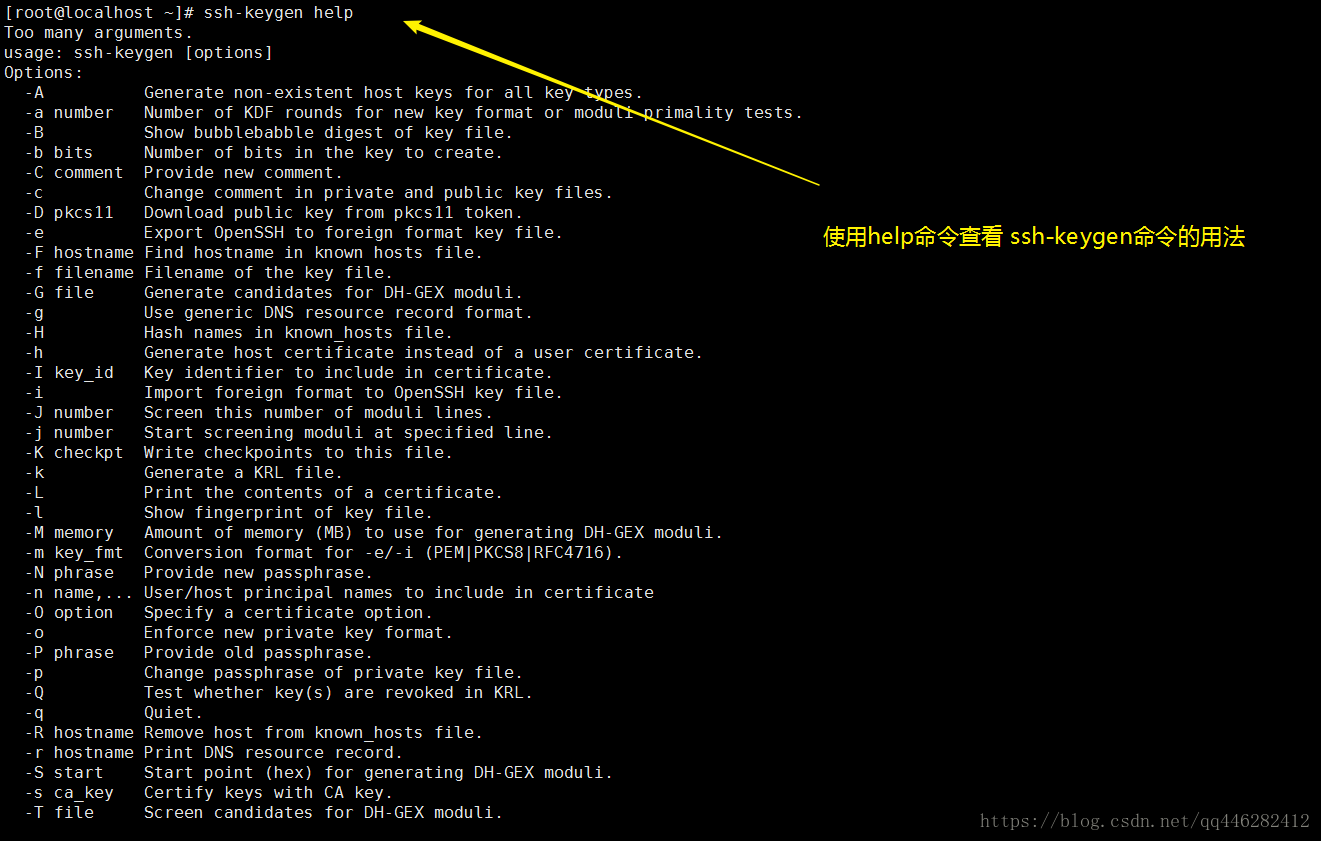
使用help命令查看下ssh-keygen命令的用法,如下所示:
[root@localhost ~]# ssh-keygen help
Too many arguments.
usage: ssh-keygen [options]
Options:
-A Generate non-existent host keys for all key types.
-a number Number of KDF rounds for new key format or moduli primality tests.
-B Show bubblebabble digest of key file.
-b bits Number of bits in the key to create.
-C comment Provide new comment.
-c Change comment in private and public key files.
-D pkcs11 Download public key from pkcs11 token.
-e Export OpenSSH to foreign format key file.
-F hostname Find hostname in known hosts file.
-f filename Filename of the key file.
-G file Generate candidates for DH-GEX moduli.
-g Use generic DNS resource record format.
-H Hash names in known_hosts file.
-h Generate host certificate instead of a user certificate.
-I key_id Key identifier to include in certificate.
-i Import foreign format to OpenSSH key file.
-J number Screen this number of moduli lines.
-j number Start screening moduli at specified line.
-K checkpt Write checkpoints to this file.
-k Generate a KRL file.
-L Print the contents of a certificate.
-l Show fingerprint of key file.
-M memory Amount of memory (MB) to use for generating DH-GEX moduli.
-m key_fmt Conversion format for -e/-i (PEM|PKCS8|RFC4716).
-N phrase Provide new passphrase.
-n name,... User/host principal names to include in certificate
-O option Specify a certificate option.
-o Enforce new private key format.
-P phrase Provide old passphrase.
-p Change passphrase of private key file.
-Q Test whether key(s) are revoked in KRL.
-q Quiet.
-R hostname Remove host from known_hosts file.
-r hostname Print DNS resource record.
-S start Start point (hex) for generating DH-GEX moduli.
-s ca_key Certify keys with CA key.
-T file Screen candidates for DH-GEX moduli.
-t type Specify type of key to create.
-u Update KRL rather than creating a new one.
-V from:to Specify certificate validity interval.
-v Verbose.
-W gen Generator to use for generating DH-GEX moduli.
-y Read private key file and print public key.
-Z cipher Specify a cipher for new private key format.
-z serial Specify a serial number.
[root@localhost ~]#
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
使用man命令查看下ssh-keygen命令的详细用法,如下所示:
SSH-KEYGEN(1) BSD General Commands Manual SSH-KEYGEN(1)
NAME
ssh-keygen — authentication key generation, management and conversion
SYNOPSIS
ssh-keygen [-q] [-b bits] [-t type] [-N new_passphrase] [-C comment] [-f output_keyfile]
ssh-keygen -p [-P old_passphrase] [-N new_passphrase] [-f keyfile]
ssh-keygen -i [-m key_format] [-f input_keyfile]
ssh-keygen -e [-m key_format] [-f input_keyfile]
ssh-keygen -y [-f input_keyfile]
ssh-keygen -c [-P passphrase] [-C comment] [-f keyfile]
ssh-keygen -l [-f input_keyfile]
ssh-keygen -B [-f input_keyfile]
ssh-keygen -D pkcs11
ssh-keygen -F hostname [-f known_hosts_file] [-l]
ssh-keygen -H [-f known_hosts_file]
ssh-keygen -R hostname [-f known_hosts_file]
ssh-keygen -r hostname [-f input_keyfile] [-g]
ssh-keygen -G output_file [-v] [-b bits] [-M memory] [-S start_point]
ssh-keygen -T output_file -f input_file [-v] [-a rounds] [-J num_lines] [-j start_line] [-K checkpt] [-W generator]
ssh-keygen -s ca_key -I certificate_identity [-h] [-n principals] [-O option] [-V validity_interval] [-z serial_number] file ...
ssh-keygen -L [-f input_keyfile]
ssh-keygen -A
ssh-keygen -k -f krl_file [-u] [-s ca_public] [-z version_number] file ...
ssh-keygen -Q -f krl_file file ...
DESCRIPTION
ssh-keygen generates, manages and converts authentication keys for ssh(1). ssh-keygen can create RSA keys for use by SSH protocol version 1 and DSA, ECDSA, ED25519 or RSA keys
for use by SSH protocol version 2. The type of key to be generated is specified with the -t option. If invoked without any arguments, ssh-keygen will generate an RSA key for use
in SSH protocol 2 connections.
ssh-keygen is also used to generate groups for use in Diffie-Hellman group exchange (DH-GEX). See the MODULI GENERATION section for details.
Finally, ssh-keygen can be used to generate and update Key Revocation Lists, and to test whether given keys have been revoked by one. See the KEY REVOCATION LISTS section for
details.
Normally each user wishing to use SSH with public key authentication runs this once to create the authentication key in ~/.ssh/identity, ~/.ssh/id_dsa, ~/.ssh/id_ecdsa,
~/.ssh/id_ed25519 or ~/.ssh/id_rsa. Additionally, the system administrator may use this to generate host keys, as seen in /etc/rc.
Normally this program generates the key and asks for a file in which to store the private key. The public key is stored in a file with the same name but “.pub” appended. The
program also asks for a passphrase. The passphrase may be empty to indicate no passphrase (host keys must have an empty passphrase), or it may be a string of arbitrary length. A
passphrase is similar to a password, except it can be a phrase with a series of words, punctuation, numbers, whitespace, or any string of characters you want. Good passphrases
are 10-30 characters long, are not simple sentences or otherwise easily guessable (English prose has only 1-2 bits of entropy per character, and provides very bad passphrases),
and contain a mix of upper and lowercase letters, numbers, and non-alphanumeric characters. The passphrase can be changed later by using the -p option.
There is no way to recover a lost passphrase. If the passphrase is lost or forgotten, a new key must be generated and the corresponding public key copied to other machines.
For RSA1 keys, there is also a comment field in the key file that is only for convenience to the user to help identify the key. The comment can tell what the key is for, or what‐
ever is useful. The comment is initialized to “user@host” when the key is created, but can be changed using the -c option.
After a key is generated, instructions below detail where the keys should be placed to be activated.
The options are as follows:
-A For each of the key types (rsa1, rsa, dsa, ecdsa and ed25519) for which host keys do not exist, generate the host keys with the default key file path, an empty passphrase,
default bits for the key type, and default comment. This is used by /etc/rc to generate new host keys.
-a rounds
When saving a new-format private key (i.e. an ed25519 key or any SSH protocol 2 key when the -o flag is set), this option specifies the number of KDF (key derivation func‐
tion) rounds used. Higher numbers result in slower passphrase verification and increased resistance to brute-force password cracking (should the keys be stolen).
When screening DH-GEX candidates ( using the -T command). This option specifies the number of primality tests to perform.
-B Show the bubblebabble digest of specified private or public key file.
-b bits
Specifies the number of bits in the key to create. For RSA keys, the minimum size is 768 bits and the default is 2048 bits. Generally, 2048 bits is considered suffi‐
cient. DSA keys must be exactly 1024 bits as specified by FIPS 186-2. For ECDSA keys, the -b flag determines the key length by selecting from one of three elliptic curve
sizes: 256, 384 or 521 bits. Attempting to use bit lengths other than these three values for ECDSA keys will fail. ED25519 keys have a fixed length and the -b flag will
be ignored.
-C comment
Provides a new comment.
-c Requests changing the comment in the private and public key files. This operation is only supported for RSA1 keys. The program will prompt for the file containing the
private keys, for the passphrase if the key has one, and for the new comment.
-D pkcs11
Download the RSA public keys provided by the PKCS#11 shared library pkcs11. When used in combination with -s, this option indicates that a CA key resides in a PKCS#11
token (see the CERTIFICATES section for details).
-e This option will read a private or public OpenSSH key file and print to stdout the key in one of the formats specified by the -m option. The default export format is
“RFC4716”. This option allows exporting OpenSSH keys for use by other programs, including several commercial SSH implementations.
-F hostname
Search for the specified hostname in a known_hosts file, listing any occurrences found. This option is useful to find hashed host names or addresses and may also be used
in conjunction with the -H option to print found keys in a hashed format.
-f filename
Specifies the filename of the key file.
-G output_file
Generate candidate primes for DH-GEX. These primes must be screened for safety (using the -T option) before use.
-g Use generic DNS format when printing fingerprint resource records using the -r command.
-H Hash a known_hosts file. This replaces all hostnames and addresses with hashed representations within the specified file; the original content is moved to a file with a
.old suffix. These hashes may be used normally by ssh and sshd, but they do not reveal identifying information should the file's contents be disclosed. This option will
not modify existing hashed hostnames and is therefore safe to use on files that mix hashed and non-hashed names.
-h When signing a key, create a host certificate instead of a user certificate. Please see the CERTIFICATES section for details.
-I certificate_identity
Specify the key identity when signing a public key. Please see the CERTIFICATES section for details.
-i This option will read an unencrypted private (or public) key file in the format specified by the -m option and print an OpenSSH compatible private (or public) key to std‐
out.
-J num_lines
Exit after screening the specified number of lines while performing DH candidate screening using the -T option.
-j start_line
Start screening at the specified line number while performing DH candidate screening using the -T option.
-K checkpt
Write the last line processed to the file checkpt while performing DH candidate screening using the -T option. This will be used to skip lines in the input file that have
already been processed if the job is restarted. This option allows importing keys from other software, including several commercial SSH implementations. The default
import format is “RFC4716”.
-k Generate a KRL file. In this mode, ssh-keygen will generate a KRL file at the location specified via the -f flag that revokes every key or certificate presented on the
command line. Keys/certificates to be revoked may be specified by public key file or using the format described in the KEY REVOCATION LISTS section.
-L Prints the contents of a certificate.
-l Show fingerprint of specified public key file. Private RSA1 keys are also supported. For RSA and DSA keys ssh-keygen tries to find the matching public key file and
prints its fingerprint. If combined with -v, an ASCII art representation of the key is supplied with the fingerprint.
-M memory
Specify the amount of memory to use (in megabytes) when generating candidate moduli for DH-GEX.
-m key_format
Specify a key format for the -i (import) or -e (export) conversion options. The supported key formats are: “RFC4716” (RFC 4716/SSH2 public or private key), “PKCS8” (PEM
PKCS8 public key) or “PEM” (PEM public key). The default conversion format is “RFC4716”.
-N new_passphrase
Provides the new passphrase.
-n principals
Specify one or more principals (user or host names) to be included in a certificate when signing a key. Multiple principals may be specified, separated by commas. Please
see the CERTIFICATES section for details.
-O option
Specify a certificate option when signing a key. This option may be specified multiple times. Please see the CERTIFICATES section for details. The options that are
valid for user certificates are:
clear Clear all enabled permissions. This is useful for clearing the default set of permissions so permissions may be added individually.
force-command=command
Forces the execution of command instead of any shell or command specified by the user when the certificate is used for authentication.
no-agent-forwarding
Disable ssh-agent(1) forwarding (permitted by default).
no-port-forwarding
Disable port forwarding (permitted by default).
no-pty Disable PTY allocation (permitted by default).
no-user-rc
Disable execution of ~/.ssh/rc by sshd(8) (permitted by default).
no-x11-forwarding
Disable X11 forwarding (permitted by default).
permit-agent-forwarding
Allows ssh-agent(1) forwarding.
permit-port-forwarding
Allows port forwarding.
permit-pty
Allows PTY allocation.
permit-user-rc
Allows execution of ~/.ssh/rc by sshd(8).
permit-x11-forwarding
Allows X11 forwarding.
source-address=address_list
Restrict the source addresses from which the certificate is considered valid. The address_list is a comma-separated list of one or more address/netmask pairs in
CIDR format.
At present, no options are valid for host keys.
-o Causes ssh-keygen to save SSH protocol 2 private keys using the new OpenSSH format rather than the more compatible PEM format. The new format has increased resistance to
brute-force password cracking but is not supported by versions of OpenSSH prior to 6.5. Ed25519 keys always use the new private key format.
-P passphrase
Provides the (old) passphrase.
-p Requests changing the passphrase of a private key file instead of creating a new private key. The program will prompt for the file containing the private key, for the old
passphrase, and twice for the new passphrase.
-Q Test whether keys have been revoked in a KRL.
-q Silence ssh-keygen.
-R hostname
Removes all keys belonging to hostname from a known_hosts file. This option is useful to delete hashed hosts (see the -H option above).
-r hostname
Print the SSHFP fingerprint resource record named hostname for the specified public key file.
-S start
Specify start point (in hex) when generating candidate moduli for DH-GEX.
-s ca_key
Certify (sign) a public key using the specified CA key. Please see the CERTIFICATES section for details.
When generating a KRL, -s specifies a path to a CA public key file used to revoke certificates directly by key ID or serial number. See the KEY REVOCATION LISTS section
for details.
-T output_file
Test DH group exchange candidate primes (generated using the -G option) for safety.
-t type
Specifies the type of key to create. The possible values are “rsa1” for protocol version 1 and “dsa”, “ecdsa”, “ed25519”, or “rsa” for protocol version 2.
-u Update a KRL. When specified with -k, keys listed via the command line are added to the existing KRL rather than a new KRL being created.
-V validity_interval
Specify a validity interval when signing a certificate. A validity interval may consist of a single time, indicating that the certificate is valid beginning now and
expiring at that time, or may consist of two times separated by a colon to indicate an explicit time interval. The start time may be specified as a date in YYYYMMDD for‐
mat, a time in YYYYMMDDHHMMSS format or a relative time (to the current time) consisting of a minus sign followed by a relative time in the format described in the TIME
FORMATS section of sshd_config(5). The end time may be specified as a YYYYMMDD date, a YYYYMMDDHHMMSS time or a relative time starting with a plus character.
For example: “+52w1d” (valid from now to 52 weeks and one day from now), “-4w:+4w” (valid from four weeks ago to four weeks from now), “20100101123000:20110101123000”
(valid from 12:30 PM, January 1st, 2010 to 12:30 PM, January 1st, 2011), “-1d:20110101” (valid from yesterday to midnight, January 1st, 2011).
-v Verbose mode. Causes ssh-keygen to print debugging messages about its progress. This is helpful for debugging moduli generation. Multiple -v options increase the ver‐
bosity. The maximum is 3.
-W generator
Specify desired generator when testing candidate moduli for DH-GEX.
-y This option will read a private OpenSSH format file and print an OpenSSH public key to stdout.
-z serial_number
Specifies a serial number to be embedded in the certificate to distinguish this certificate from others from the same CA. The default serial number is zero.
When generating a KRL, the -z flag is used to specify a KRL version number.
MODULI GENERATION
ssh-keygen may be used to generate groups for the Diffie-Hellman Group Exchange (DH-GEX) protocol. Generating these groups is a two-step process: first, candidate primes are gen‐
erated using a fast, but memory intensive process. These candidate primes are then tested for suitability (a CPU-intensive process).
Generation of primes is performed using the -G option. The desired length of the primes may be specified by the -b option. For example:
# ssh-keygen -G moduli-2048.candidates -b 2048
By default, the search for primes begins at a random point in the desired length range. This may be overridden using the -S option, which specifies a different start point (in
hex).
Once a set of candidates have been generated, they must be screened for suitability. This may be performed using the -T option. In this mode ssh-keygen will read candidates from
standard input (or a file specified using the -f option). For example:
# ssh-keygen -T moduli-2048 -f moduli-2048.candidates
By default, each candidate will be subjected to 100 primality tests. This may be overridden using the -a option. The DH generator value will be chosen automatically for the
prime under consideration. If a specific generator is desired, it may be requested using the -W option. Valid generator values are 2, 3, and 5.
Screened DH groups may be installed in /etc/ssh/moduli. It is important that this file contains moduli of a range of bit lengths and that both ends of a connection share common
moduli.
CERTIFICATES
ssh-keygen supports signing of keys to produce certificates that may be used for user or host authentication. Certificates consist of a public key, some identity information,
zero or more principal (user or host) names and a set of options that are signed by a Certification Authority (CA) key. Clients or servers may then trust only the CA key and ver‐
ify its signature on a certificate rather than trusting many user/host keys. Note that OpenSSH certificates are a different, and much simpler, format to the X.509 certificates
used in ssl(8).
ssh-keygen supports two types of certificates: user and host. User certificates authenticate users to servers, whereas host certificates authenticate server hosts to users. To
generate a user certificate:
$ ssh-keygen -s /path/to/ca_key -I key_id /path/to/user_key.pub
The resultant certificate will be placed in /path/to/user_key-cert.pub. A host certificate requires the -h option:
$ ssh-keygen -s /path/to/ca_key -I key_id -h /path/to/host_key.pub
The host certificate will be output to /path/to/host_key-cert.pub.
It is possible to sign using a CA key stored in a PKCS#11 token by providing the token library using -D and identifying the CA key by providing its public half as an argument to
-s:
$ ssh-keygen -s ca_key.pub -D libpkcs11.so -I key_id host_key.pub
In all cases, key_id is a "key identifier" that is logged by the server when the certificate is used for authentication.
Certificates may be limited to be valid for a set of principal (user/host) names. By default, generated certificates are valid for all users or hosts. To generate a certificate
for a specified set of principals:
$ ssh-keygen -s ca_key -I key_id -n user1,user2 user_key.pub
$ ssh-keygen -s ca_key -I key_id -h -n host.domain user_key.pub
Additional limitations on the validity and use of user certificates may be specified through certificate options. A certificate option may disable features of the SSH session,
may be valid only when presented from particular source addresses or may force the use of a specific command. For a list of valid certificate options, see the documentation for
the -O option above.
Finally, certificates may be defined with a validity lifetime. The -V option allows specification of certificate start and end times. A certificate that is presented at a time
outside this range will not be considered valid. By default, certificates are valid from UNIX Epoch to the distant future.
For certificates to be used for user or host authentication, the CA public key must be trusted by sshd(8) or ssh(1). Please refer to those manual pages for details.
KEY REVOCATION LISTS
ssh-keygen is able to manage OpenSSH format Key Revocation Lists (KRLs). These binary files specify keys or certificates to be revoked using a compact format, taking as little as
one bit per certificate if they are being revoked by serial number.
KRLs may be generated using the -k flag. This option reads one or more files from the command line and generates a new KRL. The files may either contain a KRL specification (see
below) or public keys, listed one per line. Plain public keys are revoked by listing their hash or contents in the KRL and certificates revoked by serial number or key ID (if the
serial is zero or not available).
Revoking keys using a KRL specification offers explicit control over the types of record used to revoke keys and may be used to directly revoke certificates by serial number or
key ID without having the complete original certificate on hand. A KRL specification consists of lines containing one of the following directives followed by a colon and some
directive-specific information.
serial: serial_number[-serial_number]
Revokes a certificate with the specified serial number. Serial numbers are 64-bit values, not including zero and may be expressed in decimal, hex or octal. If two serial
numbers are specified separated by a hyphen, then the range of serial numbers including and between each is revoked. The CA key must have been specified on the ssh-keygen
command line using the -s option.
id: key_id
Revokes a certificate with the specified key ID string. The CA key must have been specified on the ssh-keygen command line using the -s option.
key: public_key
Revokes the specified key. If a certificate is listed, then it is revoked as a plain public key.
sha1: public_key
Revokes the specified key by its SHA1 hash.
KRLs may be updated using the -u flag in addition to -k. When this option is specified, keys listed via the command line are merged into the KRL, adding to those already there.
It is also possible, given a KRL, to test whether it revokes a particular key (or keys). The -Q flag will query an existing KRL, testing each key specified on the commandline.
If any key listed on the command line has been revoked (or an error encountered) then ssh-keygen will exit with a non-zero exit status. A zero exit status will only be returned
if no key was revoked.
FILES
~/.ssh/identity
Contains the protocol version 1 RSA authentication identity of the user. This file should not be readable by anyone but the user. It is possible to specify a passphrase
when generating the key; that passphrase will be used to encrypt the private part of this file using 3DES. This file is not automatically accessed by ssh-keygen but it is
offered as the default file for the private key. ssh(1) will read this file when a login attempt is made.
~/.ssh/identity.pub
Contains the protocol version 1 RSA public key for authentication. The contents of this file should be added to ~/.ssh/authorized_keys on all machines where the user
wishes to log in using RSA authentication. There is no need to keep the contents of this file secret.
~/.ssh/id_dsa
~/.ssh/id_ecdsa
~/.ssh/id_ed25519
~/.ssh/id_rsa
Contains the protocol version 2 DSA, ECDSA, ED25519 or RSA authentication identity of the user. This file should not be readable by anyone but the user. It is possible
to specify a passphrase when generating the key; that passphrase will be used to encrypt the private part of this file using 128-bit AES. This file is not automatically
accessed by ssh-keygen but it is offered as the default file for the private key. ssh(1) will read this file when a login attempt is made.
~/.ssh/id_dsa.pub
~/.ssh/id_ecdsa.pub
~/.ssh/id_ed25519.pub
~/.ssh/id_rsa.pub
Contains the protocol version 2 DSA, ECDSA, ED25519 or RSA public key for authentication. The contents of this file should be added to ~/.ssh/authorized_keys on all
machines where the user wishes to log in using public key authentication. There is no need to keep the contents of this file secret.
/etc/ssh/moduli
Contains Diffie-Hellman groups used for DH-GEX. The file format is described in moduli(5).
ENVIRONMENT
SSH_USE_STRONG_RNG
The reseeding of the OpenSSL random generator is usually done from /dev/urandom. If the SSH_USE_STRONG_RNG environment variable is set to value other than 0 the OpenSSL
random generator is reseeded from /dev/random. The number of bytes read is defined by the SSH_USE_STRONG_RNG value. Minimum is 14 bytes. This setting is not recommended
on the computers without the hardware random generator because insufficient entropy causes the connection to be blocked until enough entropy is available.
SEE ALSO
ssh(1), ssh-add(1), ssh-agent(1), moduli(5), sshd(8)
The Secure Shell (SSH) Public Key File Format, RFC 4716, 2006.
AUTHORS
OpenSSH is a derivative of the original and free ssh 1.2.12 release by Tatu Ylonen. Aaron Campbell, Bob Beck, Markus Friedl, Niels Provos, Theo de Raadt and Dug Song removed many
bugs, re-added newer features and created OpenSSH. Markus Friedl contributed the support for SSH protocol versions 1.5 and 2.0.
BSD October 17, 2018 BSD
Manual page ssh-keygen(1) line 342/381 (END) (press h for help or q to quit)
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
- 76
- 77
- 78
- 79
- 80
- 81
- 82
- 83
- 84
- 85
- 86
- 87
- 88
- 89
- 90
- 91
- 92
- 93
- 94
- 95
- 96
- 97
- 98
- 99
- 100
- 101
- 102
- 103
- 104
- 105
- 106
- 107
- 108
- 109
- 110
- 111
- 112
- 113
- 114
- 115
- 116
- 117
- 118
- 119
- 120
- 121
- 122
- 123
- 124
- 125
- 126
- 127
- 128
- 129
- 130
- 131
- 132
- 133
- 134
- 135
- 136
- 137
- 138
- 139
- 140
- 141
- 142
- 143
- 144
- 145
- 146
- 147
- 148
- 149
- 150
- 151
- 152
- 153
- 154
- 155
- 156
- 157
- 158
- 159
- 160
- 161
- 162
- 163
- 164
- 165
- 166
- 167
- 168
- 169
- 170
- 171
- 172
- 173
- 174
- 175
- 176
- 177
- 178
- 179
- 180
- 181
- 182
- 183
- 184
- 185
- 186
- 187
- 188
- 189
- 190
- 191
- 192
- 193
- 194
- 195
- 196
- 197
- 198
- 199
- 200
- 201
- 202
- 203
- 204
- 205
- 206
- 207
- 208
- 209
- 210
- 211
- 212
- 213
- 214
- 215
- 216
- 217
- 218
- 219
- 220
- 221
- 222
- 223
- 224
- 225
- 226
- 227
- 228
- 229
- 230
- 231
- 232
- 233
- 234
- 235
- 236
- 237
- 238
- 239
- 240
- 241
- 242
- 243
- 244
- 245
- 246
- 247
- 248
- 249
- 250
- 251
- 252
- 253
- 254
- 255
- 256
- 257
- 258
- 259
- 260
- 261
- 262
- 263
- 264
- 265
- 266
- 267
- 268
- 269
- 270
- 271
- 272
- 273
- 274
- 275
- 276
- 277
- 278
- 279
- 280
- 281
- 282
- 283
- 284
- 285
- 286
- 287
- 288
- 289
- 290
- 291
- 292
- 293
- 294
- 295
- 296
- 297
- 298
- 299
- 300
- 301
- 302
- 303
- 304
- 305
- 306
- 307
- 308
- 309
- 310
- 311
- 312
- 313
- 314
- 315
- 316
- 317
- 318
- 319
- 320
- 321
- 322
- 323
- 324
- 325
- 326
- 327
- 328
- 329
- 330
- 331
- 332
- 333
- 334
- 335
- 336
- 337
- 338
- 339
- 340
- 341
- 342
- 343
- 344
- 345
- 346
- 347
- 348
- 349
- 350
- 351
- 352
- 353
- 354
- 355
- 356
- 357
- 358
- 359
- 360
- 361
- 362
- 363
- 364
- 365
- 366
- 367
- 368
- 369
- 370
- 371
- 372
- 373
- 374
- 375
- 376
- 377
- 378
- 379
- 380
- 381
- 382
- 383
下面讲解下刚才的指导说明书,大致翻译如下所示
SSH-KEYGEN(1)BSD通用命令手册SSH-KEYGEN(1)
名字
ssh-keygen - 认证密钥生成、管理和转换
概要
ssh-keygen [-q] [-b bits] [-t type] [-N new_passphrase] [-C comment] [-f output_keyfile]
ssh-keygen -p [-P old_passphrase] [-N new_passphrase] [-f keyfile]
ssh-keygen -i [-m key_format] [-f input_keyfile]
ssh-keygen -e [-m key_format] [-f input_keyfile]
ssh-keygen -y [-f input_keyfile]
ssh-keygen -c [-P passphrase] [-C comment] [-f keyfile]
ssh-keygen -l [-f input_keyfile]
ssh-keygen -B [-f input_keyfile]
ssh-keygen -D pkcs11
ssh-keygen -F hostname [-f known_hosts_file] [-l]
ssh-keygen -H [-f known_hosts_file]
ssh-keygen -R hostname [-f known_hosts_file]
ssh-keygen -r hostname [-f input_keyfile] [-g]
ssh-keygen -G output_file [-v] [-b bits] [-M memory] [-S start_point]
ssh-keygen -T output_file -f input_file [-v] [-a rounds] [-J num_lines] [-j start_line] [-K checkpt] [-W generator]
ssh-keygen -s ca_key -I certificate_identity [-h] [-n principalals] [-O option] [-V validity_interval] [-z serial_number] file ...
ssh-keygen -L [-f input_keyfile]
ssh-keygen -A
ssh-keygen -k -f krl_file [-u] [-s ca_public] [-z version_number]文件...
ssh-keygen -Q -f krl_file文件...
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
描述
ssh-keygen生成,管理和转换ssh(1)的身份验证密钥。 ssh-keygen可以创建RSA密钥,供SSH协议版本1和DSA,ECDSA,ED25519或RSA密钥使用
供SSH协议版本2使用。要生成的密钥类型使用-t选项指定。如果在没有任何参数的情况下调用,ssh-keygen将生成一个RSA密钥以供使用在SSH协议2连接。
ssh-keygen还用于生成用于Diffie-Hellman组交换(DH-GEX)的组。有关详细信息,请参阅MODULI GENERATION部分。
最后,ssh-keygen可用于生成和更新密钥撤销列表,并测试给定密钥是否已被一个撤销。请参阅KEY REVOCATION LISTS部分细节。
通常,每个希望使用SSH和公钥认证的用户运行一次以在〜/ .ssh / identity,〜/ .ssh / id_dsa,〜/ .ssh / id_ecdsa中创建认证密钥,
〜/ .ssh / id_ed25519或〜/ .ssh / id_rsa。此外,系统管理员可以使用它来生成主机密钥,如/ etc / rc中所示。
通常,该程序生成密钥并请求存储私钥的文件。公钥存储在具有相同名称但附加“.pub”的文件中。该程序还要求密码。密码短语可以为空以表示没有密码短语(主机密钥必须具有空密码短语),或者它可以是任意长度的字符串。一个密码类似于密码,除了它可以是包含一系列单词,标点符号,数字,空格或任何所需字符串的短语。好的密码是10-30个字符长,不是简单的句子或其他容易猜测(英文散文每个字符只有1-2位熵,并提供非常糟糕的密码短语),并包含大写和小写字母,数字和非字母数字字符的混合。稍后可以使用-p选项更改密码。
没有办法恢复丢失的密码短语。如果密码丢失或遗忘,则必须生成新密钥并将相应的公钥复制到其他计算机。
对于RSA1密钥,密钥文件中还有一个注释字段,仅为方便用户帮助识别密钥。 评论可以告诉关键字是什么,或者什么是有用的。 创建密钥时,注释将初始化为“user @ host”,但可以使用-c选项进行更改。
生成密钥后,下面的说明详细说明了应该激活密钥的位置。
选项如下:
-
-A
对于不存在主机密钥的每种密钥类型(rsa1,rsa,dsa,ecdsa和ed25519),使用默认密钥文件路径(空密码,生成密码)生成主机密钥,密钥类型的默认位和默认注释。 / etc / rc使用它来生成新的主机密钥。 -
-a rounds
保存新格式的私钥(即设置-o标志时的ed25519密钥或任何SSH协议2密钥)时,此选项指定使用的KDF(密钥派生函数)轮次数。 数字越大,密码短语验证越慢,并且对强力密码破解的抵抗力越强(如果密钥被盗)。
筛选DH-GEX候选者时(使用-T命令)。 此选项指定要执行的素性测试的数量。
-
-B
显示指定的私钥或公钥文件的bubblebabble摘要。 -
-b bits
指定要创建的键中的位数。 对于RSA密钥,最小大小为768位,默认值为2048位。 通常,2048位被认为是足够的。 DSA密钥必须是FIPS 186-2指定的1024位。 对于ECDSA密钥,-b标志通过从三个椭圆曲线中的一个中选择来确定密钥长度大小:256,384或521位。 尝试对ECDSA密钥使用除这三个值之外的位长度将失败。 ED25519键具有固定长度,-b标志将具有被忽略 -
-C comment
提供新评论。 -
-c
请求更改私钥和公钥文件中的注释。 此操作仅支持RSA1密钥。 程序将提示输入包含的文件私钥,密钥(如果密钥有密码)和新评论。 -
-D pkcs11
下载PKCS#11共享库pkcs11提供的RSA公钥。 与-s结合使用时,此选项表示CA密钥驻留在PKCS#11中令牌(有关详细信息,请参阅证书部分)。 -
-e
此选项将读取私有或公共OpenSSH密钥文件,并以-m选项指定的格式之一打印到stdout密钥。 默认导出格式为
“采用RFC4716”。 此选项允许导出OpenSSH密钥以供其他程序使用,包括几个商业SSH实现。 -
-F hostname
在known_hosts文件中搜索指定的主机名,列出找到的所有匹配项。 此选项对于查找散列主机名或地址很有用,也可以使用与-H选项结合使用,以散列格式打印找到的键。 -
-f filename
指定密钥文件的文件名。 -
-G output_file
为DH-GEX生成候选素数。 在使用之前,必须对这些质数进行筛选以确保安全性(使用-T选项)。 -
-g
使用-r命令打印指纹资源记录时使用通用DNS格式。 -
-H
哈希一个known_hosts文件。 这将替换指定文件中具有散列表示的所有主机名和地址; 将原始内容移动到带有的文件 .old后缀。 这些哈希值通常可以由ssh和sshd使用,但如果文件的内容被公开,它们不会显示识别信息。 这个选项会不修改现有的散列主机名,因此可以安全地用于混合散列和非散列名称的文件。 -
-h
签名密钥时,请创建主机证书而不是用户证书。有关详细信息,请参阅证书部分。 -
-I certificate_identity
在签署公钥时指定密钥标识。有关详细信息,请参阅证书部分。 -
-i
此选项将以-m选项指定的格式读取未加密的私有(或公共)密钥文件,并将与OpenSSH兼容的私有(或公共)密钥打印到stdout。 -
-J num_lines
在使用-T选项执行DH候选筛选时筛选指定数量的行后退出。 -
-j start_line
使用-T选项在执行DH候选筛选时,以指定的行号开始筛选。 -
-K检查
在使用-T选项执行DH候选筛选时,将处理的最后一行写入文件checkpt。 这将用于跳过输入文件中已重新启动作业时已处理的行。 此选项允许从其他软件导入密钥,包括几个商业SSH实现。 默认值导入格式为“RFC4716”。 -
-k
生成KRL文件。 在此模式下,ssh-keygen将在通过-f标志指定的位置生成KRL文件,该文件将撤消命令行上显示的每个密钥或证书。 要撤销的密钥/证书可以通过公钥文件或使用KEY REVOCATION LISTS部分中描述的格式来指定。 -
-L
打印证书的内容。 -
-l
显示指定公钥文件的指纹。还支持专用RSA1密钥。对于RSA和DSA密钥,ssh-keygen尝试查找匹配的公钥文件和
打印其指纹。如果与-v结合使用,则随指纹提供密钥的ASCII艺术表示。 -
-M memory
在为DH-GEX生成候选模数时,指定要使用的内存量(以兆字节为单位)。 -
-m key_format
指定-i(导入)或-e(导出)转换选项的密钥格式。支持的密钥格式为:“RFC4716”(RFC 4716 / SSH2公钥或私钥),“PKCS8”(PEM)PKCS8公钥)或“PEM”(PEM公钥)。默认转换格式为“RFC4716”。 -
-N new_passphrase
提供新密码。 -
-n principals
签署密钥时,指定要包含在证书中的一个或多个主体(用户名或主机名)。可以指定多个主体,用逗号分隔。请有关详细信息,请参阅CERTIFICATES部分。 -
-O option
签署密钥时指定证书选项。可以多次指定此选项。有关详细信息,请参阅证书部分。选项是
clear
清除所有已启用的权限这对于清除默认权限集非常有用,因此可以单独添加权限。
force-command=command
当证书用于身份验证时,强制执行命令而不是用户指定的任何shell或命令。
no-agent-forwarding
禁用ssh-agent(1)转发(默认允许)。
no-port-forwarding
禁用端口转发(默认允许)。
no-pty
禁用PTY分配(默认允许)。
no-user-rc
禁用sshd(8)执行〜/ .ssh / rc(默认允许)。
no-x11-forwarding
禁用X11转发(默认允许)。
permit-agent-forwarding
允许ssh-agent(1)转发。
permit-port-forwarding
允许端口转发。
permit-pty
允许PTY分配。
permit-user-rc
允许sshd(8)执行〜/ .ssh / rc。
permit-x11-forwarding
允许X11转发。
source-address=address_list
限制证书被认为有效的源地址。 address_list是一个逗号分隔的一个或多个地址/网络掩码对的列表
CIDR格式。目前,没有选项对主机密钥有效。
-
-o
使ssh-keygen使用新的OpenSSH格式而不是更兼容的PEM格式保存SSH协议2私钥。新格式增加了抵抗力
强制密码破解但6.5之前的OpenSSH版本不支持。 Ed25519密钥始终使用新的私钥格式。 -
-P passphrase
提供(旧)密码。 -
-p
请求更改私钥文件的密码,而不是创建新的私钥。程序将提示输入包含私钥的文件密码短语,新密码短语两次。 -
-Q
测试密钥是否已在KRL中被撤销。 -
-q
Silence ssh-keygen。 -
-R hostname
从known_hosts文件中删除属于hostname的所有密钥。此选项对于删除散列主机很有用(请参阅上面的-H选项)。 -
-r hostname
打印指定公钥文件的名为hostname的SSHFP指纹资源记录。 -
-S start
在生成DH-GEX的候选模量时指定起点(以十六进制表示)。 -
-s ca_key
使用指定的CA密钥验证(签名)公钥。 有关详细信息,请参阅证书部分。生成KRL时,-s指定用于直接通过密钥ID或序列号撤消证书的CA公钥文件的路径。 有关详细信息,请参阅KEY REVOCATION LISTS部分。 -
-T output_file
为了安全起见,测试DH组交换候选素数(使用-G选项生成)。 -
-t type
指定要创建的键的类型。对于协议版本1,可能的值是“rsa1”,对于协议版本2,可能的值是“dsa”,“ecdsa”,“ed25519”或“rsa”。 -
-u
更新KRL。使用-k指定时,通过命令行列出的键将添加到现有KRL中,而不是创建新的KRL。 -
-V validity_interval
签署证书时指定有效期间隔。有效期间隔可以包含一个时间,表示证书从现在开始有效在那个时候到期,或者可以由冒号分隔两次以指示明确的时间间隔。开始时间可以指定为YYYYMMDD格式的日期,YYYYMMDDHHMMSS格式的时间或相对时间(到当前时间),包括减号后跟sshd_config的TIME FORMATS部分中描述的格式的相对时间( 5)。结束时间可以指定为YYYYMMDD日期,YYYYMMDDHHMMSS时间或以加号开头的相对时间。
例如:“+ 52w1d”(从现在到52周和从现在起一天有效),“ - 4w:+ 4w”(从四周前到现在四周有效),“20100101123000:20110101123000”(有效期为2010年1月1日12:30至2011年1月1日12:30),“-1d:20110101”(有效期为2011年1月1日,昨天至午夜)。 -
-v
详细模式。 导致ssh-keygen打印有关其进度的调试消息。 这有助于调试模数生成。 多个-v选项增加了详细程度。 最大值为3。 -
-W generator
在测试DH-GEX的候选模量时指定所需的发生器。 -
-y
此选项将读取私有OpenSSH格式文件并将OpenSSH公钥打印到stdout。 -
-z serial_number
指定要嵌入证书中的序列号,以将此证书与同一CA中的其他证书区分开来。 默认序列号为零。
生成KRL时,-z标志用于指定KRL版本号。
MODULI GENERATION
ssh-keygen可用于生成Diffie-Hellman组交换(DH-GEX)协议的组。生成这些组的过程分为两步:首先,使用快速但内存密集的过程生成候选素数。然后测试这些候选素数的适用性(CPU密集型过程)。
使用-G选项执行质数的生成。可以通过-b选项指定所需的素数长度。例如:
#ssh-keygen -G moduli-2048.candidates -b 2048
默认情况下,搜索素数从所需长度范围内的随机点开始。这可以使用-S选项覆盖,该选项指定不同的起点(在
十六进制)。
生成一组候选人后,必须对其进行筛选以确定其适用性。这可以使用-T选项执行。在这种模式下,ssh-keygen将从中读取候选人标准输入(或使用-f选项指定的文件)。例如:
#ssh-keygen -T moduli-2048 -f moduli-2048.candidates
默认情况下,每位候选人将接受100次素性测试。这可以使用-a选项覆盖。 DH发生器值将自动选择正在考虑中。如果需要特定的生成器,可以使用-W选项请求它。有效的生成器值为2,3和5。
屏蔽的DH组可以安装在/ etc / ssh / moduli中。重要的是,此文件包含一系列位长的模数,并且连接的两端共享
模量。
证书
ssh-keygen支持密钥签名以生成可用于用户或主机身份验证的证书。 证书包括公钥,一些身份信息,
零个或多个主体(用户或主机)名称以及由证书颁发机构(CA)密钥签名的一组选项。 然后,客户端或服务器可以只信任CA密钥并且
如果它在证书上签名而不是信任许多用户/主机密钥。 请注意,OpenSSH证书是X.509证书的一种不同且更简单的格式用于ssl(8)。
ssh-keygen支持两种类型的证书:user和host。 用户证书对服务器的用户进行身份验证,而主机证书则向用户验证服务器主机。 要生成用户证书:
$ ssh-keygen -s /path/to/ca_key -I key_id /path/to/user_key.pub
生成的证书将放在/path/to/user_key-cert.pub中。 主机证书需要-h选项:
$ ssh-keygen -s /path/to/ca_key -I key_id -h /path/to/host_key.pub
主机证书将输出到/path/to/host_key-cert.pub。
可以使用存储在PKCS#11令牌中的CA密钥进行签名,方法是使用-D提供令牌库,并通过提供其公共一半作为参数来识别CA密钥。 -s:
$ ssh-keygen -s ca_key.pub -D libpkcs11.so -I key_id host_key.pub
在所有情况下,key_id是服务器在使用证书进行身份验证时记录的“密钥标识符”。
证书可能被限制为对一组主体(用户/主机)名称有效。 默认情况下,生成的证书对所有用户或主机都有效。 生成证书
对于一组指定的主体:
$ ssh-keygen -s ca_key -I key_id -n user1,user2 user_key.pub
$ ssh-keygen -s ca_key -I key_id -h -n host.domain user_key.pub
可以通过证书选项指定对用户证书的有效性和使用的额外限制。 证书选项可能会禁用SSH会话的功能,
仅在从特定源地址呈现时可能有效或可能强制使用特定命令。 有关有效证书选项的列表,请参阅文档
上面的-O选项。
最后,可以使用有效期限定义证书。 -V选项允许指定证书的开始和结束时间。 一次呈现的证书超出此范围将被视为无效。 默认情况下,证书从UNIX Epoch到远期是有效的。
对于要用于用户或主机身份验证的证书,sshd(8)或ssh(1)必须信任CA公钥。 有关详细信息,请参阅这些手册页。
秘钥撤销列表
ssh-keygen能够管理OpenSSH格式的密钥撤销列表(KRL)。 这些二进制文件使用紧凑格式指定要撤销的密钥或证书,如果按序列号撤销,则每个证书只需要一位。
可以使用-k标志生成KRL。 此选项从命令行读取一个或多个文件,并生成新的KRL。 这些文件可能包含KRL规范(见下文)或公共密钥,每行列出一个。 通过在KRL中列出其散列或内容以及由序列号或密钥ID撤销的证书(如果序列为零或不可用)来撤销普通公钥。
使用KRL规范撤销密钥可以明确控制用于撤销密钥的记录类型,并且可以用于通过序列号或密钥ID直接撤销证书,而无需手头有完整的原始证书。 KRL规范由包含以下指令之一的行组成,后跟冒号和一些特定于指令的信息。
-
serial:serial_number [-se_number]
撤消具有指定序列号的证书。 序列号是64位值,不包括零,可以用十进制,十六进制或八进制表示。 如果两个连续 数字由连字符分隔,然后撤销包括和之间的序列号范围。 必须在ssh-keygen上指定CA密钥命令行使用-s选项。 -
id:key_id
撤消具有指定密钥ID字符串的证书。 必须使用-s选项在ssh-keygen命令行上指定CA密钥。 -
key:public_key
撤消指定的密钥。 如果列出了证书,则将其作为普通公钥撤消。 -
sha1:public_key
通过SHA1哈希撤消指定的密钥。
除了-k之外,还可以使用-u标志更新KRL。 指定此选项后,通过命令行列出的键将合并到KRL中,并添加到已存在的键中。 在给定KRL的情况下,还可以测试它是否撤销特定的密钥(或密钥)。 -Q标志将查询现有KRL,测试命令行上指定的每个密钥。 如果命令行中列出的任何键已被撤销(或遇到错误),则ssh-keygen将以非零退出状态退出。 仅退回零退出状态 如果没有钥匙被撤销。
文件
-
~/.ssh/identity
包含用户的协议版本1 RSA身份验证标识。除了用户之外,任何人都不应该读取此文件。可以指定密码
生成密钥时;该密码将用于使用3DES加密此文件的私有部分。 ssh-keygen不会自动访问此文件,但它是
作为私钥的默认文件提供。 ssh(1)将在尝试登录时读取此文件。 -
~/.ssh/identity.pub
包含用于身份验证的协议版本1 RSA公钥。该文件的内容应添加到用户所有机器上的〜/ .ssh / authorized_keys
希望使用RSA身份验证登录。无需保密此文件的内容。 -
~/.ssh/id_dsa
-
~/.ssh/id_ecdsa
-
~/.ssh/id_ed25519
-
~/.ssh/id_rsa
包含用户的协议版本2 DSA,ECDSA,ED25519或RSA身份验证标识。 除了用户之外,任何人都不应该读取此文件。 有可能的生成密钥时指定密码; 该密码将用于使用128位AES加密此文件的私有部分。 此文件不是自动的
由ssh-keygen访问,但它作为私钥的默认文件提供。 ssh(1)将在尝试登录时读取此文件。 -
~/.ssh/id_dsa.pub
-
~/.ssh/id_ecdsa.pub
-
~/.ssh/id_ed25519.pub
-
~/.ssh/id_rsa.pub
包含用于身份验证的协议版本2 DSA,ECDSA,ED25519或RSA公钥。 该文件的内容应添加到〜/ .ssh / authorized_keys上 用户希望使用公钥认证登录的机器。 无需保密此文件的内容。
- /etc/ssh/moduli
包含用于DH-GEX的Diffie-Hellman组。 文件格式在模数(5)中描述。
环境
SSH_USE_STRONG_RNG
OpenSSL随机生成器的重新安装通常从/ dev / urandom完成。 如果将SSH_USE_STRONG_RNG环境变量设置为除OpenSSL以外的值,随机生成器从/ dev / random重新开始。 读取的字节数由SSH_USE_STRONG_RNG值定义。 最小值为14个字节。 建议不要使用此设置在没有硬件随机生成器的计算机上,因为熵不足导致连接被阻塞,直到有足够的熵可用。
SEE ALSO
ssh(1), ssh-add(1), ssh-agent(1), moduli(5), sshd(8)
The Secure Shell (SSH) Public Key File Format, RFC 4716, 2006.
AUTHORS
OpenSSH是Tatu Ylonen发布的原始和免费ssh 1.2.12的衍生版本。 Aaron Campbell,Bob Beck,Markus Friedl,Niels Provos,Theo de Raadt和Dug Song取消了很多错误,重新添加新功能并创建OpenSSH。 Markus Friedl为SSH协议版本1.5和2.0提供了支持。
作者:欧阳鹏 欢迎转载,与人分享是进步的源泉!
转载请保留原文地址:https://blog.csdn.net/ouyang_peng/article/details/83115290如果觉得本文对您有所帮助,欢迎您扫码下图所示的支付宝和微信支付二维码对本文进行随意打赏。您的支持将鼓励我继续创作