[CM311-1A]-全网最全 Android 软件管理_gdyd-iptvsettings-an9-all-debug-1.0.0-20220110-095
赞
踩
##################################################
目录
##################################################
如何使用命令安装卸载应用
——————————
示例安装一个小破站 TV 版
%%%%%
将安装包上传到系统 /tmp 目录
如下 看注释:
- cmcc_jiangsu:/ # cd /tmp /* 进入 tmp */
- cmcc_jiangsu:/tmp # ls /* 此时可以看到没有安装包 */
- capture
- cmcc_jiangsu:/tmp # exit /* 退出 shell */
-
- C:\Users\byme>adb connect 192.168.0.101 /* 确定连接 */
- already connected to 192.168.0.101:5555
-
- C:\Users\byme>adb push D:\download\bilibiliTV\bilibiliTV_1.5.1_dangbei.apk /tmp /* 将 apk 上传到 tmp 目录 */
- D:\download\bilibiliTV\bilibiliTV_1.5....d. 3.1 MB/s (20727626 bytes in 6.398s)
-
- C:\Users\byme>adb shell /* 进入系统终端 */
- cmcc_jiangsu:/ # cd /tmp /* 进入 tmp */
- cmcc_jiangsu:/tmp # ls /* 发现 apk */
- capture
- cmcc_jiangsu:/tmp # ls
- bilibiliTV_1.5.1_dangbei.apk capture
- cmcc_jiangsu:/tmp # ls -alh
- total 10M
- drwxrwxrwt 3 root root 80 2022-07-23 17:21 .
- drwxr-xr-x 23 root root 0 2015-01-01 08:00 ..
- -rw-r--r-- 1 root root 20M 2022-07-22 23:43 bilibiliTV_1.5.1_dangbei.apk
- drwxrwxrwt 2 root root 40 2015-01-01 08:00 capture
- cmcc_jiangsu:/tmp #
%%%%%
安装 bilibiliTV 版
- cmcc_jiangsu:/tmp # ls /* 看一眼 apk 名字 */
- bilibiliTV_1.5.1_dangbei.apk capture
- cmcc_jiangsu:/tmp # pm install bilibiliTV_1.5.1_dangbei.apk /* 安装 apk 输入前几个字母就可以按下 TAB 自动补全 */
- avc: denied { read } for scontext=u:r:system_server:s0 tcontext=u:object_r:su
- _tmpfs:s0 tclass=file permissive=1
- Success
- cmcc_jiangsu:/tmp # screencap -p /sdcard/sc/1.png /* 截取屏幕 */
- screencap 3
- screencap start. screen_type: 1
- file path: /sdcard/sc/1.png
- new ScreenCatch ok
- got video+osd data: 1280 x 720
- SkEncodeImage success
- screencap end
- cmcc_jiangsu:/tmp # ls /sdcard/sc -alh /* 确定截取成功 */
- total 282K
- drwxrwx--x 2 root sdcard_rw 4.0K 2022-07-20 18:58 .
- drwxrwx--x 22 root sdcard_rw 4.0K 2022-07-20 18:56 ..
- -rw-rw---- 1 root sdcard_rw 554K 2022-07-23 17:52 1.png
- cmcc_jiangsu:/tmp # exit
-
- C:\Users\byme>adb pull /sdcard/sc/1.png D:1.png /* 将截屏下载到 D 盘根目录 */
- /sdcard/sc/1.png: 1 file pulled, 0 skipped. 0.3 MB/s (567707 bytes in 1.863s)
-
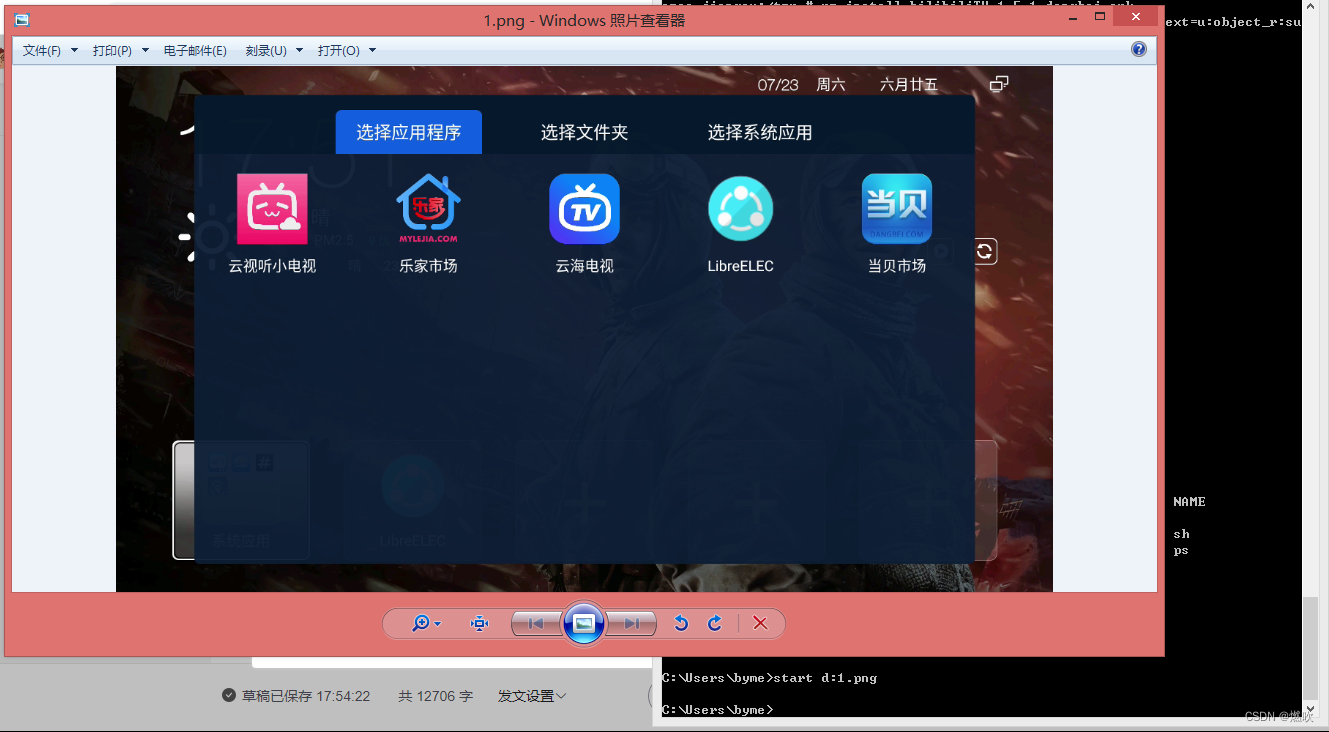
- C:\Users\byme> start 1.png /* 使用默认图像查看器打开截屏文件 */
看 出现一个云视听小电视:
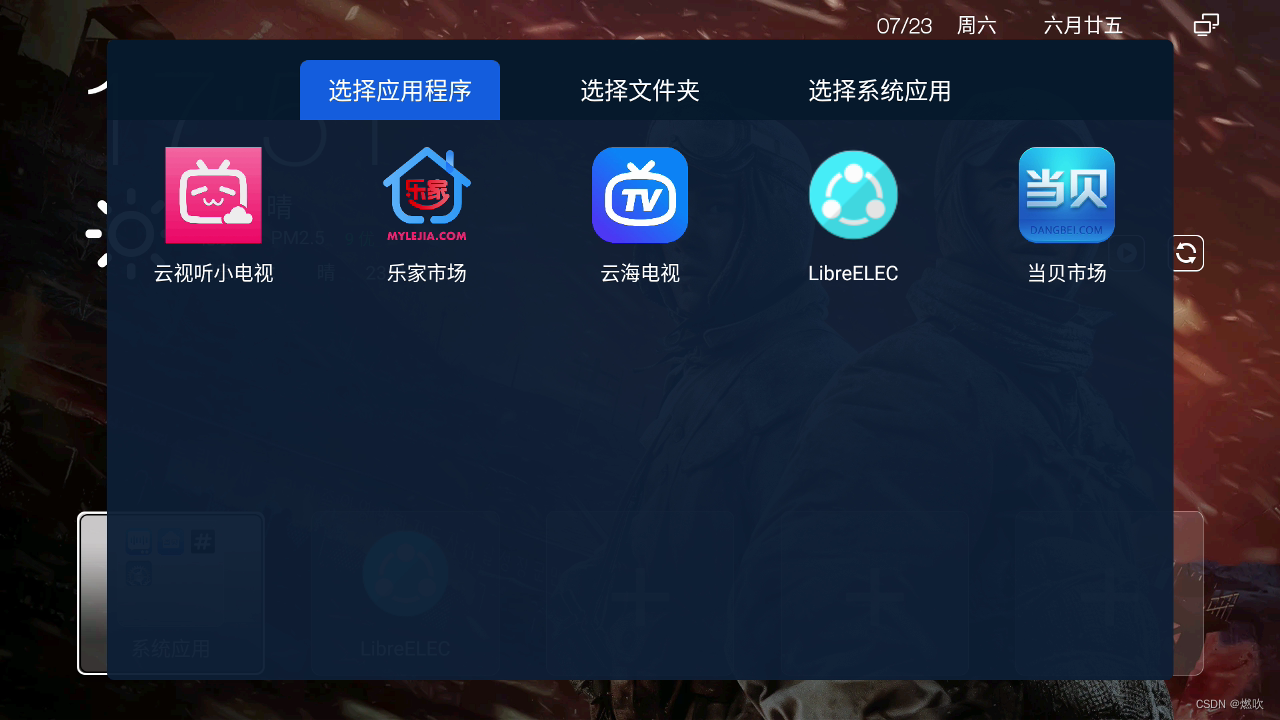
安装成功:
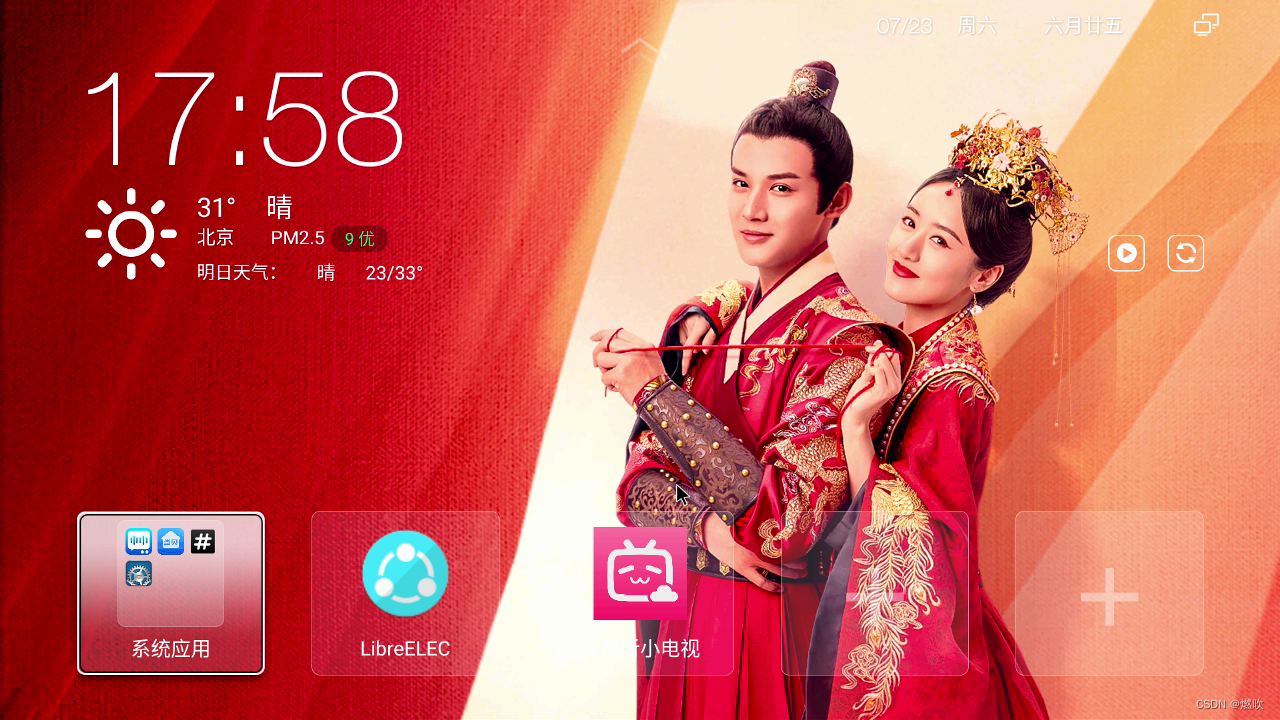
添加到桌面:
启动成功:
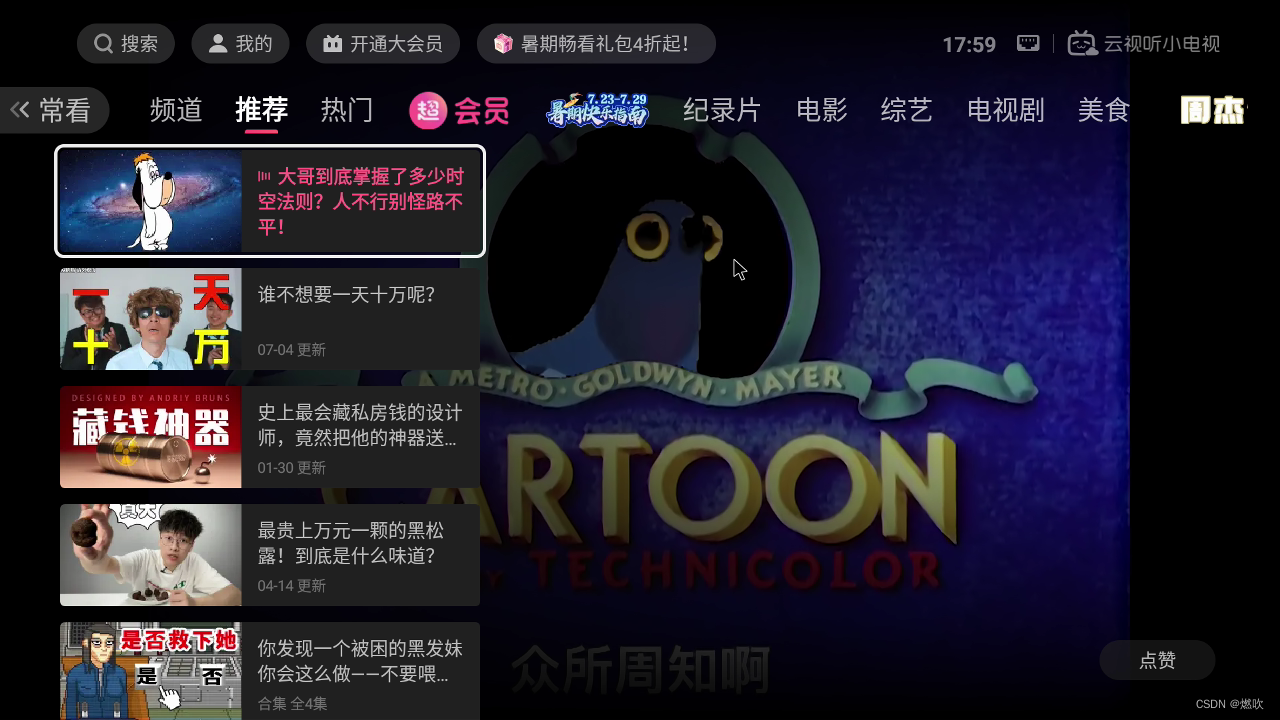
好家伙我竟然在盒子上逛 B 站:

%%%%%
查看安装后的软件信息
我们很轻易的就能获取这个应用的包名叫
com.xiaodianshi.tv.yst 云视听小电视
- cmcc_jiangsu:/ # pm list packages -3 /* 查看安装的所有第三方软甲 */
- package:com.xiaodianshi.tv.yst /* 这个就是我们刚刚安装的 b 站 */
- package:com.mylejia.store
- package:com.fengyun.live
- package:me.thomastv.rebootupdate
- package:com.dangbeimarket
- cmcc_jiangsu:/ # pm list packages -i "tv" /* 查看 tv 相关软件的安装信息 */
- package:com.xiaodianshi.tv.yst installer=null
- package:com.dangbei.tvlauncher installer=null
- package:me.thomastv.rebootupdate installer=null
- cmcc_jiangsu:/ # pm list packages -f "tv" /* 查看 tv 相关联应用的文件 */
- package:/data/app/com.xiaodianshi.tv.yst-7s2x33sktQES0TVqJsQhbA==/base.apk=com.x
- iaodianshi.tv.yst
- package:/system/app/Dangbei2.apk=com.dangbei.tvlauncher
- package:/data/app/me.thomastv.rebootupdate-4SVHakbq9YXs3X7ozxyY0w==/base.apk=me.
- thomastv.rebootupdate
- cmcc_jiangsu:/ # ls /data/app/com.xiaodianshi.tv.yst-7s2x33sktQES0TVqJsQhbA\=\=
- base.apk lib oat
- cmcc_jiangsu:/ # ls -alh /data/app/com.xiaodianshi.tv.yst-7s2x33sktQES0TVqJsQhbA\=\=
- total 10M
- drwxr-xr-x 4 system system 4.0K 2022-07-23 17:44 .
- drwxrwxr-x 8 system system 4.0K 2022-07-23 17:44 ..
- -rw-r--r-- 1 system system 20M 2022-07-23 17:44 base.apk
- drwxr-xr-x 3 system system 4.0K 2022-07-23 17:44 lib
- drwxrwx--x 3 system install 4.0K 2022-07-23 17:44 oat
- cmcc_jiangsu:/ #
%%%%%
卸载刚刚安装的 tv
- cmcc_jiangsu:/ # pm list packages -3 /* 卸载之前的第三方软件 */
- package:com.xiaodianshi.tv.yst
- package:com.mylejia.store
- package:com.fengyun.live
- package:me.thomastv.rebootupdate
- package:com.dangbeimarket
- cmcc_jiangsu:/ # pm uninstall com.xiaodianshi.tv.yst /* 卸载小破站 */
- Success
- cmcc_jiangsu:/ # pm list packages -3 /* 卸载之后再次查看第三方软件 */
- package:com.mylejia.store
- package:com.fengyun.live
- package:me.thomastv.rebootupdate
- package:com.dangbeimarket
- cmcc_jiangsu:/ #
——————————
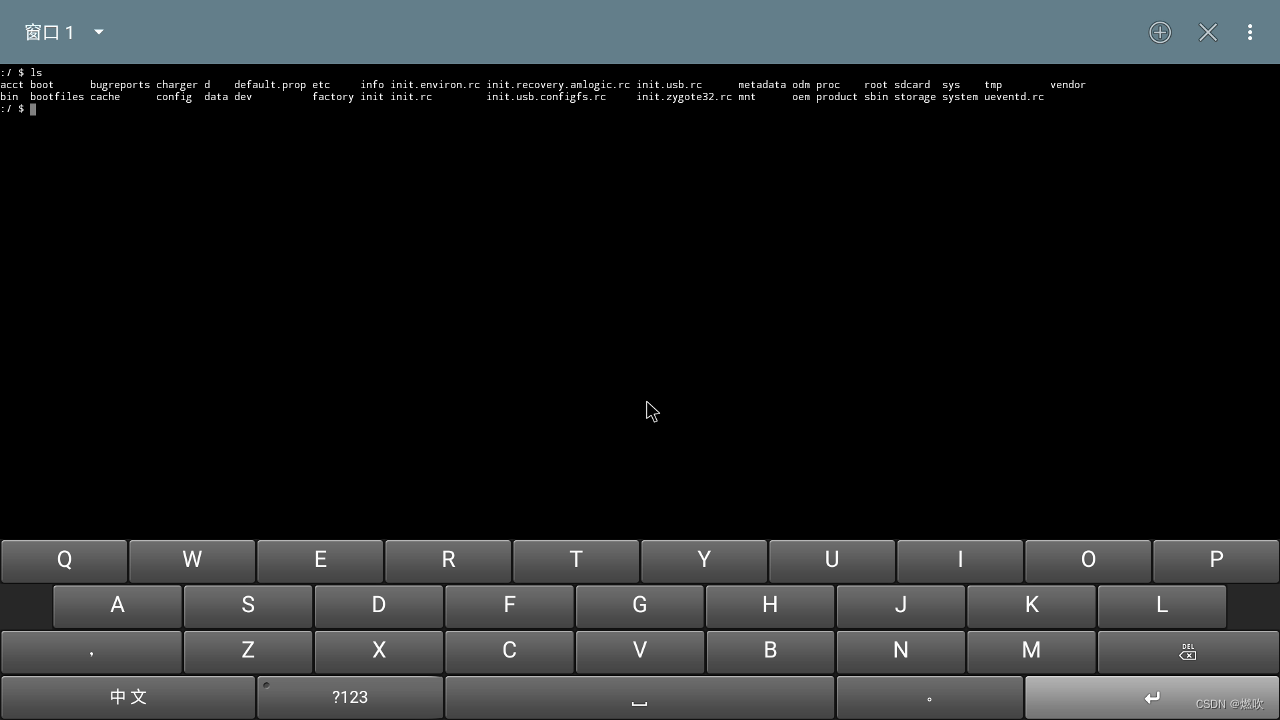
真的推荐安装一个安卓终端模拟器
安卓终端模拟器就相当于 Windows 的 cmd/Xshell 或者 Linux 的 console/terminal
开源地址:
Terminal Emulator for Android Downloads![]() https://jackpal.github.io/Android-Terminal-Emulator/
https://jackpal.github.io/Android-Terminal-Emulator/
如果访问不了也可以下载我提供的资源 跟上面是一样的:
- pan.baidu.com/s/1yw8pzpMviDLjRJRf1IVZ4w
- 1297
- ranchui
%%%%%
jackpal.androidterm 包
我这个包名是 jackpal.androidterm
- cmcc_jiangsu:/ # pm list packages -3 /* 安装之前的第三方软件 */
- package:com.xiaodianshi.tv.yst
- package:com.mylejia.store
- package:com.fengyun.live
- package:me.thomastv.rebootupdate
- package:com.dangbeimarket
- cmcc_jiangsu:/ # ls /tmp/Term.apk -alh /* 确定 APK 位置 */
- -rw-r--r-- 1 root root 551K 2022-05-28 23:35 /tmp/Term.apk
- cmcc_jiangsu:/ # pm install /tmp/Term.apk /* 安装 APK */
- avc: denied { read } for scontext=u:r:system_server:s0 tcontext=u:object_r:su
- _tmpfs:s0 tclass=file permissive=1
- Success
- cmcc_jiangsu:/ # pm list packages -3 /* 安装之后再看 */
- package:com.xiaodianshi.tv.yst
- package:com.mylejia.store
- package:com.fengyun.live
- package:me.thomastv.rebootupdate
- package:jackpal.androidterm
- package:com.dangbeimarket
- cmcc_jiangsu:/ # screencap -p /sdcard/sc/1.png /* 截个屏 */
- screencap 3
- screencap start. screen_type: 1
- file path: /sdcard/sc/1.png
- new ScreenCatch ok
- got video+osd data: 1280 x 720
- SkEncodeImage success
- screencap end
- cmcc_jiangsu:/ # exit /* 退出终端 */
-
- C:\Users\byme>adb pull /sdcard/sc/1.png d:1.png /* 获取截屏 */
- /sdcard/sc/1.png: 1 file pulled, 0 ski...ed. 2.9 MB/s (1237270 bytes in 0.402s)
-
- C:\Users\byme>start d:1.png /* 打开截屏图像 */
截屏如下:
安卓终端模拟器 可以运行命令:
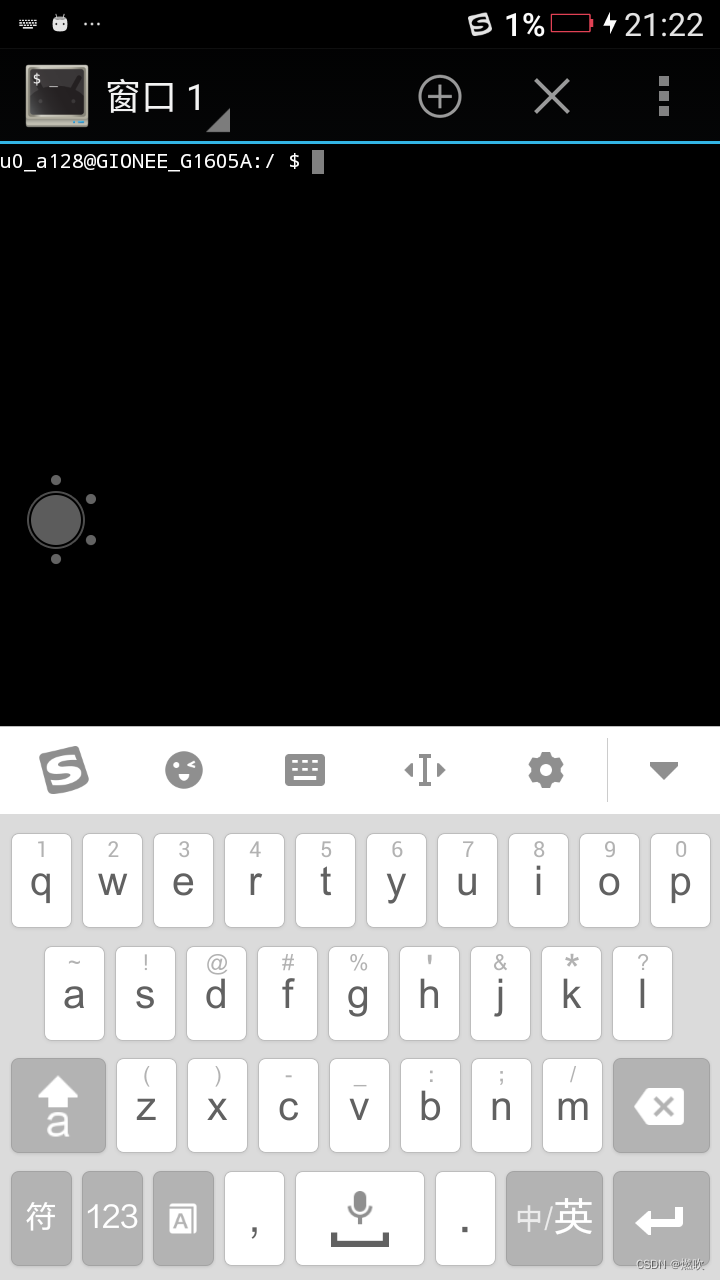
——————————
查看某个应用的详细信息
使用 dumpsys 的 package 子命令可以查看指定包的详细信息
这边我是在一个小手机上查看安装的旧版本的终端模拟器:
- shell@GIONEE_G1605A:/mnt/sdcard $ pm list packages -3 | grep term /* 在第三方应用中搜索包含 term 字样的包 */
- package:jackpal.androidterm
- shell@GIONEE_G1605A:/mnt/sdcard $ dumpsys package jackpal.androidterm /* 查看终端模拟器应用的详细信息 */
- Activity Resolver Table:
- Full MIME Types:
- */*:
- 3d65be5 jackpal.androidterm/.TermHere
- a6316ba jackpal.androidterm/.shortcuts.FSNavigator
-
- Wild MIME Types:
- *:
- 3d65be5 jackpal.androidterm/.TermHere
- a6316ba jackpal.androidterm/.shortcuts.FSNavigator
-
- Non-Data Actions:
- jackpal.androidterm.RUN_SHORTCUT:
- af9896b jackpal.androidterm/.RunShortcut
- jackpal.androidterm.private.SWITCH_WINDOW:
- 7e04cc8 jackpal.androidterm/.TermInternal
- jackpal.androidterm.OPEN_NEW_WINDOW:
- c95d161 jackpal.androidterm/.RemoteInterface
- android.intent.action.MAIN:
- 39be486 jackpal.androidterm/.Term
- ea55147 jackpal.androidterm/.shortcuts.AddShortcut
- android.intent.action.PICK:
- a6316ba jackpal.androidterm/.shortcuts.FSNavigator
- jackpal.androidterm.RUN_SCRIPT:
- f116d74 jackpal.androidterm/.RunScript
- jackpal.androidterm.private.OPEN_NEW_WINDOW:
- 7e04cc8 jackpal.androidterm/.TermInternal
- android.intent.action.CREATE_SHORTCUT:
- ea55147 jackpal.androidterm/.shortcuts.AddShortcut
-
- MIME Typed Actions:
- android.intent.action.SEND:
- 3d65be5 jackpal.androidterm/.TermHere
- android.intent.action.GET_CONTENT:
- a6316ba jackpal.androidterm/.shortcuts.FSNavigator
-
- Permissions:
- Permission [jackpal.androidterm.permission.PREPEND_TO_PATH] (57d229d):
- sourcePackage=jackpal.androidterm
- uid=10128 gids=null type=0 prot=dangerous
- perm=Permission{941c312 jackpal.androidterm.permission.PREPEND_TO_PATH}
- packageSetting=PackageSetting{c5bbae3 jackpal.androidterm/10128}
- Permission [jackpal.androidterm.permission.RUN_SCRIPT] (491ece0):
- sourcePackage=jackpal.androidterm
- uid=10128 gids=null type=0 prot=dangerous
- perm=Permission{d8e4b99 jackpal.androidterm.permission.RUN_SCRIPT}
- packageSetting=PackageSetting{c5bbae3 jackpal.androidterm/10128}
- Permission [jackpal.androidterm.permission.APPEND_TO_PATH] (1f4fe5e):
- sourcePackage=jackpal.androidterm
- uid=10128 gids=null type=0 prot=dangerous
- perm=Permission{585223f jackpal.androidterm.permission.APPEND_TO_PATH}
- packageSetting=PackageSetting{c5bbae3 jackpal.androidterm/10128}
-
- Key Set Manager:
- [jackpal.androidterm]
- Signing KeySets: 27
-
- Packages:
- Package [jackpal.androidterm] (c5bbae3):
- userId=10128
- pkg=Package{e5a569a jackpal.androidterm}
- codePath=/data/app/jackpal.androidterm-1
- resourcePath=/data/app/jackpal.androidterm-1
- legacyNativeLibraryDir=/data/app/jackpal.androidterm-1/lib
- primaryCpuAbi=arm64-v8a
- secondaryCpuAbi=null
- versionCode=66 targetSdk=11
- versionName=1.0.65
- splits=[base]
- applicationInfo=ApplicationInfo{5d8f70c jackpal.androidterm clone=0}
- flags=[ HAS_CODE ALLOW_CLEAR_USER_DATA ALLOW_BACKUP ]
- pkgFlagsEx=[ ]
- dataDir=/data/user/0/jackpal.androidterm
- supportsScreens=[small, medium, large, xlarge, resizeable, anyDensity]
- timeStamp=2022-07-24 20:02:40
- firstInstallTime=2022-07-24 20:02:40
- lastUpdateTime=2022-07-24 20:02:40
- signatures=PackageSignatures{7ef0855 [c0ea26a]}
- installPermissionsFixed=true installStatus=1
- pkgFlags=[ HAS_CODE ALLOW_CLEAR_USER_DATA ALLOW_BACKUP ]
- declared permissions:
- jackpal.androidterm.permission.RUN_SCRIPT: prot=dangerous, INSTALLED
- jackpal.androidterm.permission.APPEND_TO_PATH: prot=dangerous, INSTALLED
- jackpal.androidterm.permission.PREPEND_TO_PATH: prot=dangerous, INSTALLED
- requested permissions:
- android.permission.INTERNET
- android.permission.READ_EXTERNAL_STORAGE
- android.permission.WRITE_EXTERNAL_STORAGE
- android.permission.ACCESS_SUPERUSER
- android.permission.WAKE_LOCK
- install permissions:
- android.permission.INTERNET: granted=true
- android.permission.READ_EXTERNAL_STORAGE: granted=true
- android.permission.WRITE_EXTERNAL_STORAGE: granted=true
- android.permission.WAKE_LOCK: granted=true
- User 0: installed=true hidden=false stopped=false notLaunched=false enabled
- =0
- gids=[3003]
- runtime permissions:
- shell@GIONEE_G1605A:/mnt/sdcard $
——————————
如何使用命令启动应用程序
%%%%%
在前台运行 app
先让程序在前台显示 不要黑屏不要切换到后台:
%%%%%
获取包名和 activity 路径
此时可以使用命令获取信息了
如果你在 cmd :
adb shell dumpsys window windows | findstr “Current”如果你在终端中:
- shell@GIONEE_G1605A:/ $ dumpsys window windows | grep Current
- mCurrentFocus=Window{144ca1f u0 jackpal.androidterm/jackpal.androidterm.Term}
- shell@GIONEE_G1605A:/ $
可以从
jackpal.androidterm/jackpal.androidterm.Term
看到包名和启动名:
包名 jackpal.androidterm
启动名 jackpal.androidterm.Term
%%%%%
使用 am 的 start 命令启动 APP
语法格式:
am start package/applicationId.launchActivity package 是 app 的包名 一般是跟 applicationId 是相同的值
launch activity 是启动 activity 的完整路径
示例 jackpal.androidterm/jackpal.androidterm.Term 中
jackpal.androidterm 是 package
jackpal.androidterm 是 applicationId
Term 是 activity
jackpal.androidterm.Term 是 launch activity
启动 jackpal.androidterm 示例:
- shell@GIONEE_G1605A:/ $ am start jackpal.androidterm/jackpal.androidterm.Term
- Starting: Intent { act=android.intent.action.MAIN cat=[android.intent.category.L
- AUNCHER] cmp=jackpal.androidterm/.Term }
- shell@GIONEE_G1605A:/ $
或者
- shell@GIONEE_G1605A:/ $ am start -n jackpal.androidterm/jackpal.androidterm.Term
- Starting: Intent { cmp=jackpal.androidterm/.Term }
- Warning: Activity not started, its current task has been brought to the front
- shell@GIONEE_G1605A:/ $
事实也确实成功了:

——————————
示例使用命令启动哔哩哔哩 TV 版
启动小破站后截一下屏
- cmcc_jiangsu:/ # screencap -p /sdcard/sc/1.png /* 截个屏 */
- screencap 3
- screencap start. screen_type: 1
- file path: /sdcard/sc/1.png
- new ScreenCatch ok
- got video+osd data: 1280 x 720
- SkEncodeImage success
- screencap end
- cmcc_jiangsu:/ #
查看当前窗口的 activity 信息:
- cmcc_jiangsu:/ # dumpsys window windows | grep Current
- mCurrentFocus=Window{d898b33 u0 com.xiaodianshi.tv.yst/com.xiaodianshi.tv.yst.
- ui.introduction.IntroductionActivity}
- cmcc_jiangsu:/ #
好家伙是真的长:
com.xiaodianshi.tv.yst.ui.introduction.IntroductionActivity通过命令启动 bilibili tv 版:
- cmcc_jiangsu:/ # am start com.xiaodianshi.tv.yst/com.xiaodianshi.tv.yst.ui.introduction.IntroductionActivity
- Starting: Intent { act=android.intent.action.MAIN cat=[android.intent.category.L
- AUNCHER] cmp=com.xiaodianshi.tv.yst/.ui.introduction.IntroductionActivity }
- cmcc_jiangsu:/ # screencap -p /sdcard/sc/1.png
- screencap 3
- screencap start. screen_type: 1
- file path: /sdcard/sc/1.png
- new ScreenCatch ok
- got video+osd data: 1280 x 720
- SkEncodeImage success
- screencap end
- cmcc_jiangsu:/ #
结果笑死人 启动的只是那个协议对话框:
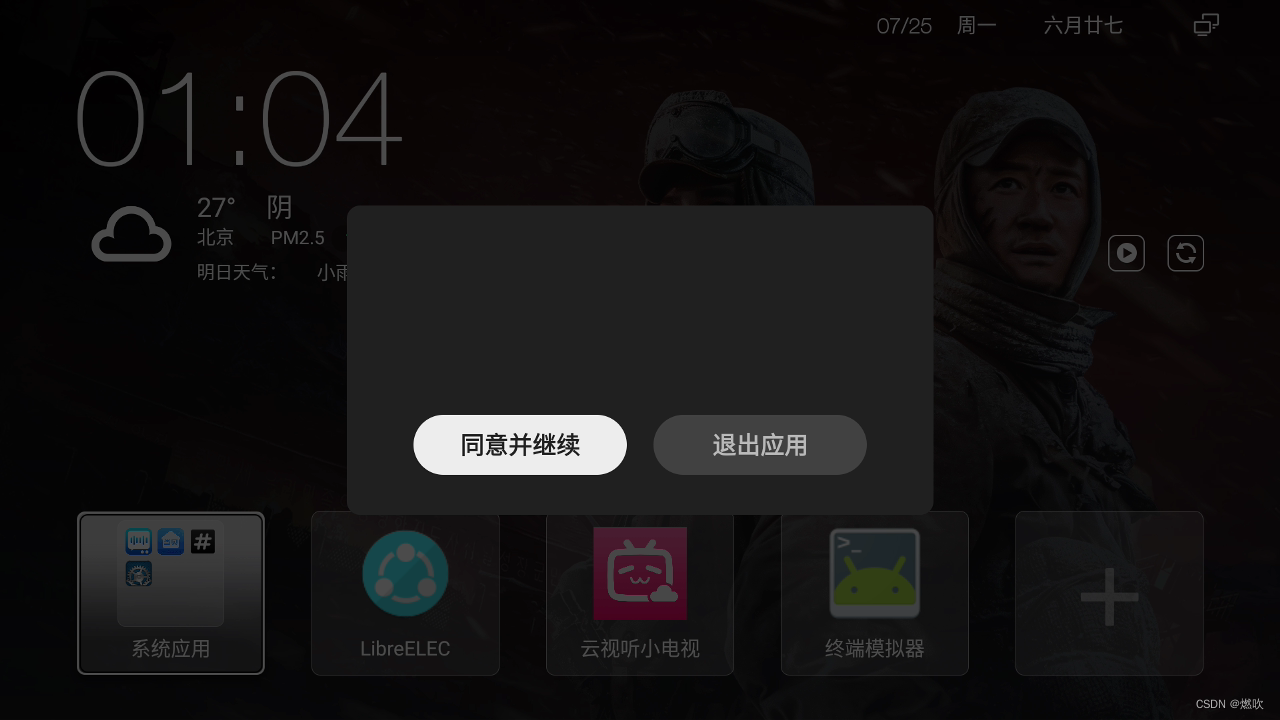
无奈只好从应用详细信息中筛选:
- cmcc_jiangsu:/ # dumpsys package com.xiaodianshi.tv.yst | grep com.xiaodianshi.tv.yst
- 86a175e com.xiaodianshi.tv.yst/.ui.transition.TransitionActivity filter
- d6fb37d
- Action: "com.xiaodianshi.tv.yst.uri"
- Authority: "com.xiaodianshi.tv.yst": -1
- 86a175e com.xiaodianshi.tv.yst/.ui.transition.TransitionActivity filter
- edb272
- Authority: "com.xiaodianshi.tv.yst": -1
- 8fec73f com.xiaodianshi.tv.yst/com.yst.projection.ProjectionPlayerActivi
- tyV2 filter fc90a79
- 8fec73f com.xiaodianshi.tv.yst/com.yst.projection.ProjectionPlayerActivi
- tyV2 filter c6083be
- Action: "com.xiaodianshi.tv.yst.uri"
- com.xiaodianshi.tv.yst:
- eea380c com.xiaodianshi.tv.yst/.ui.main.MainActivity filter 7bfe6c3
- Action: "com.xiaodianshi.tv.yst"
- com.xiaodianshi.tv.yst.external:
- 86a175e com.xiaodianshi.tv.yst/.ui.transition.TransitionActivity filter
- ea235d4
- Action: "com.xiaodianshi.tv.yst.external"
- com.xiaodianshi.tv.yst.projection.entry:
- c15b555 com.xiaodianshi.tv.yst/com.yst.projection.entry.ProjectionEntryA
- ctivity filter 302c1f
- Action: "com.xiaodianshi.tv.yst.projection.entry"
- eea380c com.xiaodianshi.tv.yst/.ui.main.MainActivity filter 7bfe6c3
- Action: "com.xiaodianshi.tv.yst"
- eea380c com.xiaodianshi.tv.yst/.ui.main.MainActivity filter 2d6db40
- 73c4b6a com.xiaodianshi.tv.yst/com.bilibili.opd.app.bizcommon.sentinel.s
- ession.ChildProcessSessionBroadcastReceiver filter 8147f27
- 1a2985b com.xiaodianshi.tv.yst/.ui.transition.PreassembleBroadcastReceiv
- er filter c071441
- e08c8f8 com.xiaodianshi.tv.yst/.video.service.YstMediaButtonReceiver fil
- ter 2759de6
- 1a2985b com.xiaodianshi.tv.yst/.ui.transition.PreassembleBroadcastReceiv
- er filter c071441
- ec951d1 com.xiaodianshi.tv.yst/.video.service.YstMediaService filter bd3
- 4f28
- Permission [com.xiaodianshi.tv.yst.permission.BLKV] (8352e34):
- sourcePackage=com.xiaodianshi.tv.yst
- perm=Permission{b4bb436 com.xiaodianshi.tv.yst.permission.BLKV}
- packageSetting=PackageSetting{7e85f37 com.xiaodianshi.tv.yst/10030}
- com.xiaodianshi.tv.yst/.provider.TvSearchSuggestionProvider:
- Provider{67d7ca4 com.xiaodianshi.tv.yst/.provider.TvSearchSuggestionProvider
- }
- com.xiaodianshi.tv.yst/com.bilibili.lib.media.resolver.resolve.MediaResolvePro
- vider:
- Provider{a403a0d com.xiaodianshi.tv.yst/com.bilibili.lib.media.resolver.reso
- lve.MediaResolveProvider}
- com.xiaodianshi.tv.yst/androidx.lifecycle.ProcessLifecycleOwnerInitializer:
- Provider{216ddc2 com.xiaodianshi.tv.yst/androidx.lifecycle.ProcessLifecycleO
- wnerInitializer}
- com.xiaodianshi.tv.yst/androidx.core.content.FileProvider:
- Provider{159b7d3 com.xiaodianshi.tv.yst/androidx.core.content.FileProvider}
- com.xiaodianshi.tv.yst/com.bilibili.lib.okdownloader.internal.db.DownloadDatab
- aseProvider:
- Provider{967bf10 com.xiaodianshi.tv.yst/com.bilibili.lib.okdownloader.intern
- al.db.DownloadDatabaseProvider}
- com.xiaodianshi.tv.yst/com.bilibili.lib.mod.ModResourceProvider:
- Provider{3c36a09 com.xiaodianshi.tv.yst/com.bilibili.lib.mod.ModResourceProv
- ider}
- com.xiaodianshi.tv.yst/com.bilibili.xpref.XprefProvider:
- Provider{79140e com.xiaodianshi.tv.yst/com.bilibili.xpref.XprefProvider}
- com.xiaodianshi.tv.yst/com.bilibili.base.ipc.IPCActivityStateProvider:
- Provider{87dfe2f com.xiaodianshi.tv.yst/com.bilibili.base.ipc.IPCActivitySta
- teProvider}
- com.xiaodianshi.tv.yst/com.bilibili.lib.account.AuthProvider:
- Provider{871bc3c com.xiaodianshi.tv.yst/com.bilibili.lib.account.AuthProvide
- r}
- com.xiaodianshi.tv.yst/com.bilibili.app.lib.modx.ModImageContentProvider:
- Provider{22f9dc5 com.xiaodianshi.tv.yst/com.bilibili.app.lib.modx.ModImageCo
- ntentProvider}
- com.xiaodianshi.tv.yst/com.coocaa.historylib.HistoryContentProvider:
- Provider{bb6631a com.xiaodianshi.tv.yst/com.coocaa.historylib.HistoryContent
- Provider}
- com.xiaodianshi.tv.yst/com.coocaa.historylib.CollectContentProvider:
- Provider{ef64e4b com.xiaodianshi.tv.yst/com.coocaa.historylib.CollectContent
- Provider}
- com.xiaodianshi.tv.yst/com.bilibili.infra.base.provider.InfraInitProvider:
- Provider{3bc6028 com.xiaodianshi.tv.yst/com.bilibili.infra.base.provider.Inf
- raInitProvider}
- [com.xiaodianshi.tv.yst.provider.xpref]:
- Provider{79140e com.xiaodianshi.tv.yst/com.bilibili.xpref.XprefProvider}
- applicationInfo=ApplicationInfo{3715141 com.xiaodianshi.tv.yst}
- [com.xiaodianshi.tv.yst.fileprovider]:
- Provider{159b7d3 com.xiaodianshi.tv.yst/androidx.core.content.FileProvider}
- applicationInfo=ApplicationInfo{3715141 com.xiaodianshi.tv.yst}
- [com.xiaodianshi.tv.yst.lifecycle-process]:
- Provider{216ddc2 com.xiaodianshi.tv.yst/androidx.lifecycle.ProcessLifecycleO
- wnerInitializer}
- applicationInfo=ApplicationInfo{3715141 com.xiaodianshi.tv.yst}
- [com.xiaodianshi.tv.yst.provider.modimage]:
- Provider{22f9dc5 com.xiaodianshi.tv.yst/com.bilibili.app.lib.modx.ModImageCo
- ntentProvider}
- applicationInfo=ApplicationInfo{3715141 com.xiaodianshi.tv.yst}
- [com.xiaodianshi.tv.yst.provider.modresource]:
- Provider{3c36a09 com.xiaodianshi.tv.yst/com.bilibili.lib.mod.ModResourceProv
- ider}
- applicationInfo=ApplicationInfo{3715141 com.xiaodianshi.tv.yst}
- [com.xiaodianshi.tv.yst.provider.resolver]:
- Provider{a403a0d com.xiaodianshi.tv.yst/com.bilibili.lib.media.resolver.reso
- lve.MediaResolveProvider}
- applicationInfo=ApplicationInfo{3715141 com.xiaodianshi.tv.yst}
- [com.xiaodianshi.tv.yst.okdownloader.provider]:
- Provider{967bf10 com.xiaodianshi.tv.yst/com.bilibili.lib.okdownloader.intern
- al.db.DownloadDatabaseProvider}
- applicationInfo=ApplicationInfo{3715141 com.xiaodianshi.tv.yst}
- [com.xiaodianshi.tv.yst.coocaa.history]:
- Provider{bb6631a com.xiaodianshi.tv.yst/com.coocaa.historylib.HistoryContent
- Provider}
- applicationInfo=ApplicationInfo{3715141 com.xiaodianshi.tv.yst}
- [com.xiaodianshi.tv.yst.coocaa.collect]:
- Provider{ef64e4b com.xiaodianshi.tv.yst/com.coocaa.historylib.CollectContent
- Provider}
- applicationInfo=ApplicationInfo{3715141 com.xiaodianshi.tv.yst}
- [com.xiaodianshi.tv.yst.provider.TvSearchSuggestionProvider]:
- Provider{67d7ca4 com.xiaodianshi.tv.yst/.provider.TvSearchSuggestionProvider
- }
- applicationInfo=ApplicationInfo{3715141 com.xiaodianshi.tv.yst}
- [com.xiaodianshi.tv.yst.provider.InfraInitProvider]:
- Provider{3bc6028 com.xiaodianshi.tv.yst/com.bilibili.infra.base.provider.Inf
- raInitProvider}
- applicationInfo=ApplicationInfo{3715141 com.xiaodianshi.tv.yst}
- [com.xiaodianshi.tv.yst.provider.IPCActivityStateProvider]:
- Provider{87dfe2f com.xiaodianshi.tv.yst/com.bilibili.base.ipc.IPCActivitySta
- teProvider}
- applicationInfo=ApplicationInfo{3715141 com.xiaodianshi.tv.yst}
- [com.xiaodianshi.tv.yst.provider.auth]:
- Provider{871bc3c com.xiaodianshi.tv.yst/com.bilibili.lib.account.AuthProvide
- r}
- applicationInfo=ApplicationInfo{3715141 com.xiaodianshi.tv.yst}
- [com.xiaodianshi.tv.yst]
- Package [com.xiaodianshi.tv.yst] (7e85f37):
- pkg=Package{74796e6 com.xiaodianshi.tv.yst}
- codePath=/data/app/com.xiaodianshi.tv.yst-Gq1cdiX3Aho20N4EPrC5gw==
- resourcePath=/data/app/com.xiaodianshi.tv.yst-Gq1cdiX3Aho20N4EPrC5gw==
- legacyNativeLibraryDir=/data/app/com.xiaodianshi.tv.yst-Gq1cdiX3Aho20N4EPrC5
- gw==/lib
- applicationInfo=ApplicationInfo{3715141 com.xiaodianshi.tv.yst}
- dataDir=/data/user_de/0/com.xiaodianshi.tv.yst
- com.xiaodianshi.tv.yst.permission.BLKV: prot=signature, INSTALLED
- com.xiaodianshi.tv.yst.permission.BLKV
- com.xiaodianshi.tv.yst.permission.BLKV: granted=true
- [com.xiaodianshi.tv.yst]
- path: /data/app/com.xiaodianshi.tv.yst-Gq1cdiX3Aho20N4EPrC5gw==/base.apk
- [com.xiaodianshi.tv.yst]
- cmcc_jiangsu:/ #
没想到运气这么好 才试了第一个就成功了:
- cmcc_jiangsu:/ # am start com.xiaodianshi.tv.yst/.ui.transition.TransitionActivity
- Starting: Intent { act=android.intent.action.MAIN cat=[android.intent.category.L
- AUNCHER] cmp=com.xiaodianshi.tv.yst/.ui.transition.TransitionActivity }
- cmcc_jiangsu:/ # screencap -p /sdcard/sc/1.png
- screencap 3
- screencap start. screen_type: 1
- file path: /sdcard/sc/1.png
- new ScreenCatch ok
- got video+osd data: 1280 x 720
- SkEncodeImage success
- screencap end
- cmcc_jiangsu:/ #
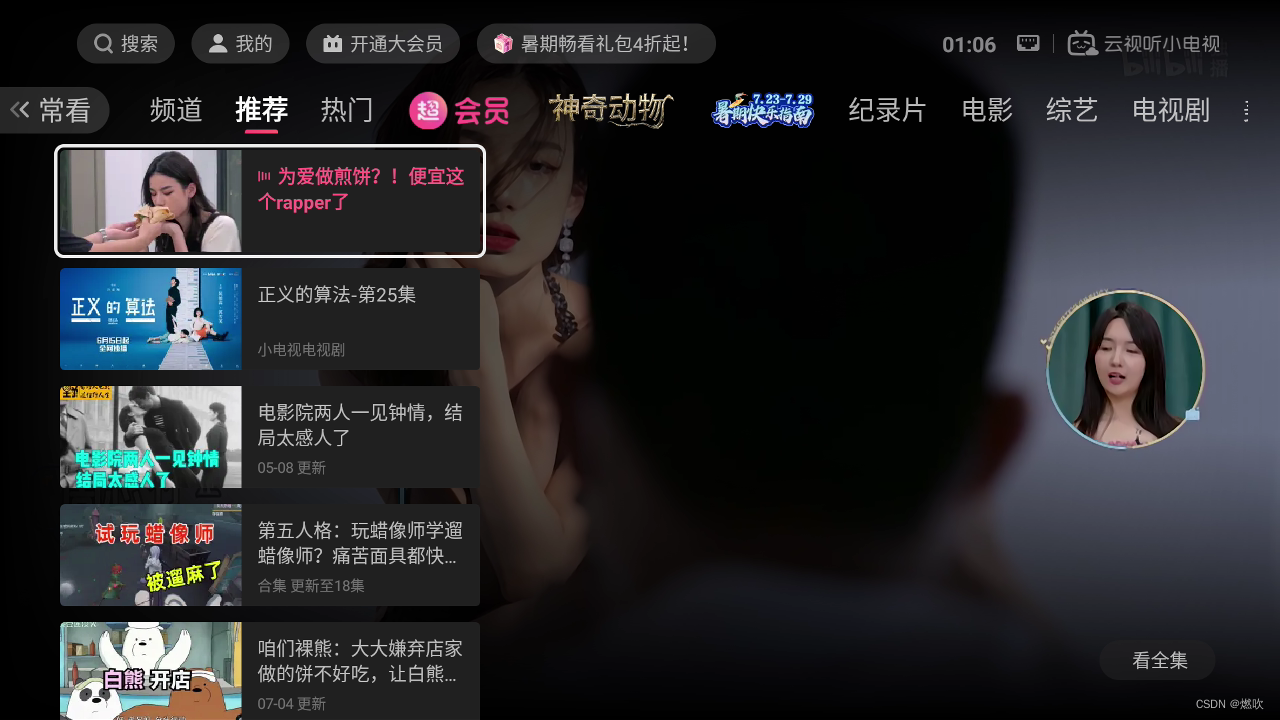
##################################################
使用 pm 应用管理工具
——————————
pm 简介
pm 是 包管理/package manager 简拼
可以使用 pm 工具来执行应用的安装 或查询应用的信息、系统权限、控制应用
pm 工具是 Android 开发与测试过程中必不可少的工具
%%%%%
应用安装与数据文件的位置不同
App 的文件存储和数据目录在不同用户下都是独立的:
/data/user/0 root 用户内部存储位置
/storage/emulated/0/ root 用户外部存储位置
但是同一个 APP 在多用户下却只有一个安装目录:
/data/app 第三方软件安装位置 这是普通用户安装的软件
/system/app 系统预装软件位置 这是系统自带的 app
/system/priv-app 特权 app 位置 这是系统级别的应用
示例请看注释:
- cmcc_jiangsu:/ # ls /data/user/0/ /* root 用户的应用数据存储位置 */
- android com.android.sharedstoragebackup
- android.ext.services com.android.shell
- android.ext.shared com.android.statementservice
- com.android.backupconfirm com.android.superuser
- com.android.bluetooth com.android.systemui
- com.android.certinstaller com.android.vpndialogs
- com.android.companiondevicemanager com.android.webview
- com.android.defcontainer com.cmcc.mid.softdetector
- com.android.externalstorage com.dangbei.tvlauncher
- com.android.inputdevices com.dangbeimarket
- com.android.inputmethod.latin com.droidlogic
- com.android.keychain com.droidlogic.BluetoothRemote
- com.android.location.fused com.droidlogic.inputmethod.remote
- com.android.managedprovisioning com.fengyun.live
- com.android.packageinstaller com.iflytek.bt.auto
- com.android.pacprocessor com.iflytek.xiri
- com.android.providers.downloads com.iflytek.xiri2.system
- com.android.providers.media com.mylejia.store
- com.android.providers.settings com.tv.kuaisou
- com.android.proxyhandler com.xiaodianshi.tv.yst
- com.android.se jackpal.androidterm
- com.android.settings me.thomastv.rebootupdate
- cmcc_jiangsu:/ # ls /data/user/0/com.android.settings/ -alh /* com.android.settings 的数据目录 */
- total 14K
- drwx------ 6 system system 4.0K 2015-01-01 08:00 .
- drwxrwx--x 46 system system 4.0K 2022-07-25 11:24 ..
- drwxrws--x 2 system system 4.0K 2015-01-01 08:00 cache
- drwxrws--x 2 system system 4.0K 2015-01-01 08:00 code_cache
- drwxrwx--x 2 system system 4.0K 2015-01-01 08:00 files
- lrwxrwxrwx 1 root root 52 2015-01-01 08:00 lib -> /system/app/SkySettingA
- 9_jiangsuCMCC_release/lib/arm
- drwxrwx--x 2 system system 4.0K 2022-07-25 11:29 shared_prefs
- cmcc_jiangsu:/ # ls /data/app /* 用户安装的第三方应用 */
- com.dangbeimarket-GvchZCDlwKegHBtoXBQhwg==
- com.fengyun.live-829NViyOdL42DNDyYJhxWw==
- com.iflytek.xiri-WgYGkZvi6pwHhlca9dWSJw==
- com.mylejia.store--X53YUFZXKN1XMhyN9prZw==
- com.tv.kuaisou-fI0vFrNXcO_5RNCnl5c-7A==
- com.xiaodianshi.tv.yst-KrOFFpsDIBXvgmut74jw_Q==
- jackpal.androidterm-sAgHElvcbHuZtUuQdCSIdQ==
- me.thomastv.rebootupdate-4SVHakbq9YXs3X7ozxyY0w==
- cmcc_jiangsu:/ # ls /system/app /* 系统预装应用 */
- Bluetooth
- BtAutoConn_release_9.0_V1.0_19_20210827_chinamobile
- CertInstaller
- CompanionDeviceManager
- Dangbei2.apk
- ExtShared
- GDYD-IPTVSettings-AN9-ALL-DEBUG-1.0.0-20210805-1058.apk
- KeyChain
- LatinIME
- PacProcessor
- SecureElement
- SkySettingA9_jiangsuCMCC_release
- SoftDetector_V5.1.0_20210721_35101_x025_encrypt
- Superuser
- SystemXiri_release-2.0.4-unsigned_signed_Aligned
- Tr069_Service.apk
- TvSettings
- xiri
- cmcc_jiangsu:/ # ls /system/priv-app /* 系统特权应用 */
- BackupRestoreConfirmation ManagedProvisioning Shell
- DefaultContainerService MediaProvider SkySettings
- DownloadProvider PackageInstaller StatementService
- ExtServices ProxyHandler SystemUI
- ExternalStorageProvider Settings VpnDialogs
- FusedLocation SettingsProvider
- InputDevices SharedStorageBackup
- cmcc_jiangsu:/ #
%%%%%
查看包的系统状态信息
语法:
pm dump 子命令 包名子命令:
- pm dump package [包名] /* 打印服务信息 */
- pm dump activity [包名] /* 打印 Activity 信息 */
- pm dump meminfo [包名] /* 打印当前内存使用信息 */
- pm dump procstats [包名] /* 打印系统内存使用与一段时间内存汇总 */
- pm dump usagestats [包名] /* 打印服务器使用状态信息 */
- pm dump batterystats [包名] /* 打印电池状态信息 */
不过我的盒子总报错 只好使用 dumpsys 命令:
- dumpsys package [包名] /* 打印服务信息 */
- dumpsys activity [包名] /* 打印 Activity 信息 */
- dumpsys meminfo [包名] /* 打印当前内存使用信息 */
- dumpsys procstats [包名] /* 打印系统内存使用与一段时间内存汇总 */
- dumpsys usagestats [包名] /* 打印服务器使用状态信息 */
- dumpsys batterystats [包名] /* 打印电池状态信息 */
示例查看 终端模拟器 的包信息:
- cmcc_jiangsu:/ # dumpsys package jackpal.androidterm
- Activity Resolver Table:
- Full MIME Types:
- */*:
- 2c3ec43 jackpal.androidterm/.TermHere filter 4201189
- Action: "android.intent.action.SEND"
- Category: "android.intent.category.DEFAULT"
- Type: "*"
- mPriority=0, mOrder=0, mHasPartialTypes=true
- e3a32c0 jackpal.androidterm/.shortcuts.FSNavigator filter 801b9cb
- Action: "android.intent.action.GET_CONTENT"
- Category: "android.intent.category.DEFAULT"
- Category: "android.intent.category.OPENABLE"
- Type: "*"
- mPriority=0, mOrder=0, mHasPartialTypes=true
-
- Wild MIME Types:
- *:
- 2c3ec43 jackpal.androidterm/.TermHere filter 4201189
- Action: "android.intent.action.SEND"
- Category: "android.intent.category.DEFAULT"
- Type: "*"
- mPriority=0, mOrder=0, mHasPartialTypes=true
- e3a32c0 jackpal.androidterm/.shortcuts.FSNavigator filter 801b9cb
- Action: "android.intent.action.GET_CONTENT"
- Category: "android.intent.category.DEFAULT"
- Category: "android.intent.category.OPENABLE"
- Type: "*"
- mPriority=0, mOrder=0, mHasPartialTypes=true
-
- Non-Data Actions:
- jackpal.androidterm.RUN_SHORTCUT:
- abe4bf9 jackpal.androidterm/.RunShortcut filter a41b1af
- Action: "jackpal.androidterm.RUN_SHORTCUT"
- Category: "android.intent.category.DEFAULT"
- jackpal.androidterm.private.SWITCH_WINDOW:
- 9c2673e jackpal.androidterm/.TermInternal filter 7613353
- Action: "jackpal.androidterm.private.SWITCH_WINDOW"
- Category: "android.intent.category.DEFAULT"
- jackpal.androidterm.OPEN_NEW_WINDOW:
- b2f099f jackpal.androidterm/.RemoteInterface filter 7385490
- Action: "jackpal.androidterm.OPEN_NEW_WINDOW"
- Category: "android.intent.category.DEFAULT"
- android.intent.action.MAIN:
- 7efbaec jackpal.androidterm/.Term filter b79698d
- Action: "android.intent.action.MAIN"
- Category: "android.intent.category.LAUNCHER"
- Category: "android.intent.category.MULTIWINDOW_LAUNCHER"
- a8eaeb5 jackpal.androidterm/.shortcuts.AddShortcut filter e7629bc
- Action: "android.intent.action.MAIN"
- android.intent.action.PICK:
- e3a32c0 jackpal.androidterm/.shortcuts.FSNavigator filter 8664c9a
- Action: "android.intent.action.PICK"
- Category: "android.intent.category.DEFAULT"
- jackpal.androidterm.RUN_SCRIPT:
- cf9b94a jackpal.androidterm/.RunScript filter ff5658e
- Action: "jackpal.androidterm.RUN_SCRIPT"
- Category: "android.intent.category.DEFAULT"
- jackpal.androidterm.private.OPEN_NEW_WINDOW:
- 9c2673e jackpal.androidterm/.TermInternal filter e91742
- Action: "jackpal.androidterm.private.OPEN_NEW_WINDOW"
- Category: "android.intent.category.DEFAULT"
- android.intent.action.CREATE_SHORTCUT:
- a8eaeb5 jackpal.androidterm/.shortcuts.AddShortcut filter c6f3d45
- Action: "android.intent.action.CREATE_SHORTCUT"
-
- MIME Typed Actions:
- android.intent.action.SEND:
- 2c3ec43 jackpal.androidterm/.TermHere filter 4201189
- Action: "android.intent.action.SEND"
- Category: "android.intent.category.DEFAULT"
- Type: "*"
- mPriority=0, mOrder=0, mHasPartialTypes=true
- android.intent.action.GET_CONTENT:
- e3a32c0 jackpal.androidterm/.shortcuts.FSNavigator filter 801b9cb
- Action: "android.intent.action.GET_CONTENT"
- Category: "android.intent.category.DEFAULT"
- Category: "android.intent.category.OPENABLE"
- Type: "*"
- mPriority=0, mOrder=0, mHasPartialTypes=true
-
- Service Resolver Table:
- Non-Data Actions:
- jackpal.androidterm.action.START_TERM.v1:
- 604a0bb jackpal.androidterm/.TermService filter 427ba24
- Action: "jackpal.androidterm.action.START_TERM.v1"
- Category: "android.intent.category.DEFAULT"
-
- Permissions:
- Permission [jackpal.androidterm.permission.PREPEND_TO_PATH] (49399d8):
- sourcePackage=jackpal.androidterm
- uid=10031 gids=null type=0 prot=dangerous
- perm=Permission{c88131 jackpal.androidterm.permission.PREPEND_TO_PATH}
- packageSetting=PackageSetting{9a22016 jackpal.androidterm/10031}
-
- Permissions:
- Permission [jackpal.androidterm.permission.RUN_SCRIPT] (6d28d97):
- sourcePackage=jackpal.androidterm
- uid=10031 gids=null type=0 prot=dangerous
- perm=Permission{8947b84 jackpal.androidterm.permission.RUN_SCRIPT}
- packageSetting=PackageSetting{9a22016 jackpal.androidterm/10031}
-
- Permissions:
- Permission [jackpal.androidterm.permission.APPEND_TO_PATH] (f2ff6d):
- sourcePackage=jackpal.androidterm
- uid=10031 gids=null type=0 prot=dangerous
- perm=Permission{c9827a2 jackpal.androidterm.permission.APPEND_TO_PATH}
- packageSetting=PackageSetting{9a22016 jackpal.androidterm/10031}
-
- Key Set Manager:
- [jackpal.androidterm]
- Signing KeySets: 17
-
- Packages:
- Package [jackpal.androidterm] (9a22016):
- userId=10031
- pkg=Package{2286c33 jackpal.androidterm}
- codePath=/data/app/jackpal.androidterm-sAgHElvcbHuZtUuQdCSIdQ==
- resourcePath=/data/app/jackpal.androidterm-sAgHElvcbHuZtUuQdCSIdQ==
- legacyNativeLibraryDir=/data/app/jackpal.androidterm-sAgHElvcbHuZtUuQdCSIdQ=
- =/lib
- primaryCpuAbi=armeabi
- secondaryCpuAbi=null
- versionCode=71 minSdk=4 targetSdk=22
- versionName=1.0.70
- splits=[base]
- apkSigningVersion=1
- applicationInfo=ApplicationInfo{e9fcbf0 jackpal.androidterm}
- flags=[ HAS_CODE ALLOW_CLEAR_USER_DATA ALLOW_BACKUP ]
- privateFlags=[ DEFAULT_TO_DEVICE_PROTECTED_STORAGE DIRECT_BOOT_AWARE ]
- dataDir=/data/user_de/0/jackpal.androidterm
- supportsScreens=[small, medium, large, xlarge, resizeable, anyDensity]
- usesLibraries:
- org.apache.http.legacy
- usesLibraryFiles:
- /system/framework/org.apache.http.legacy.boot.jar
- timeStamp=2022-07-23 23:53:02
- firstInstallTime=2022-07-23 23:53:02
- lastUpdateTime=2022-07-23 23:53:02
- signatures=PackageSignatures{5cd2569 version:1, signatures:[e7b54ff0], past
- signatures:[]}
- installPermissionsFixed=true
- pkgFlags=[ HAS_CODE ALLOW_CLEAR_USER_DATA ALLOW_BACKUP ]
- declared permissions:
- jackpal.androidterm.permission.RUN_SCRIPT: prot=dangerous, INSTALLED
- jackpal.androidterm.permission.APPEND_TO_PATH: prot=dangerous, INSTALLED
- jackpal.androidterm.permission.PREPEND_TO_PATH: prot=dangerous, INSTALLED
- requested permissions:
- android.permission.INTERNET
- android.permission.READ_EXTERNAL_STORAGE
- android.permission.WRITE_EXTERNAL_STORAGE
- android.permission.ACCESS_SUPERUSER
- android.permission.WAKE_LOCK
- install permissions:
- android.permission.INTERNET: granted=true
- android.permission.READ_EXTERNAL_STORAGE: granted=true
- android.permission.WRITE_EXTERNAL_STORAGE: granted=true
- android.permission.WAKE_LOCK: granted=true
- User 0: ceDataInode=-4294966708 installed=true hidden=false suspended=false
- stopped=false notLaunched=false enabled=0 instant=false virtual=false
- gids=[3003]
- runtime permissions:
-
- Package Changes:
- Sequence number=0
-
-
- Dexopt state:
- [jackpal.androidterm]
- path: /data/app/jackpal.androidterm-sAgHElvcbHuZtUuQdCSIdQ==/base.apk
- arm: [status=speed-profile] [reason=install]
-
-
- Compiler stats:
- [jackpal.androidterm]
- (No recorded stats)
- cmcc_jiangsu:/ #
示例查看进程中的 sh 信息:
- cmcc_jiangsu:/ # dumpsys procstats sh
- CURRENT STATS:
- System memory usage:
- SOn /Norm: 1 samples:
- Cached: 176MB min, 176MB avg, 176MB max
- Free: 705MB min, 705MB avg, 705MB max
- ZRam: 12KB min, 12KB avg, 12KB max
- Kernel: 145MB min, 145MB avg, 145MB max
- Native: 388MB min, 388MB avg, 388MB max
- Low : 1 samples:
- Cached: 136MB min, 136MB avg, 136MB max
- Free: 860MB min, 860MB avg, 860MB max
- ZRam: 0.00 min, 0.00 avg, 0.00 max
- Kernel: 129MB min, 129MB avg, 129MB max
- Native: 311MB min, 311MB avg, 311MB max
-
- Summary:
-
- Run time Stats:
- SOn /Norm: +36m9s929ms (running)
- Mod : +24s266ms
- Low : +5s211ms
- Crit: +4s583ms
- TOTAL: +36m43s989ms
-
- Memory usage:
- Kernel : 137MB (16 samples)
- Native : 350MB (16 samples)
- Persist: 154MB (110 samples)
- Top: 121MB (35 samples)
- ImpFg: 134MB (193 samples)
- ImpBg: 7.1MB (15 samples)
- Service: 62MB (168 samples)
- Receivr: 22KB (63 samples)
- LastAct: 466KB (25 samples)
- CchEmty: 117MB (151 samples)
- Cached : 156MB (16 samples)
- Free : 783MB (16 samples)
- Z-Ram : 6.0KB (16 samples)
- TOTAL : 2.0GB
- ServRst: 556KB (28 samples)
-
- PSS collection stats:
- Internal Single: 113x over +6s76ms
- Internal All Procs (Memory Change): 0x over 0
- Internal All Procs (Polling): 2x over +147ms
- External: 0x over 0
- External Slow: 63x over +6s830ms
-
- Start time: 2015-01-01 08:00:10
- Total uptime: +36m44s154ms
- Total elapsed time: +36m44s154ms (partial) (swapped-out-pss) libart.so
-
- Available pages by page size:
- Zone 0 Unmovable 1 0 13 10 17 14 14 9 3
- 2 0
- Zone 0 Movable 0 1 1 1 4 10 3 0 2
- 4 159
- Zone 0 Reclaimable 1 1 0 1 0 1 0 0 1
- 1 0
- Zone 0 HighAtomic 0 0 0 0 0 0 0 0 0
- 0 0
- Zone 0 CMA 0 0 0 0 0 0 0 0 1
- 0 0
- Zone 0 Isolate 0 0 0 0 0 0 0 0 0
- 0 0
- Zone 0 Unmovable 0 1 0 0 1 1 0 0 0
- 1 0
- Zone 0 Movable 1 0 0 1 1 1 1 1 1
- 0 66
- Zone 0 Reclaimable 0 0 0 0 0 0 0 0 0
- 0 0
- Zone 0 HighAtomic 0 0 0 0 0 0 0 0 0
- 0 0
- Zone 0 CMA 3 3 3 1 4 0 1 0 1
- 1 148
- Zone 0 Isolate 0 0 0 0 0 0 0 0 0
- 0 0
-
- AGGREGATED OVER LAST 24 HOURS:
- System memory usage:
- SOn /Norm: 8 samples:
- Cached: 168MB min, 275MB avg, 340MB max
- Free: 463MB min, 639MB avg, 893MB max
- ZRam: 0.00 min, 9.0KB avg, 12KB max
- Kernel: 125MB min, 140MB avg, 149MB max
- Native: 338MB min, 380MB avg, 407MB max
- Low : 2 samples:
- Cached: 136MB min, 233MB avg, 330MB max
- Free: 568MB min, 714MB avg, 860MB max
- ZRam: 0.00 min, 6.0KB avg, 12KB max
- Kernel: 129MB min, 135MB avg, 142MB max
- Native: 311MB min, 358MB avg, 405MB max
-
- Summary:
-
- Run time Stats:
- SOn /Norm: +5h52m19s853ms
- Mod : +22m13s287ms
- Low : +2h0m22s180ms
- Crit: +4s583ms
- TOTAL: +8h14m59s903ms
-
- Memory usage:
- Kernel : 140MB (78 samples)
- Native : 379MB (78 samples)
- Persist: 157MB (241 samples)
- Top: 128MB (88 samples)
- ImpFg: 123MB (1195 samples)
- ImpBg: 13MB (40 samples)
- Service: 49MB (947 samples)
- Receivr: 4.0KB (422 samples)
- LastAct: 373KB (72 samples)
- CchAct: 14MB (17 samples)
- CchEmty: 79MB (391 samples)
- Cached : 272MB (78 samples)
- Free : 643MB (78 samples)
- Z-Ram : 8.7KB (78 samples)
- TOTAL : 1.9GB
- ServRst: 48KB (89 samples)
-
- PSS collection stats:
- Internal Single: 315x over +17s246ms
- Internal All Procs (Memory Change): 81x over +3s988ms
- Internal All Procs (Polling): 63x over +3s189ms
- External: 0x over 0
- External Slow: 519x over +1m2s809ms
-
- Start time: 2015-01-01 08:00:10
- Total uptime: +8h15m0s252ms
- Total elapsed time: +8h15m0s253ms (partial) (swapped-out-pss) libart.so
-
- Available pages by page size:
- Zone 0 Unmovable 1 0 13 10 17 14 14 9 3
- 2 0
- Zone 0 Movable 0 1 1 1 4 10 3 0 2
- 4 159
- Zone 0 Reclaimable 1 1 0 1 0 1 0 0 1
- 1 0
- Zone 0 HighAtomic 0 0 0 0 0 0 0 0 0
- 0 0
- Zone 0 CMA 0 0 0 0 0 0 0 0 1
- 0 0
- Zone 0 Isolate 0 0 0 0 0 0 0 0 0
- 0 0
- Zone 0 Unmovable 0 1 0 0 1 1 0 0 0
- 1 0
- Zone 0 Movable 1 0 0 1 1 1 1 1 1
- 0 66
- Zone 0 Reclaimable 0 0 0 0 0 0 0 0 0
- 0 0
- Zone 0 HighAtomic 0 0 0 0 0 0 0 0 0
- 0 0
- Zone 0 CMA 3 3 3 1 4 0 1 0 1
- 1 148
- Zone 0 Isolate 0 0 0 0 0 0 0 0 0
- 0 0
-
- AGGREGATED OVER LAST 3 HOURS:
- System memory usage:
- SOn /Norm: 1 samples:
- Cached: 176MB min, 176MB avg, 176MB max
- Free: 705MB min, 705MB avg, 705MB max
- ZRam: 12KB min, 12KB avg, 12KB max
- Kernel: 145MB min, 145MB avg, 145MB max
- Native: 388MB min, 388MB avg, 388MB max
- Low : 2 samples:
- Cached: 136MB min, 233MB avg, 330MB max
- Free: 568MB min, 714MB avg, 860MB max
- ZRam: 0.00 min, 6.0KB avg, 12KB max
- Kernel: 129MB min, 135MB avg, 142MB max
- Native: 311MB min, 358MB avg, 405MB max
-
- Summary:
-
- Run time Stats:
- SOn /Norm: +36m9s997ms
- Mod : +24s266ms
- Low : +2h0m21s599ms
- Crit: +4s583ms
- TOTAL: +2h37m0s445ms
-
- Memory usage:
- Kernel : 139MB (24 samples)
- Native : 368MB (24 samples)
- Persist: 155MB (129 samples)
- Top: 143MB (29 samples)
- ImpFg: 154MB (414 samples)
- ImpBg: 17MB (14 samples)
- Service: 73MB (314 samples)
- Receivr: 5.1KB (81 samples)
- LastAct: 109KB (29 samples)
- CchEmty: 65MB (151 samples)
- Cached : 214MB (24 samples)
- Free : 711MB (24 samples)
- Z-Ram : 8.0KB (24 samples)
- TOTAL : 2.0GB
- ServRst: 139KB (37 samples)
-
- PSS collection stats:
- Internal Single: 136x over +7s324ms
- Internal All Procs (Memory Change): 0x over 0
- Internal All Procs (Polling): 23x over +1s208ms
- External: 0x over 0
- External Slow: 183x over +21s381ms
-
- Start time: 2015-01-01 08:00:10
- Total uptime: +2h37m0s615ms
- Total elapsed time: +2h37m0s615ms (partial) (swapped-out-pss) libart.so
-
- Available pages by page size:
- Zone 0 Unmovable 1 0 13 10 17 14 14 9 3
- 2 0
- Zone 0 Movable 0 1 1 1 4 10 3 0 2
- 4 159
- Zone 0 Reclaimable 1 1 0 1 0 1 0 0 1
- 1 0
- Zone 0 HighAtomic 0 0 0 0 0 0 0 0 0
- 0 0
- Zone 0 CMA 0 0 0 0 0 0 0 0 1
- 0 0
- Zone 0 Isolate 0 0 0 0 0 0 0 0 0
- 0 0
- Zone 0 Unmovable 0 1 0 0 1 1 0 0 0
- 1 0
- Zone 0 Movable 1 0 0 1 1 1 1 1 1
- 0 66
- Zone 0 Reclaimable 0 0 0 0 0 0 0 0 0
- 0 0
- Zone 0 HighAtomic 0 0 0 0 0 0 0 0 0
- 0 0
- Zone 0 CMA 3 3 3 1 4 0 1 0 1
- 1 148
- Zone 0 Isolate 0 0 0 0 0 0 0 0 0
- 0 0
- cmcc_jiangsu:/ #
%%%%%
查看系统功能与支持库信息
查看系统功能:
pm list feature /* 打印系统的所有功能/列出所有硬件相关信息 */查看支持库信息:
pm list libraries /* 打印当前设备所支持的所有库 */示例查看支持库:
- cmcc_jiangsu:/ # pm list libraries
- library:android.ext.services
- library:android.ext.shared
- library:android.test.base
- library:android.test.mock
- library:android.test.runner
- library:com.android.future.usb.accessory
- library:com.android.location.provider
- library:com.android.media.remotedisplay
- library:com.android.mediadrm.signer
- library:droidlogic.software.core
- library:droidlogic.tv.software.core
- library:javax.obex
- library:org.apache.http.legacy
- cmcc_jiangsu:/ #
%%%%%
测试包与 APK 路径查询
测试包:
- pm list instrymentation /* 列出所有的 instrumentation 测试包 */
- pm list instrymentation 包名 /* 指定某个 app 的测试包 */
- pm list instrymentation -f /* 列出 apk 文件位置 */
APK 路径查询:
pm path 包名 /* 列出指定包的 APK 路径 */示例:
- cmcc_jiangsu:/ # pm path jackpal.androidterm
- package:/data/app/jackpal.androidterm-sAgHElvcbHuZtUuQdCSIdQ==/base.apk
- cmcc_jiangsu:/ #
——————————
查询
%%%%%
常用查询语法及常用参数
pm 查询语法:
pm list packages 参数 包名pm 查询常用参数:
- -i 查看应用的安装者
-
- -f 显示每个包的文件位置
-
- -d 搭配过滤器 只显示禁用的应用的包名
- -e 搭配过滤器 只显示可用的应用的包名
- -s 搭配过滤器 只显示系统应用的包名
- -3 搭配过滤器 只显示第三方应用的包名
%%%%%
列出所有包
- cmcc_jiangsu:/tmp # pm list packages
- package:com.iflytek.xiri
- package:com.droidlogic.inputmethod.remote
- package:com.android.providers.media
- package:com.mylejia.store
- package:com.android.externalstorage
- package:com.android.companiondevicemanager
- package:com.android.providers.downloads
- package:com.fengyun.live
- package:com.droidlogic
- package:com.dangbei.tvlauncher
- package:com.android.defcontainer
- package:com.android.pacprocessor
- package:com.android.certinstaller
- package:me.thomastv.rebootupdate
- package:android
- package:com.android.backupconfirm
- package:com.android.statementservice
- package:com.android.superuser
- package:com.android.providers.settings
- package:com.android.sharedstoragebackup
- package:com.iflytek.xiri2.system
- package:com.android.webview
- package:com.android.se
- package:com.android.inputdevices
- package:com.droidlogic.BluetoothRemote
- package:android.ext.shared
- package:com.android.keychain
- package:android.ext.services
- package:com.android.packageinstaller
- package:com.android.proxyhandler
- package:com.android.inputmethod.latin
- package:com.android.managedprovisioning
- package:com.iflytek.bt.auto
- package:com.android.settings
- package:com.android.vpndialogs
- package:com.android.shell
- package:com.dangbeimarket
- package:com.android.location.fused
- package:com.android.systemui
- package:com.android.bluetooth
- package:com.cmcc.mid.softdetector
- cmcc_jiangsu:/tmp #
%%%%%
-i 查看包的安装者
- cmcc_jiangsu:/tmp # pm list packages -i
- package:com.iflytek.xiri installer=null
- package:com.droidlogic.inputmethod.remote installer=null
- package:com.android.providers.media installer=null
- package:com.mylejia.store installer=null
- package:com.android.externalstorage installer=null
- package:com.android.companiondevicemanager installer=null
- package:com.android.providers.downloads installer=null
- package:com.fengyun.live installer=null
- package:com.droidlogic installer=null
- package:com.dangbei.tvlauncher installer=null
- package:com.android.defcontainer installer=null
- package:com.android.pacprocessor installer=null
- package:com.android.certinstaller installer=null
- package:me.thomastv.rebootupdate installer=null
- package:android installer=null
- package:com.android.backupconfirm installer=null
- package:com.android.statementservice installer=null
- package:com.android.superuser installer=null
- package:com.android.providers.settings installer=null
- package:com.android.sharedstoragebackup installer=null
- package:com.iflytek.xiri2.system installer=null
- package:com.android.webview installer=null
- package:com.android.se installer=null
- package:com.android.inputdevices installer=null
- package:com.droidlogic.BluetoothRemote installer=null
- package:android.ext.shared installer=null
- package:com.android.keychain installer=null
- package:android.ext.services installer=null
- package:com.android.packageinstaller installer=null
- package:com.android.proxyhandler installer=null
- package:com.android.inputmethod.latin installer=null
- package:com.android.managedprovisioning installer=null
- package:com.iflytek.bt.auto installer=null
- package:com.android.settings installer=null
- package:com.android.vpndialogs installer=null
- package:com.android.shell installer=null
- package:com.dangbeimarket installer=null
- package:com.android.location.fused installer=null
- package:com.android.systemui installer=null
- package:com.android.bluetooth installer=null
- package:com.cmcc.mid.softdetector installer=null
- cmcc_jiangsu:/tmp #
%%%%%
-u 列出包和未安装包信息
- cmcc_jiangsu:/tmp # pm list packages -u
- package:com.iflytek.xiri
- package:com.droidlogic.inputmethod.remote
- package:com.android.providers.media
- package:com.mylejia.store
- package:com.android.externalstorage
- package:com.android.companiondevicemanager
- package:com.android.providers.downloads
- package:com.fengyun.live
- package:com.droidlogic
- package:com.dangbei.tvlauncher
- package:com.android.defcontainer
- package:com.android.pacprocessor
- package:com.android.certinstaller
- package:me.thomastv.rebootupdate
- package:android
- package:com.android.backupconfirm
- package:com.android.statementservice
- package:com.android.superuser
- package:com.android.providers.settings
- package:com.android.sharedstoragebackup
- package:com.iflytek.xiri2.system
- package:com.android.webview
- package:com.android.se
- package:com.android.inputdevices
- package:com.droidlogic.BluetoothRemote
- package:android.ext.shared
- package:com.android.keychain
- package:android.ext.services
- package:com.android.packageinstaller
- package:com.android.proxyhandler
- package:com.android.inputmethod.latin
- package:com.android.managedprovisioning
- package:com.iflytek.bt.auto
- package:com.android.settings
- package:com.android.vpndialogs
- package:com.android.shell
- package:com.dangbeimarket
- package:com.android.location.fused
- package:com.android.systemui
- package:com.android.bluetooth
- package:com.cmcc.mid.softdetector
- cmcc_jiangsu:/tmp #
%%%%%
-e 列出启用包
- cmcc_jiangsu:/tmp # pm list packages -e
- package:com.iflytek.xiri
- package:com.droidlogic.inputmethod.remote
- package:com.android.providers.media
- package:com.mylejia.store
- package:com.android.externalstorage
- package:com.android.companiondevicemanager
- package:com.android.providers.downloads
- package:com.fengyun.live
- package:com.droidlogic
- package:com.dangbei.tvlauncher
- package:com.android.defcontainer
- package:com.android.pacprocessor
- package:com.android.certinstaller
- package:me.thomastv.rebootupdate
- package:android
- package:com.android.backupconfirm
- package:com.android.statementservice
- package:com.android.superuser
- package:com.android.providers.settings
- package:com.android.sharedstoragebackup
- package:com.iflytek.xiri2.system
- package:com.android.webview
- package:com.android.se
- package:com.android.inputdevices
- package:com.droidlogic.BluetoothRemote
- package:android.ext.shared
- package:com.android.keychain
- package:android.ext.services
- package:com.android.packageinstaller
- package:com.android.proxyhandler
- package:com.android.inputmethod.latin
- package:com.android.managedprovisioning
- package:com.iflytek.bt.auto
- package:com.android.settings
- package:com.android.vpndialogs
- package:com.android.shell
- package:com.dangbeimarket
- package:com.android.location.fused
- package:com.android.systemui
- package:com.android.bluetooth
- package:com.cmcc.mid.softdetector
- cmcc_jiangsu:/tmp #
%%%%%
-d 列出禁用包
- cmcc_jiangsu:/tmp # pm list packages -d
- cmcc_jiangsu:/tmp #
%%%%%
-s 列出系统包
- cmcc_jiangsu:/tmp # pm list packages -s
- package:com.iflytek.xiri
- package:com.droidlogic.inputmethod.remote
- package:com.android.providers.media
- package:com.android.externalstorage
- package:com.android.companiondevicemanager
- package:com.android.providers.downloads
- package:com.droidlogic
- package:com.dangbei.tvlauncher
- package:com.android.defcontainer
- package:com.android.pacprocessor
- package:com.android.certinstaller
- package:android
- package:com.android.backupconfirm
- package:com.android.statementservice
- package:com.android.superuser
- package:com.android.providers.settings
- package:com.android.sharedstoragebackup
- package:com.iflytek.xiri2.system
- package:com.android.webview
- package:com.android.se
- package:com.android.inputdevices
- package:com.droidlogic.BluetoothRemote
- package:android.ext.shared
- package:com.android.keychain
- package:android.ext.services
- package:com.android.packageinstaller
- package:com.android.proxyhandler
- package:com.android.inputmethod.latin
- package:com.android.managedprovisioning
- package:com.iflytek.bt.auto
- package:com.android.settings
- package:com.android.vpndialogs
- package:com.android.shell
- package:com.android.location.fused
- package:com.android.systemui
- package:com.android.bluetooth
- package:com.cmcc.mid.softdetector
- cmcc_jiangsu:/tmp #
%%%%%
-3 列出所有第三方包
- cmcc_jiangsu:/tmp # pm list packages -3
- package:com.mylejia.store
- package:com.fengyun.live
- package:me.thomastv.rebootupdate
- package:com.dangbeimarket
- cmcc_jiangsu:/tmp #
%%%%%
-f 查看包的安装位置
列出包和包相关联的文件:
- cmcc_jiangsu:/tmp # pm list packages -f
- package:/data/app/com.iflytek.xiri-WgYGkZvi6pwHhlca9dWSJw==/base.apk=com.iflytek.xiri
- package:/vendor/app/RemoteIME/RemoteIME.apk=com.droidlogic.inputmethod.remote
- package:/system/priv-app/MediaProvider/MediaProvider.apk=com.android.providers.media
- package:/data/app/com.mylejia.store--X53YUFZXKN1XMhyN9prZw==/base.apk=com.mylejia.store
- package:/system/priv-app/ExternalStorageProvider/ExternalStorageProvider.apk=com.android.externalstorage
- package:/system/app/CompanionDeviceManager/CompanionDeviceManager.apk=com.android.companiondevicemanager
- package:/system/priv-app/DownloadProvider/DownloadProvider.apk=com.android.providers.downloads
- package:/data/app/com.fengyun.live-829NViyOdL42DNDyYJhxWw==/base.apk=com.fengyun.live
- package:/product/priv-app/droidlogic-res/droidlogic-res.apk=com.droidlogic
- package:/system/app/Dangbei2.apk=com.dangbei.tvlauncher
- package:/system/priv-app/DefaultContainerService/DefaultContainerService.apk=com.android.defcontainer
- package:/system/app/PacProcessor/PacProcessor.apk=com.android.pacprocessor
- package:/system/app/CertInstaller/CertInstaller.apk=com.android.certinstaller
- package:/data/app/me.thomastv.rebootupdate-4SVHakbq9YXs3X7ozxyY0w==/base.apk=me.thomastv.rebootupdate
- package:/system/framework/framework-res.apk=android
- package:/system/priv-app/BackupRestoreConfirmation/BackupRestoreConfirmation.apk=com.android.backupconfirm
- package:/system/priv-app/StatementService/StatementService.apk=com.android.statementservice
- package:/system/app/Superuser/Superuser.apk=com.android.superuser
- package:/system/priv-app/SettingsProvider/SettingsProvider.apk=com.android.providers.settings
- package:/system/priv-app/SharedStorageBackup/SharedStorageBackup.apk=com.android.sharedstoragebackup
- package:/system/app/SystemXiri_release-2.0.4-unsigned_signed_Aligned/SystemXiri_release-2.0.4-unsigned_signed_Aligned.apk=com.iflytek.xiri2.system
- package:/product/app/webview/webview.apk=com.android.webview
- package:/system/app/SecureElement/SecureElement.apk=com.android.se
- package:/system/priv-app/InputDevices/InputDevices.apk=com.android.inputdevices
- package:/vendor/app/BluetoothRemote/BluetoothRemote.apk=com.droidlogic.BluetoothRemote
- package:/system/app/ExtShared/ExtShared.apk=android.ext.shared
- package:/system/app/KeyChain/KeyChain.apk=com.android.keychain
- package:/system/priv-app/ExtServices/ExtServices.apk=android.ext.services
- package:/system/priv-app/PackageInstaller/PackageInstaller.apk=com.android.packageinstaller
- package:/system/priv-app/ProxyHandler/ProxyHandler.apk=com.android.proxyhandler
- package:/system/app/LatinIME/LatinIME.apk=com.android.inputmethod.latin
- package:/system/priv-app/ManagedProvisioning/ManagedProvisioning.apk=com.android.managedprovisioning
- package:/system/app/BtAutoConn_release_9.0_V1.0_19_20210827_chinamobile/BtAutoConn_release_9.0_V1.0_19_20210827_chinamobile.apk=com.iflytek.bt.auto
- package:/system/app/SkySettingA9_jiangsuCMCC_release/SkySettingA9_jiangsuCMCC_release.apk=com.android.settings
- package:/system/priv-app/VpnDialogs/VpnDialogs.apk=com.android.vpndialogs
- package:/system/priv-app/Shell/Shell.apk=com.android.shell
- package:/data/app/com.dangbeimarket-GvchZCDlwKegHBtoXBQhwg==/base.apk=com.dangbeimarket
- package:/system/priv-app/FusedLocation/FusedLocation.apk=com.android.location.fused
- package:/system/priv-app/SystemUI/SystemUI.apk=com.android.systemui
- package:/system/app/Bluetooth/Bluetooth.apk=com.android.bluetooth
- package:/system/app/SoftDetector_V5.1.0_20210721_35101_x025_encrypt/SoftDetector_V5.1.0_20210721_35101_x025_encrypt.apk=com.cmcc.mid.softdetector
- cmcc_jiangsu:/tmp #
%%%%%
搜索包
搜索包很简单 在引号中输入包包含的字符 所有匹配的信息都列出来:
- shell@GIONEE_G1605A:/ $ pm list packages "androidterm" /* 寻找包含 androidterm 的包 */
- package:jackpal.androidterm
- shell@GIONEE_G1605A:/ $
也可以根据多个参数配合查找:
- cmcc_jiangsu:/tmp # pm list packages -3 "live" /* 在第三方软件中搜索包含 live 字样的包 */
- package:com.fengyun.live
- cmcc_jiangsu:/tmp #
——————————
卸载
卸载时如果加上 -k 参数表示保留配置和缓存文件:
- pm uninstall -k 应用名 /* 卸载应用且保留数据与缓存 */
- pm uninstall 应用名 /* 如果不加 -k 参数则全部删除 */
卸载安卓预装软件的话我们经常使用该命令:
pm uninstall -k –user 包名示例卸载终端模拟器:
- shell@GIONEE_G1605A:/ $ pm list packages -3
- package:com.uei.quicksetsdk.mtkirmgr
- package:jackpal.androidterm
- package:com.iflytek.translate
- shell@GIONEE_G1605A:/ $ pm uninstall jackpal.androidterm
- Success
- shell@GIONEE_G1605A:/ $ pm list packages -3
- package:com.uei.quicksetsdk.mtkirmgr
- package:com.iflytek.translate
- shell@GIONEE_G1605A:/ $
%%%%%
根据 UID 卸载指定账户应用
还可以卸载指定用户的软件
pm uninstall --user 0 应用 /* 卸载默认用户的 应用 */示例搭配用户 UID 卸载指定软件:
- cmcc_jiangsu:/ # pm list packages -3 /* 查看第三方应用 */
- package:com.xiaodianshi.tv.yst
- package:com.mylejia.store
- package:com.fengyun.live
- package:me.thomastv.rebootupdate
- package:jackpal.androidterm
- package:com.dangbeimarket
- cmcc_jiangsu:/ # pm uninstall --user 0 com.xiaodianshi.tv.yst /* 卸载机主的小破站 */
- Success
- cmcc_jiangsu:/ # pm list packages -3 /* 查看第三方应用 卸载成功 */
- package:com.mylejia.store
- package:com.fengyun.live
- package:me.thomastv.rebootupdate
- package:jackpal.androidterm
- package:com.dangbeimarket
- cmcc_jiangsu:/ #
——————————
安装
需要注意的是 pm install 与 adb install 不同
adb install 安装的 .apk 是在你的电脑上!
而 pm install 安装的 .apk 是存储在你的手机中!
所以手下你需要将 .apk 文件上传到手机目录中 常用的目录如:
/data/local/tmp
安装 apk 最常用的两种方式:
- pm install apk /* 安装指定 apk */
- pm install -r APK /* -r 参数表示重新安装指定 apk 会保留应用数据 */
其她参数 可能以后会用到:
- -l 锁定应用程序
- -t 允许测试 apk 被安装
- -i 指定安装包的包名!!!
- -s 安装到 sd 卡
- -f 默认安装到系统内置存储中
- -d 允许降级安装 同一应用低级换高级
示例安装终端模拟器:
- cmcc_jiangsu:/ # pm list packages -3
- package:com.xiaodianshi.tv.yst
- package:com.mylejia.store
- package:com.fengyun.live
- package:me.thomastv.rebootupdate
- package:com.dangbeimarket
- cmcc_jiangsu:/ # ls /tmp/Term.apk -alh
- -rw-r--r-- 1 root root 551K 2022-05-28 23:35 /tmp/Term.apk
- cmcc_jiangsu:/ # pm install /tmp/Term.apk
- avc: denied { read } for scontext=u:r:system_server:s0 tcontext=u:object_r:su
- _tmpfs:s0 tclass=file permissive=1
- Success
- cmcc_jiangsu:/ # pm list packages -3
- package:com.xiaodianshi.tv.yst
- package:com.mylejia.store
- package:com.fengyun.live
- package:me.thomastv.rebootupdate
- package:jackpal.androidterm
- package:com.dangbeimarket
- cmcc_jiangsu:/ #
%%%%%
将 APP 安装到指定 UID 用户下
语法格式:
pm install –user USER_ID name.apk示例将当贝市场安装到机主用户下:
- cmcc_jiangsu:/ # pm list users /* 列出用户信息 */
- Users:
- UserInfo{0:机主:13} running
- cmcc_jiangsu:/ # ls /sdcard/Android/data/com.dangbei.tvlauncher/files/Download/zm_fileupload /* 查看安装包在哪里 */
- Term-1.0.65.apk bilibiliTV_1.5.1_dangbei.apk
- Term.apk dangbeishichang1_3.11.9.2_dangbei.apk
- cmcc_jiangsu:/ # pm list packages -3 /* 查看第三方应用列表 */
- package:com.xiaodianshi.tv.yst
- package:com.mylejia.store
- package:com.fengyun.live
- package:me.thomastv.rebootupdate
- package:jackpal.androidterm
- package:com.dangbeimarket
- cmcc_jiangsu:/ # cd /sdcard/Android/data/com.dangbei.tvlauncher/files/Download/zm_fileupload /* 进入安装包目录 */
- cmcc_jiangsu:/sdcard/Android/data/com.dangbei.tvlauncher/files/Download/zm_fileupload # pwd /* 查看当前位置 */
- /sdcard/Android/data/com.dangbei.tvlauncher/files/Download/zm_fileupload
- cmcc_jiangsu:/sdcard/Android/data/com.dangbei.tvlauncher/files/Download/zm_fileupload # pm install --user 0 dangbeishichang1_3.11.9.2_dangbei.apk /* 将指定 apk 安装到 UID 为 0 的用户上 */
- avc: denied { read } for scontext=u:r:system_server:s0 tcontext=u:object_r:sd
- cardfs:s0 tclass=file permissive=1
- Success
- cmcc_jiangsu:/sdcard/Android/data/com.dangbei.tvlauncher/files/Download/zm_fileupload # cd / /* 回到根目录 */
- cmcc_jiangsu:/ # pm list packages -3 /* 查看第三方应用列表 发现多出来 com.dangbeimarket */
- package:com.xiaodianshi.tv.yst
- package:com.mylejia.store
- package:com.fengyun.live
- package:me.thomastv.rebootupdate
- package:jackpal.androidterm
- package:com.dangbeimarket
- package:com.tv.kuaisou
- cmcc_jiangsu:/ #
安装成功:
——————————
控制
%%%%%
清除应用数据
语法如下:
pm clear 包名示例 清除终端模拟器的数据:
- shell@GIONEE_G1605A:/mnt/sdcard $ pm clear jackpal.androidterm
- Success
- shell@GIONEE_G1605A:/mnt/sdcard $
%%%%%
停用/禁用/启用
需要注意的是只有系统应用才可以禁用 第三方应用不可以哦
主要是对 package/包 或 component/组件 进行操作:
- pm enable 包名/组件名 /* 使 package 或 component 可用 */
- pm disenable 包名/组件名 /* 使 package 或 component 不可用 直接就找不到应用了 */
- pm disenable-user 包名/组件名 /* 使 package 或 component 不可用 会显示已停用 */
示例禁用 com.android.webview 包 介绍一个这个包:
WebView 是 Android 系统提供的一个能显示网页的系统控件
是一个特殊的 View 同时也是一个 ViewGroup 可以有很多其她子 View
该控件的作用是用来展示一个 web 页面她使用的内核是 webkit 引擎
在低版本和高版本采用了不同的 webkit 版本内核在版本更新到 4.4 后直接使用了 Chrome 作为内置网页浏览器
- cmcc_jiangsu:/ # pm list packages -d /* 没有禁用包 */
- cmcc_jiangsu:/ # pm list packages -s /* 查看系统包 */
- package:com.iflytek.xiri
- package:com.droidlogic.inputmethod.remote
- package:com.android.providers.media
- package:com.android.externalstorage
- package:com.android.companiondevicemanager
- package:com.android.providers.downloads
- package:com.droidlogic
- package:com.dangbei.tvlauncher
- package:com.android.defcontainer
- package:com.android.pacprocessor
- package:com.android.certinstaller
- package:android
- package:com.android.backupconfirm
- package:com.android.statementservice
- package:com.android.superuser
- package:com.android.providers.settings
- package:com.android.sharedstoragebackup
- package:com.iflytek.xiri2.system
- package:com.android.webview
- package:com.android.se
- package:com.android.inputdevices
- package:com.droidlogic.BluetoothRemote
- package:android.ext.shared
- package:com.android.keychain
- package:android.ext.services
- package:com.android.packageinstaller
- package:com.android.proxyhandler
- package:com.android.inputmethod.latin
- package:com.android.managedprovisioning
- package:com.iflytek.bt.auto
- package:com.android.settings
- package:com.android.vpndialogs
- package:com.android.shell
- package:com.android.location.fused
- package:com.android.systemui
- package:com.android.bluetooth
- package:com.cmcc.mid.softdetector
- cmcc_jiangsu:/ # pm disable-user com.android.webview /* 停用该包 这是一个浏览器控件 */
- Package com.android.webview new state: disabled-user
- cmcc_jiangsu:/ # pm list packages -d /* 查看禁用包 成功禁用 */
- package:com.android.webview
- cmcc_jiangsu:/ # pm disable com.android.bluetooth /* 禁用该包 这是蓝牙 */
- Package com.android.bluetooth new state: disabled
- cmcc_jiangsu:/ # pm list packages -d /* 查看禁用包 蓝牙也被禁了 */
- package:com.android.webview
- package:com.android.bluetooth
- cmcc_jiangsu:/ #
WebView 组件是安卓系统中内置的一款基于 webkit 引擎、展现 web 页面的控件
WebView 能够对 Web 页面进行显示和渲染
网络上或本地可以直接使用 html 文件作布局 更可以和 JavaScript 交互调用
WebView 控件功能强大
除了具有一般 View 的属性和设置外 还可以对 url 请求、页面加载、渲染、页面交互进行强大的处理
- 总的来说 WebView 是用于展示网络请求后的结果
- 比如开发者开发一款 APP 如果想要用她访问网络 但是不想使用手机安装的浏览器
- 而是想在自己 APP 内部打开展示网页 此时就可以使用 WebView 这个组件来展示网页
蓝牙就不需要介绍了吧 懂的都懂
下面示例一下怎么启用应用:
- cmcc_jiangsu:/ # pm enable com.android.webview /* 恢复 WebView 控件 */
- Package com.android.webview new state: enabled
- cmcc_jiangsu:/ # pm list packages -d /* 查看禁用包列表 WebView 已经恢复 */
- package:com.android.bluetooth
- cmcc_jiangsu:/ # pm enable com.android.bluetooth /* 恢复蓝牙 */
- Package com.android.bluetooth new state: enabled
- cmcc_jiangsu:/ # pm list packages -d /* 已经没有禁用包了 */
- cmcc_jiangsu:/ # pm list packages -s
- package:com.iflytek.xiri
- package:com.droidlogic.inputmethod.remote
- package:com.android.providers.media
- package:com.android.externalstorage
- package:com.android.companiondevicemanager
- package:com.android.providers.downloads
- package:com.droidlogic
- package:com.dangbei.tvlauncher
- package:com.android.defcontainer
- package:com.android.pacprocessor
- package:com.android.certinstaller
- package:android
- package:com.android.backupconfirm
- package:com.android.statementservice
- package:com.android.superuser
- package:com.android.providers.settings
- package:com.android.sharedstoragebackup
- package:com.iflytek.xiri2.system
- package:com.android.webview
- package:com.android.se
- package:com.android.inputdevices
- package:com.droidlogic.BluetoothRemote
- package:android.ext.shared
- package:com.android.keychain
- package:android.ext.services
- package:com.android.packageinstaller
- package:com.android.proxyhandler
- package:com.android.inputmethod.latin
- package:com.android.managedprovisioning
- package:com.iflytek.bt.auto
- package:com.android.settings
- package:com.android.vpndialogs
- package:com.android.shell
- package:com.android.location.fused
- package:com.android.systemui
- package:com.android.bluetooth
- package:com.cmcc.mid.softdetector
- cmcc_jiangsu:/ #
%%%%%
隐藏与恢复应用
被隐藏应用在应用管理中变得不可见 桌面图标也会消失:
- pm hide 应用 /* 隐藏 package 或 component */
- pm unhide 应用 /* 将 package 或 component 恢复可见 */
示例隐藏小破站:
- cmcc_jiangsu:/ # pm list packages -3 /* 查看第三方应用 */
- package:com.xiaodianshi.tv.yst
- package:com.mylejia.store
- package:com.fengyun.live
- package:me.thomastv.rebootupdate
- package:jackpal.androidterm
- package:com.dangbeimarket
- cmcc_jiangsu:/ # pm hide com.xiaodianshi.tv.yst /* 隐藏 B 站 TV 版 */
- Package com.xiaodianshi.tv.yst new hidden state: true
- cmcc_jiangsu:/ # pm list packages -3 /* 再次查看第三方应用 发现消失了 */
- package:com.mylejia.store
- package:com.fengyun.live
- package:me.thomastv.rebootupdate
- package:jackpal.androidterm
- package:com.dangbeimarket
- cmcc_jiangsu:/ # pm list packages -d /* 并没有禁用 */
- cmcc_jiangsu:/ # screencap -p /sdcard/sc/1.png /* 截个屏 */
- screencap 3
- screencap start. screen_type: 1
- file path: /sdcard/sc/1.png
- new ScreenCatch ok
- got video+osd data: 1280 x 720
- SkEncodeImage success
- screencap end
- cmcc_jiangsu:/ #
发现桌面图标消失掉了:
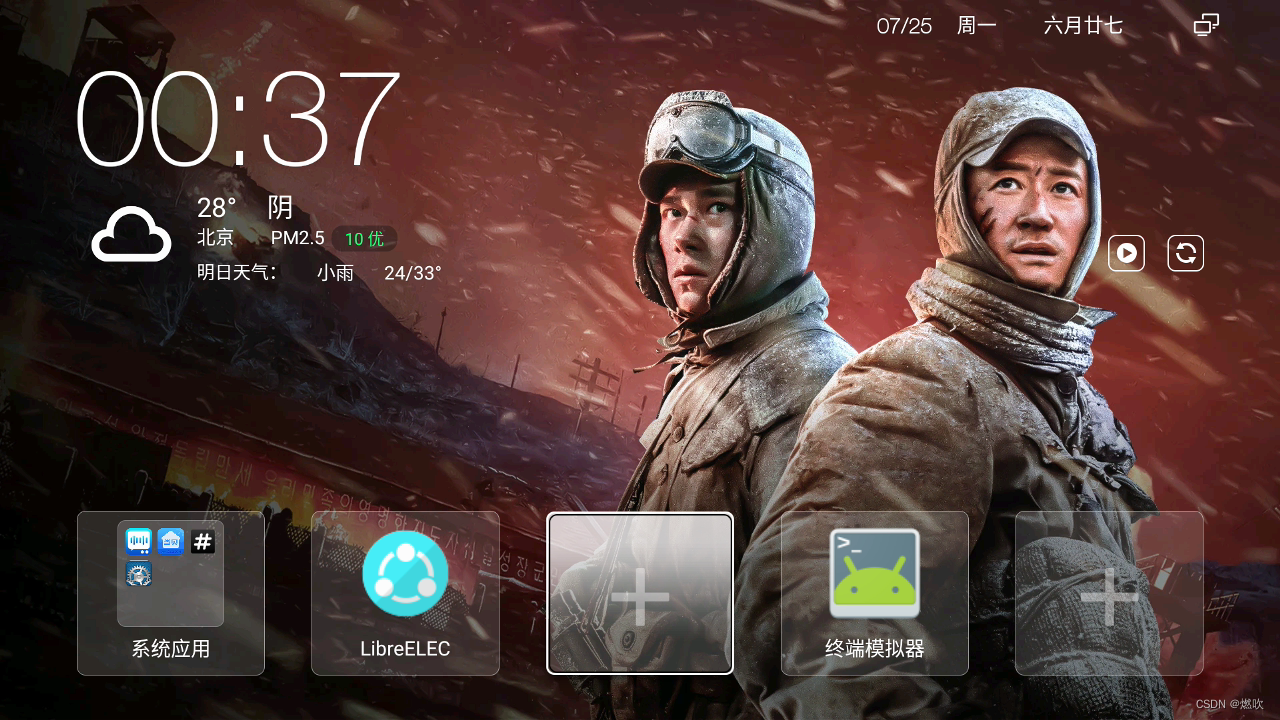
示例恢复小破站:
- cmcc_jiangsu:/ # pm unhide com.xiaodianshi.tv.yst /* 恢复小破站 */
- Package com.xiaodianshi.tv.yst new hidden state: false
- cmcc_jiangsu:/ # pm list packages -3 /* 查看第三方应用 bilibili tv 回来了 */
- package:com.xiaodianshi.tv.yst
- package:com.mylejia.store
- package:com.fengyun.live
- package:me.thomastv.rebootupdate
- package:jackpal.androidterm
- package:com.dangbeimarket
- cmcc_jiangsu:/ # screencap -p /sdcard/sc/1.png /* 截个屏 */
- screencap 3
- screencap start. screen_type: 1
- file path: /sdcard/sc/1.png
- new ScreenCatch ok
- got video+osd data: 1280 x 720
- SkEncodeImage success
- screencap end
- cmcc_jiangsu:/ #
%%%%%
默认安装位置
返回当前应用的安装位置:
pm get-install-localtion会返回 0/1/2 三种值 分别表示 自动/内部/外部
示例:
- cmcc_jiangsu:/ # pm get-install-location
- 0[auto]
- cmcc_jiangsu:/ #
我这边是让系统自动安装
控制应用的默认安装位置
pm set-install-location 位置 /* 更改默认的安装位置 */参数如下:
- 0 自动 让系统决定最好的位置
- 1 内部存储 安装在内部设备上的存储
- 2 外部存储 安装在外部媒体
示例更改安装位置 注意:
只适用于调试 不要瞎搞!
- cmcc_jiangsu:/ # pm set-install-location 2
- cmcc_jiangsu:/ # pm get-install-location
- 2[external]
- cmcc_jiangsu:/ # pm set-install-location 1
- cmcc_jiangsu:/ # pm get-install-location
- 1[internal]
- cmcc_jiangsu:/ # pm set-install-location 0
- cmcc_jiangsu:/ # pm get-install-location
- 0[auto]
- cmcc_jiangsu:/ #


