原理:802.1X协议是一种基于端口的网络接入控制协议,“基于端口的网络接入控制”是指在局域网接入控制设备的端口这一级对所接入的设备进行认证和控制,连接在端口上的用户设备如果能通过认证,就可以访问局域网中的资源;如果不能通过认证。则无法访问局域网中的资源。
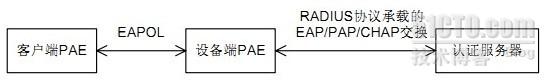
802.1X的体系结构:802.1X系统为典型的C/S体系结构,包括三个实体客户端,设备端,认证服务器端。
802.1X的认证过程:EAP中继方式和EAP终结方式
1. PAE (Port Access Entity,端口访问实体)PAE 是认证机制中负责执行算法和协议操作的实体。设备端 PAE 利用认证服务器对需要接入局域网的客户端执行认证,并根据认证结果相应地控制受控端口的授权/非授权状态。客户端 PAE 负责响应设备端的认证请求,向设备端提交用户的认证信息。客户端 PAE 也可以主动向设备端发送认证请求和下线请求
案例一:EAP终结方式
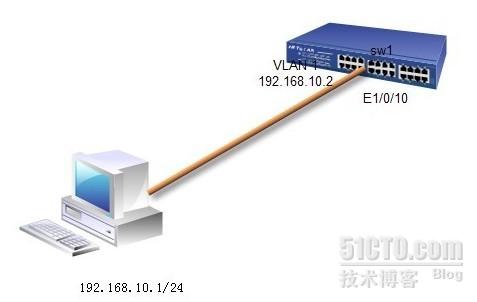
就是在设备端交换机上进行验证,验证的数据库是在交换机上配置,拓扑
实验步骤:
(1)交换机配置
<Quidway>system-v
[Quidway]sys SW1
[SW1]int vlan 1 #在vlan1上配置管理IP
[SW1-Vlan-interface1]
%Apr 2 08:09:31:258 2000 SW1 L2INF/5/VLANIF LINK STATUS CHANGE:- 1 -
Vlan-interface1: is UP
[SW1-Vlan-interface1]ip add 192.168.10.2 24
[SW1-Vlan-interface1]
%Apr 2 08:09:40:788 2000 SW1 IFNET/5/UPDOWN:- 1 -Line protocol on the interface
Vlan-interface1 is UP
[SW1-Vlan-interface1]quit
[SW1]dot1x #开启dot1x在配置模式下开启dot1x
802.1X is enabled globally.
[SW1]int e1/0/10
[SW1-Ethernet1/0/10]dot1x #在连接终端的接口下开启dot1x
802.1X is enabled on port Ethernet1/0/10.
[SW1-Ethernet1/0/10]
[SW1]local-user test1 #配置本地账号
New local user added.
[SW1-luser-test1]password cipher 123456
[SW1-luser-test1]ser
[SW1-luser-test1]service-type lan-access
[SW1-luser-test1]quit
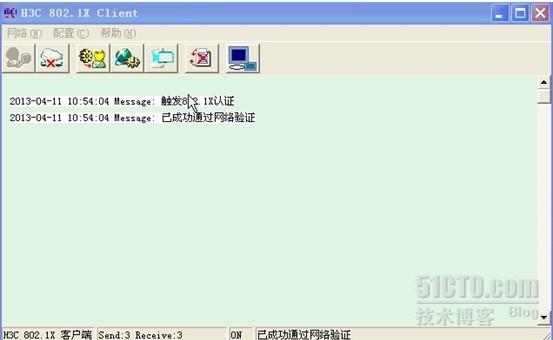
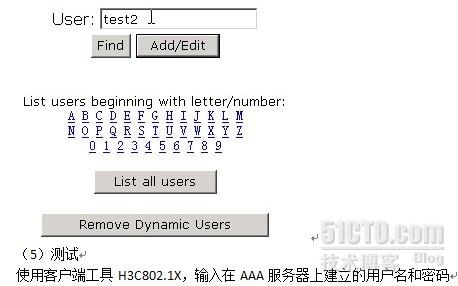
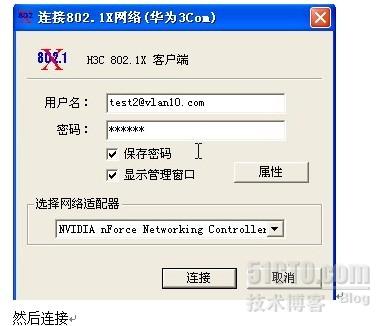
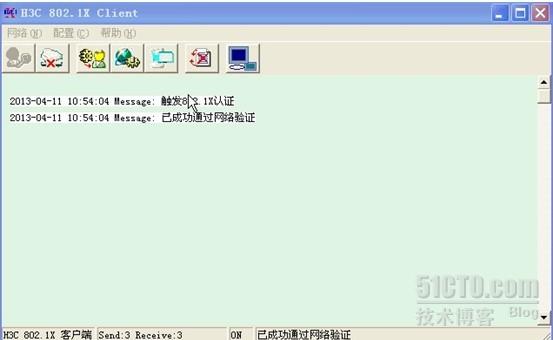
(2)验证:用客户端软件H3C802.1X测试,输入在交换机上建立的帐号和密码
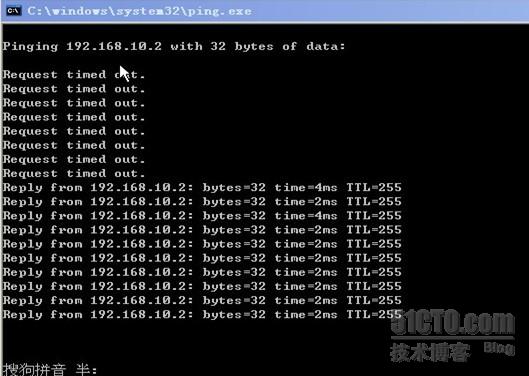
这时PC机再ping交换机的管理IP就通了
案例二:EAP中继方式
这种方式是 IEEE 802.1x 标准规定的,将 EAP 协议承载在其他高层协议中,如 EAP over RADIUS,以便扩展认证协议报文穿越复杂的网络到达认证服务器。一般来说,EAP 中继方式需要 RADIUS 服务器支持 EAP 属性:EAP-Message (值为79)和Message-Authenticator (值为80)。
802.1x的工作机制:
案例:
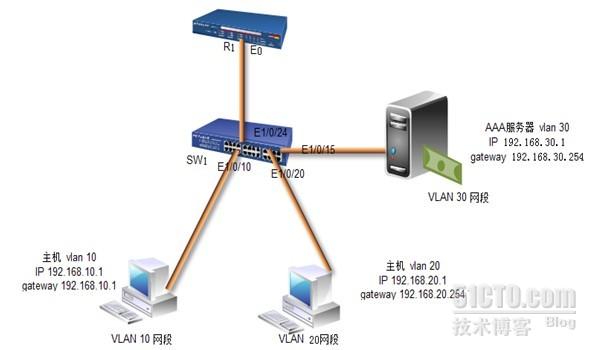
一:组网需求:要求在各端口上对用户接入进行AAA认证,AAA属于VLAN30,主机又分VLAN 10和VLAN 20,VLAN 10属于VLAN10域,VLAN 20属于VLAN20域,本实验实现VLAN 10和VLAN 20能够通过用户认证登录,下面是拓扑图
二:实验步骤
(1)R1的配置
[Router]sys R1
[R1]int e0
[R1-Ethernet0]ip add 192.168.1.254 24 #配置交换机SW1的网关地址,实现交换机和AAA服务器的通讯
%01:03:53: Line protocol ip on the interface Ethernet0 is UP
[R1-Ethernet0]int e0.10 #配置VLAN 10的网关
[R1-Ethernet0.10]vlan-ty dot1q vid 10
[R1-Ethernet0.10]ip add 192.168.10.254 24
[R1-Ethernet0.10]
%01:05:06: Line protocol ip on the interface Ethernet0.10 is UP
[R1-Ethernet0.10]int e0.20 #配置VLAN 20的网关
[R1-Ethernet0.20]vlan-ty dot1q vid 20
[R1-Ethernet0.20]ip add 192.168.20.254 24
[R1-Ethernet0.20]
%01:05:31: Line protocol ip on the interface Ethernet0.20 is UP
[R1-Ethernet0.20]int e0.30 #配置VLAN 30的网关
[R1-Ethernet0.30]vlan-ty dot1q vid 30
[R1-Ethernet0.30]ip add 192.168.30.254 24
[R1-Ethernet0.30]
%01:05:56: Line protocol ip on the interface Ethernet0.30 is UP
[R1-Ethernet0.30]quit
[R1]dis ip rout #查看路由表
Routing Tables:
Destination/Mask Proto Pref Metric Nexthop Interface
127.0.0.0/8 Direct 0 0 127.0.0.1 LoopBack0
127.0.0.1/32 Direct 0 0 127.0.0.1 LoopBack0
192.168.1.0/24 Direct 0 0 192.168.1.254 Ethernet0
192.168.1.254/32 Direct 0 0 127.0.0.1 LoopBack0
192.168.10.0/24 Direct 0 0 192.168.10.254 Ethernet0.10
192.168.10.254/32 Direct 0 0 127.0.0.1 LoopBack0
192.168.20.0/24 Direct 0 0 192.168.20.254 Ethernet0.20
192.168.20.254/32 Direct 0 0 127.0.0.1 LoopBack0
192.168.30.0/24 Direct 0 0 192.168.30.254 Ethernet0.30
192.168.30.254/32 Direct 0 0 127.0.0.1 LoopBack0
[R1]
(2)交换机SW1的配置
<Quidway>system-view
System View: return to User View with Ctrl+Z.
[Quidway]sys SW1
[SW1]int vlan 1 #配置交换机的IP地址
[SW1-Vlan-interface1]
%Apr 2 07:56:34:517 2000 SW1 L2INF/5/VLANIF LINK STATUS CHANGE:- 1 -
Vlan-interface1: is UP
[SW1-Vlan-interface1]ip add 192.168.1.1 24
[SW1-Vlan-interface1]
%Apr 2 07:56:44:698 2000 SW1 IFNET/5/UPDOWN:- 1 -Line protocol on the interface
Vlan-interface1 is UP
[SW1-Vlan-interface1]quit
[SW1]ip route-static 0.0.0.0 0 192.168.1.254 #交换机的默认路由
[SW1]vlan 10 #配置vlan
[SW1-vlan10]port e1/0/10 #添加端口
[SW1-vlan10]vlan 20
[SW1-vlan20]port e1/0/20
[SW1-vlan20]vlan 30
[SW1-vlan30]port e1/0/15
[SW1-vlan30]quit
[SW1]int e1/0/24 #端口24是trunk
[SW1-Ethernet1/0/24]port link-ty
[SW1-Ethernet1/0/24]port link-type trunk
[SW1-Ethernet1/0/24]port tru
[SW1-Ethernet1/0/24]port trunk permit vlan all
Please wait........................................... Done.
[SW1-Ethernet1/0/24]quit
[SW1]radius scheme zxf #配置radius方案
New Radius scheme
[SW1-radius-zxf]primary authentication 192.168.30.1 #主要的认证地址是AAA服务器IP地址
[SW1-radius-zxf]accounting optional #审计可选
[SW1-radius-zxf]key authentication 123456 #认证密钥
[SW1-radius-zxf]server-type standard #服务类型为标准
[SW1-radius-zxf]user-name-format without-domain #用户名格式不带域名,当交换机向AAA服务器发送用户名时,不带域名,
[SW1-radius-zxf]quit
[SW1]dot1x #在交换机上开启dot1x
802.1X is enabled globally.
[SW1]int e1/0/10 #在VLAN 10中相应的端口开启dot1x
[SW1-Ethernet1/0/10]dot1x
802.1X is enabled on port Ethernet1/0/10.
[SW1-Ethernet1/0/10]int e1/0/20 #在VLAN 20中端口开启dot1x
[SW1-Ethernet1/0/20]dot1x
802.1X is enabled on port Ethernet1/0/20.
[SW1-Ethernet1/0/20]quit
[SW1]dis cu #查看配置
#
sysname SW1
#
dot1x
#
radius scheme system
radius scheme zxf
server-type standard
primary authentication 192.168.30.1
accounting optional
key authentication 123456
user-name-format without-domain
#
domain system
#
vlan 1
#
vlan 10
#
vlan 20
#
vlan 30
#
interface Vlan-interface1
ip address 192.168.1.1 255.255.255.0
#
interface Ethernet1/0/9
#
interface Ethernet1/0/10
port access vlan 10
dot1x
interface Ethernet1/0/15
port access vlan 30
interface Ethernet1/0/20
port access vlan 20
dot1x
#
interface Ethernet1/0/24
port link-type trunk
port trunk permit vlan all
ip route-static 0.0.0.0 0.0.0.0 192.168.1.254 preference 60
[SW1]domain vlan10.com #建立域
New Domain added.
[SW1-isp-vlan10.com]radius-scheme zxf #引用域
[SW1-isp-vlan10.com]access-limit enable 10 #限制一个域允许的个数
[SW1-isp-vlan10.com]accounting optional #审计可选
[SW1-isp-vlan10.com]domain vlan20.com
New Domain added.
[SW1-isp-vlan20.com]ra
[SW1-isp-vlan20.com]radius-scheme zxf
[SW1-isp-vlan20.com]access-limit enable 10
[SW1-isp-vlan20.com]accounting optional
[SW1-isp-vlan20.com]quit
[SW1]dis radius scheme #查看radius方案
------------------------------------------------------------------
SchemeName =system Index=0 Type=huawei
Primary Auth IP =127.0.0.1 Port=1645
Primary Acct IP =127.0.0.1 Port=1646
Second Auth IP =0.0.0.0 Port=1812
Second Acct IP =0.0.0.0 Port=1813
Auth Server Encryption Key= Not configured
Acct Server Encryption Key= Not configured
Accounting method = required
Accounting-On packet disable, send times = 15 , interval = 3s
TimeOutValue(in second)=3 RetryTimes=3 RealtimeACCT(in minute)=12
Permitted send realtime PKT failed counts =5
Retry sending times of noresponse acct-stop-PKT =500
nas-ip:Source-IP-address =0.0.0.0
Quiet-interval(min) =5
Username format =without-domain
Data flow unit =Byte
Packet unit =1
unit 1 :
Primary AuthState=active, SecondAuthState=block
Primary Acc State=active, SecondAcc State=block
------------------------------------------------------------------
SchemeName =zxf Index=1 Type=standard
Primary Auth IP =192.168.30.1 Port=1812
Primary Acct IP =0.0.0.0 Port=1813
Second Auth IP =0.0.0.0 Port=1812
Second Acct IP =0.0.0.0 Port=1813
Auth Server Encryption Key= 123456
Acct Server Encryption Key= Not configured
Accounting method = optional
Accounting-On packet disable, send times = 15 , interval = 3s
TimeOutValue(in second)=3 RetryTimes=3 RealtimeACCT(in minute)=12
Permitted send realtime PKT failed counts =5
Retry sending times of noresponse acct-stop-PKT =500
nas-ip:Source-IP-address =0.0.0.0
Quiet-interval(min) =5
Username format =without-domain
Data flow unit =Byte
Packet unit =1
unit 1 :
Primary AuthState=active, SecondAuthState=block
Primary Acc State=block , SecondAcc State=block
------------------------------------------------------------------
Total 2 RADIUS scheme(s). 2 listed
[SW1]
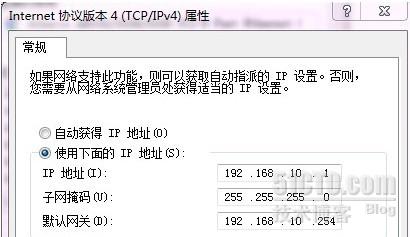
(3)VLAN 10中的一台主机的IP地址
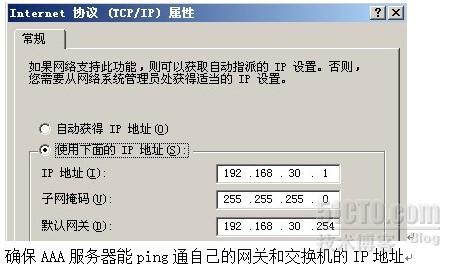
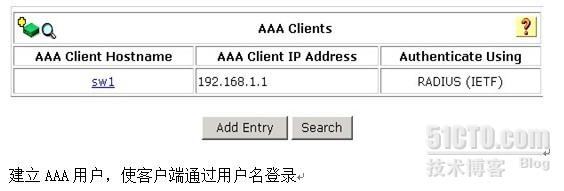
(4)AAA服务器的IP地址
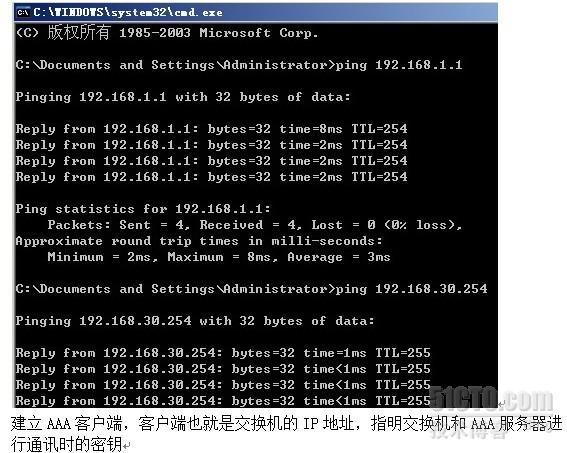
通过认证