- 1Unity学习笔记 关于解决VideoPlayer使用Slider控制视频跳转时滑动条“闪烁跳动”的问题_微信小程序使用slider组件做视频进度条,滑动时出现抖动?
- 2Unity制作场景加载进度条(异步场景加载)_unity场景加载进度条
- 3解决gitlab克隆仓库时url没带上端口号的问题_gitlab external_url添加端口错误
- 4Android图片加载框架:ImageLoader,Volley,Picasso,Glide,Fresco_imageloader glide.with crossfade
- 5eltable 列头不换行 内容自适应_el-table 表头不换行
- 6cesium之流动线纹理实现的两种方式_cesium 流动线
- 7软件测试简单么,发展前景如何?_软件测试真的很简单吗?
- 8esxi虚拟山闪存修改_vmfsl
- 9Echarts设置环形图中心文字_echart 环形图中间文字
- 10springboot+vue结合,后端学习前端(三)(前端拦截器+后端拦截器)未登录访问其他页面,直接进入登陆界面_springboot怎么使用vue页面
k8s 核心网络插件flannel的安装2020-11-23_k8s网络组件flannel下载
赞
踩
flanneld安装部署
最主要的是让pod容器内部能互相联通,形成集群。
CNI 网络插件最主要的功能就是实现pod资源跨宿主机进行通讯
CNI 网络插件
flannel
calico
canal
contiv
OpenContrail
Kube-router
下载flannel: https://github.com/flannel/releases
在jackie21上部署
#cd /opt/src
#wget https:github.com/coreos/flannel/releases/download/v0.11.0/flannel-v0.11.0-linux-amd64.tar.gz
#mkdir /opt/flannel-v0.11.0
#tar xf flannel-v0.11.0-linux-amd-64.tar.gz -C /opt/flannel-v0.11.0/
#ln -s /opt/flannel-v0.11.0/ /opt/flannel
#cd flannel
#mkdir cert
#cd cert/
因为要和apserver通信,所以要配置client证书
cert]# scp jackie200:/opt/certs/ca.pem .
cert]# scp jackie200:/opt/certs/client.pem .
cert]# scp jackie200:/opt/certs/client-key.pem .
编辑环境变量env文件:
flannel ]#
vi /opt/flannel/subnet.env
FLANNEL_NETWORK=172.7.0.0/16
FLANNEL_SUBNET=172.7.21.1/24
FLANNEL_MTU=1500
FLANNEL_IPMASQ=false
- 1
- 2
- 3
- 4
创建启动脚本
jackie21上
vi /opt/flannel/flannel.sh
#!/bin/sh
./flanneld \
--public-ip=10.0.0.21 \
--etcd-endpoints=https://10.0.0.12:2379,https://10.0.0.21:2379,https://10.0.0.22:2379 \
--etcd-keyfile=./cert/client-key.pem \
--etcd-certfile=./cert/client.pem \
--etcd-cafile=./cert/ca.pem \
--iface=eth0 \
--subnet-file=./subnet.env \
--healthz-port=2401
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
chmod u+x flanneld.sh
创建日志存放目录
mkdir -p /data/logs/flanneld
在etcd中增加网络配置信息
cd /opt/etcd
测试使用host-gw模型:
#./etcdctl set /coreos.com/network/config ‘{“Network”: “172.7.0.0/16”, “Backend”: {“Type”: “host-gw”}}’
查看网络模型配置:
#./etcdctl get /coreos.com/network/config
编辑supervisor启动脚本:
vi /etc/supervisord.d/flannel.ini
[program:flanneld-7-21] command=/opt/flannel/flanneld.sh ; the program (relative uses PATH, can take args) numprocs=1 ; number of processes copies to start (def 1) directory=/opt/flannel ; directory to cwd to before exec (def no cwd) autostart=true ; start at supervisord start (default: true) autorestart=true ; retstart at unexpected quit (default: true) startsecs=30 ; number of secs prog must stay running (def. 1) startretries=3 ; max # of serial start failures (default 3) exitcodes=0,2 ; 'expected' exit codes for process (default 0,2) stopsignal=QUIT ; signal used to kill process (default TERM) stopwaitsecs=10 ; max num secs to wait b4 SIGKILL (default 10) user=root ; setuid to this UNIX account to run the program redirect_stderr=true ; redirect proc stderr to stdout (default false) stdout_logfile=/data/logs/flanneld/flanneld.stdout.log ; stderr log path, NONE for none; default AUTO stdout_logfile_maxbytes=64MB ; max # logfile bytes b4 rotation (default 50MB) stdout_logfile_backups=4 ; # of stdout logfile backups (default 10) stdout_capture_maxbytes=1MB ; number of bytes in 'capturemode' (default 0) stdout_events_enabled=false ; emit events on stdout writes (default false)
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
更新supervisor配置:
supervisorctl update
这里需要修改iptables优化SNAT规则,否则在访问时,其他节点记录的是node节点的ip 10.4.7.21,而不是pod集群内部的172.7.21.x,红色部分按需修改
#yum install iptables-services -y
#iptables -t nat -D POSTROUTING -s 172.7.21.0/24 ! -o docker0 -j MASQUERADE
#iptables -t nat -I POSTROUTING -s 172.7.21.0/24 ! -d 172.7.0.0/16 ! -o docker0 -j MASQUERADE
#iptables-save |grep -i postrouting
#iptables-save > /etc/sysconfig/iptables
修改后会影响到docker原本的iptables链的规则,所以需要重启docker服务
#systemctl restart docker
配置vxlan模型:
cd /opt/etcd
./etcdctl set /coreos.com/network/config ‘{“Network”: “172.7.0.0/16”, “Backend”: {“Type”: “vxlan”}}’
重启flanneld:
#supervisorctl restart flanneld-7-21
可以发现多了一块网卡,这块网卡就是vxlan用于隧道通信的虚拟网卡:
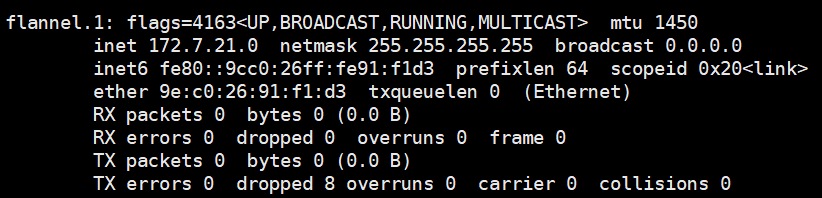
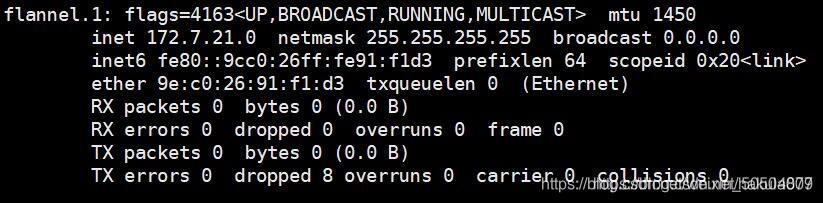
配置vxlan跟host-gw混合模型:
./etcdctl set /coreos.com/network/config ‘{“Network”: “172.7.0.0/16”, “Backend”: {“Type”: “vxlan”,“Directrouting”: true}}’
重启flanneld:
#supervisorctl restart flanneld-7-21



